Configure Standard numbering ACLs
1.Syntax of the standard numbering ACL command:
Router(config)# access-list access-list-number { deny | permit | remark } source [ source-wildcard ][ log ]
- Access-list-number: 1-99 or 1300-1999
- Deny: denies access if the conditions are matched.
- Permit: permit access if the conditions are matched.
- Remark: add a remark about this entry to make the list easier to understand for later use or by other staff.
- Source: the network address or keyword.
- Source-wildcard: (optional)32-bit wildcard mask to be applied to the source.
- Log : (optional) Causes an informational logging message about the packet that matches the criteria( the level of the messages logged to the console is controlled by the
Logging consolecommand). The message includes the ACL number, whether the packet was permitted or denied, the source address, and the number of packets. The message is generated for the first packet that matches, and then a 5 minuts intervals, including the number of packets permitted or denied in the prior 5 minutes interval.
2. Remove and check the list.
To remove the ACL, the global configuration no access-list command is used. Issuing the show access-list command.
3. Internal logic:
- Host statement can always be configured before range statement, this can eliminate conflict issues.
Eg: if you enter:
r1(config)#access-list 3 deny 192.168.10.0 0.0.0.255
r1(config)#access-list 3 permit host 192.168.10.10
The system will tell you that the there is a conflict, because the first entry have denied the network, and the host specified in the second entry is in the network which been denied in the first entry. It will work fine like this:
r1(config)#access-list 3 permit host 192.168.10.10
r1(config)#access-list 3 deny 192.168.10.0 0.0.0.255
Note: The order in which standard ACEs are entered may not be the order that they are stored, displayed, or processed by the router.
- Notice that the statements are grouped into two sections, host statements followed by range statements. The sequence number indicates the order that the statement was entered, not the order the statement will be processed.
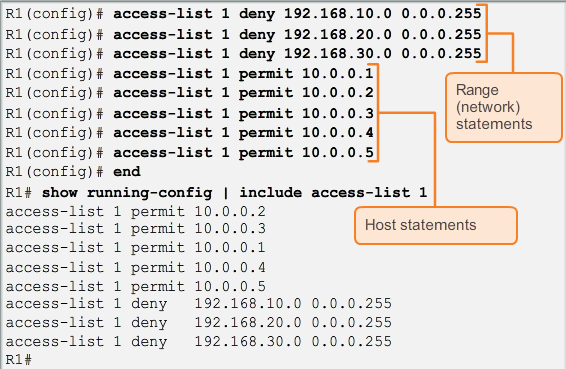
To check the processing order, We will use the show access-lists command to understand the logic behind this.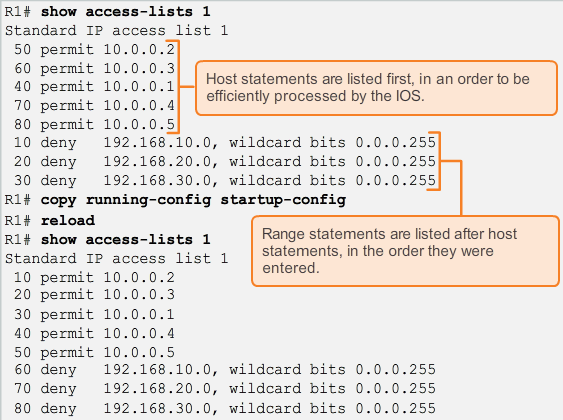 The IOS puts host statements in an order using a special hashing function. The resulting order optimizes the search for a host ACL entry.When inserting a new ACL statement, the sequence number will only affect the location of a range statement in the list. Host statements will always be put in order using the hashing function.
The IOS puts host statements in an order using a special hashing function. The resulting order optimizes the search for a host ACL entry.When inserting a new ACL statement, the sequence number will only affect the location of a range statement in the list. Host statements will always be put in order using the hashing function.
Note: The hashing function is only applied to host statements in an IPv4 standard access list. The algorithm is not used for IPv4 extended ACLs or IPv6 ACLs. This is because extended and IPv6 ACLs filter on more than just a single source address.
4. Applying to interfaces:
Router(config-if)# ip access-group { access-list-number | access-list-name } { in | out }
To remove an ACL from an interface, first enter the no ip access-group command on the interface, and then enter the global no access-list command to remove the entire ACL.
Configure Standard Named ACLs
Step 1. Starting from the global configuration mode, use the ip access-list command to create a named ACL. ACL names are alphanumeric, case sensitive, and must be unique. The ip access-list standard name is used to create a standard named ACL, whereas the command ip access-list extended name is for an extended access list. After entering the command, the router is in named standard ACL configuration mode as indicated by the prompt.
R1(config)#ip access-list [standard|extended] name
Note: Numbered ACLs use the global configuration command access-list whereas named IPv4 ACLs use the ip access-list command.
Step 2. From the named ACL configuration mode, use permit or deny statements to specify one or more conditions for determining whether a packet is forwarded or dropped.
R1(config-std-nacl)#[permit|deny|remark] {source_address [source _wildcard]} [log]
Step 3. Apply the ACL to an interface using the ip access-group command. Specify if the ACL should be applied to packets as they enter into the interface (in) or applied to packets as they exit the interface (out).
R1(config-if)#ip access-group name [in|out]
Capitalizing ACL names is not required, but makes them stand out when viewing the running-config output.
Commenting ACLs
Syntax: access-list access-list_number remark remark
The remark keywords can before or after the statement, but it’s good to keep the consistency.