Operations
Frame structure
All 802.11 wireless frames contain the following fields: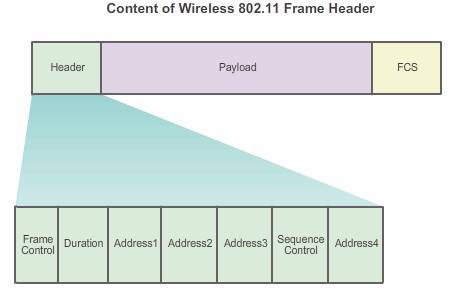
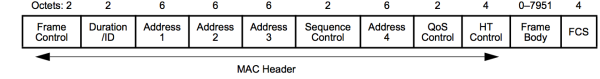
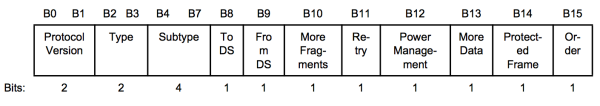
- Frame Control – Identifies the type of wireless frame and contains subfields for protocol version, frame type, address type, power management, and security settings.
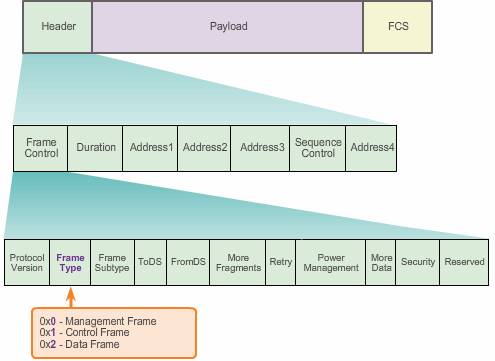
- Frame Type and Frame Subtype – Determines the function of the frame. A wireless frame can either be a control frame, data frame, or a management frame. There are multiple subtype fields for each frame type. Each subtype determines the specific function to perform for its associated frame type.
-
- Management Frame – Used in the maintenance of communication, such as finding, authenticating, and associating with an AP.
- Association request frame – (0x00) Sent from a wireless client, it enables the AP to allocate resources and synchronize. The frame carries information about the wireless connection including supported data rates and SSID of the network to the wireless client that wants to associate. If the request is accepted, the AP reserves memory and establishes an association ID for the device.
- Association response frame – (0x01) Sent from an AP to a wireless client containing the acceptance or rejection to an association request. If it is an acceptance, the frame contains information, such as an association ID and supported data rates.
- Reassociation request frame – (0x02) A device sends a reassociation request when it drops from range of the currently associated AP and finds another AP with a stronger signal. The new AP coordinates the forwarding of any information that may still be contained in the buffer of the previous AP.
- Reassociation response frame – (0x03) Sent from an AP containing the acceptance or rejection to a device reassociation request frame. The frame includes information required for association, such as the association ID and supported data rates.
- Probe request frame – (0x04) Sent from a wireless client when it requires information from another wireless client.
- Probe response frame – (0x05) Sent from an AP containing capability information, such as the supported data rates, after receiving a probe request frame.
- Beacon frame – (0x08) Sent periodically from an AP to announce its presence and provide the SSID and other preconfigured parameters.
- Disassociation frame – (0x0A) Sent from a device wanting to terminate a connection. Allows the AP to relinquish memory allocation and remove the device from the association table.
- Authentication frame – (0x0B) The sending device sends an authentication frame to the AP containing its identity.
- Deauthentication frame – (0x0C) Sent from a wireless client wanting to terminate connection from another wireless client.
Beacons are the only management frame that may regularly be broadcast by an AP. All other probing, authentication, and association frames are used only during the association (or reassociation) process.
- Control Frame – Used to facilitate in the exchange of data frames between wireless clients.
-
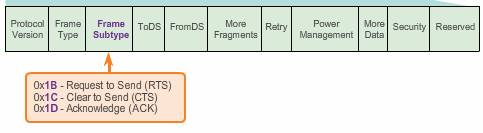
- Request to Send (RTS) frame – The RTS and CTS frames provide an optional collision reduction scheme for APs with hidden wireless clients. A wireless client sends an RTS frame as the first step in the two-way handshake, which is required before sending data frames.
- Clear to Send (CTS) frame – A wireless AP responds to an RTS frame with a CTS frame. It provides clearance for the requesting wireless client to send a data frame. The CTS contributes to collision control management by including a time value. This time delay minimizes the chance that other wireless clients will transmit while the requesting client transmits.
- Data Frame – Used to carry the payload information such as web pages and files.
- Management Frame – Used in the maintenance of communication, such as finding, authenticating, and associating with an AP.
- ToDS and FromDS – Indicates whether the frame is going to or exiting from the DS(Distribution System), and is only used in data frames of wireless clients associated with an AP. FromDS indicates an associated AP client that the data is existing an DS system.
- More Fragments – Indicates whether more fragments of the frame, either data or management type, are to follow.
- Retry – Indicates whether or not the frame, for either data or management frame types, is being retransmitted.
- Power Management – Indicates whether the sending device is in active mode or power-save mode.
- More Data – Indicates to a device in power-save mode that the AP has more frames to send. It is also used for APs to indicate that additional broadcast/multicast frames are to follow.
- Security – Indicates whether encryption and authentication are used in the frame. It can be set for all data frames and management frames, which have the subtype set to authentication.
- Frame Type and Frame Subtype – Determines the function of the frame. A wireless frame can either be a control frame, data frame, or a management frame. There are multiple subtype fields for each frame type. Each subtype determines the specific function to perform for its associated frame type.
- Duration – Typically used to indicate the remaining duration needed to receive the next frame transmission.
- Address1 – Usually contains the MAC address of the receiving wireless device or AP.
- Address2 – Usually contains the MAC address of the transmitting wireless device or AP.
- Address3 – Sometimes contains the MAC address of the destination, such as the router interface (default gateway) to which the AP is attached.
- Sequence Control – Contains the Sequence Number and the Fragment Number subfields. The Sequence Number indicates the sequence number of each frame. The Fragment Number indicates the number of each frame sent of a fragmented frame.
- Address4 – Usually missing because it is used only in ad hoc mode.
- Payload – Contains the data for transmission.
- FCS – Frame Check Sequence; used for Layer 2 error control.
Operation
collision avoidance
Wi-Fi systems are half-duplex, shared media configurations; therefore, wireless clients can transmit and receive on the same radio channel.
This creates a problem because a wireless client cannot hear while it is sending; thus, making it impossible to detect a collision. To address this problem, the IEEE developed an additional collision avoidance mechanism called the Distributed Coordination Function (DCF). Using DCF, a wireless client transmits only if the channel is clear. All transmissions are acknowledged; therefore, if a wireless client does not receive an acknowledgment, it assumes a collision occurred and retries after a random waiting interval.
Client and AP association stage
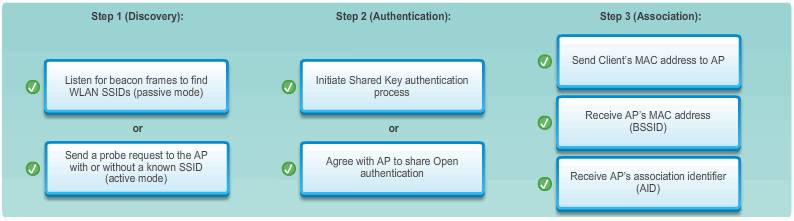
Management frames are used by wireless devices to complete the following three-stage process:
- Discover new wireless AP.
- Authenticate with AP.
- Associate with AP.
To associate, a wireless client and an AP must agree on specific parameters. Parameters must be configured on the AP and subsequently on the client to enable the negotiation of these processes.
Common configurable wireless parameters include:
- SSID – An SSID is a unique identifier that wireless clients use to distinguish between multiple wireless networks in the same vicinity. The SSID name appears in the list of available wireless network on a client. Depending on the network configuration, several APs on a network can share an SSID. Names are usually 2 to 32 characters long.
- Password – Required from the wireless client to authenticate to the AP. A password is sometimes called the security key. It prevents intruders and other unwanted users from accessing the wireless network.
- Network mode – Refers to the 802.11a/b/g/n/ac/ad WLAN standards. APs and wireless routers can operate in a Mixed mode meaning that it can simultaneously use multiple standards.
- Security mode – Refers to the security parameter settings, such as WEP, WPA, or WPA2. Always enable the highest security level supported.
- Channel settings – Refers to the frequency bands being used to transmit wireless data. Wireless routers and AP can choose the channel setting or it can be set manually if there is interference with another AP or wireless device.Notice that the Linksys EA6500 support 2.4GHZ and 5Ghz, does not support 802.11ad.
AP modes:
Wireless clients connect to the AP using a scanning (probing) process. This process can be:
- Passive mode – The AP openly advertises its service by periodically sending broadcast beacon frames containing the SSID, supported standards, and security settings. The primary purpose of the beacon is to allow wireless clients to learn which networks and APs are available in a given area, thereby allowing them to choose which network and AP to use.
- Active mode – Wireless clients must know the name of the SSID. The wireless client initiates the process by broadcasting a probe request frame on multiple channels. The probe request includes the SSID name and standards supported. Active mode may be required if an AP or wireless router is configured to not broadcast beacon frames.
A wireless client could also send a probe request without an SSID name to discover nearby WLAN networks. APs configured to broadcast beacon frames would respond to the wireless client with a probe response and provide the SSID name. APs with the broadcast SSID feature disabled do not respond.
Authentication
The 802.11 standard was originally developed with two authentication mechanisms:
- Open authentication – Fundamentally a NULL authentication where the wireless client says “authenticate me” and the AP responds with “yes”. Open authentication provides wireless connectivity to any wireless device and should only be used in situations where security is of no concern.
- Shared key authentication – Technique is based on a key that is pre-shared between the client and the AP.
In most shared key authentication installations, the exchange is as follows:
1. The wireless client sends an authentication frame to the AP.
2. The AP responds with a challenge text to the client.
3. The client encrypts the message using its shared key and returns the encrypted text back to the AP.
4. The AP then decrypts the encrypted text using its shared key.
5. If the decrypted text matches the challenge text, the AP authenticates the client. If the messages do not match, the wireless client is not authenticated and wireless access is denied.
After a wireless client has been authenticated, the AP proceeds to the association stage. The association stage finalizes settings and establishes the data link between the wireless client and the AP.
As part of this stage:
- The wireless client forwards an Association Request frame that includes its MAC address.
- The AP responds with an Associate Response that includes the AP BSSID, which is the AP MAC address.
- The AP maps a logical port known as the association identifier (AID) to the wireless client. The AID is equivalent to a port on a switch and allows the infrastructure switch to keep track of frames destined for the wireless client to be forwarded.
After a wireless client has associated with an AP, traffic is now able to flow between the client and the AP.
Channel management
A common practice is for frequencies to be allocated as ranges. Such ranges are then split into smaller ranges called channels.
If the demand for a specific channel is too high, that channel is likely to become oversaturated. The saturation of the wireless medium degrades the quality of the communication. Over the years, a number of techniques have been created to improve wireless communication and alleviate saturation. The techniques listed below mitigate channel saturation by using the channels in a more efficient way:
- Direct-sequence spread spectrum (DSSS) – DSSS is a spread-spectrum modulation technique. Spread-spectrum is designed to spread a signal over a larger frequency band making it more resistant to interference. With DSSS the signal is multiplied by a “crafted noise” known as a spreading code. Because the receiver knows about the spreading code and when it was added, it can mathematically remove it and re-construct the original signal. In effect, this creates redundancy in the transmitted signal in an effort to counter quality loss in the wireless medium.
DSSS is used by 802.11b. Also used by cordless phones operating in the 900 MHz, 2.4 GHz, 5.8 GHz bands, CDMA cellular, and GPS networks.
- Frequency-hopping spread spectrum (FHSS) – FHSS also relies on spread-spectrum methods to communicate. It is similar to DSSS but transmits radio signals by rapidly switching a carrier signal among many frequency channels. With the FHSS, sender and receiver must be synchronized to “know” which channel to jump. This channel hopping process allows for a more efficient usage of the channels, decreasing channel congestion. Walkie-talkies and 900 MHz cordless phones also use FHSS, and Bluetooth uses a variation of FHSS. FHSS is also used by the original 802.11 standard.
- Orthogonal frequency-division multiplexing (OFDM) – OFDM is a subset of frequency division multiplexing in which a single channel utilizes multiple sub-channels on adjacent frequencies. Sub-channels in an OFDM system are precisely orthogonal to one another which allow the sub-channels to overlap without interfering. As a result, OFDM systems are able to maximize spectral efficiency without causing adjacent channel interference. In effect, this makes it easier for a receiving station to “hear” the signal. Because OFDM uses sub-channels, channel usage is very efficient. OFDM is used by a number of communication systems including 802.11a/g/n/ac.
A best practice for WLANs requiring multiple APs is to use non-overlapping channels. If there are three adjacent APs, use channels 1, 6, and 11. If there are just two, select any two that are five channels apart, such as channels 5 and 10.
802.11n can also use channel bonding, which combines two 20 MHz channel into on 40 MHz channels. Channel bonding increase throughput by using two channels at one time to deliver data.
Planning WLAN deployment
The number of users a WLAN can support is not a straightforward calculation. The number or users depends on
- the geographical layout of the facility, including the number of bodies and devices that can fit in a space
- the data rates users expect
- the use of non-overlapping channels by multiple APs in an ESS, and transmit power settings
some additional recommendations:
- If APs are to use existing wiring or if there are locations where APs cannot be placed, note these locations on the map.
- Position APs above obstructions.
- Position APs vertically near the ceiling in the center of each coverage area, if possible.
- Position APs in locations where users are expected to be. For example, conference rooms are typically a better location for APs than a hallway.
- Always consult the specifications for the AP when planning for coverage areas.
BSAs represent the coverage area provided by a single channel.
An ESS should have 10 to 15 percent overlap between BSAs in an ESS. With a 15 percent overlap between BSAs, an SSID, and non-overlapping channels (i.e., one cell on channel 1 and the other on channel 6), roaming capability can be created.