Basic
Categorize networks based on the number of devices serviced:
- Small network – Provides services for up to 200 devices.
- Medium-sized network – Provides services for 200 to 1000 devices.
- Large network – Provides services for 1000+ devices.
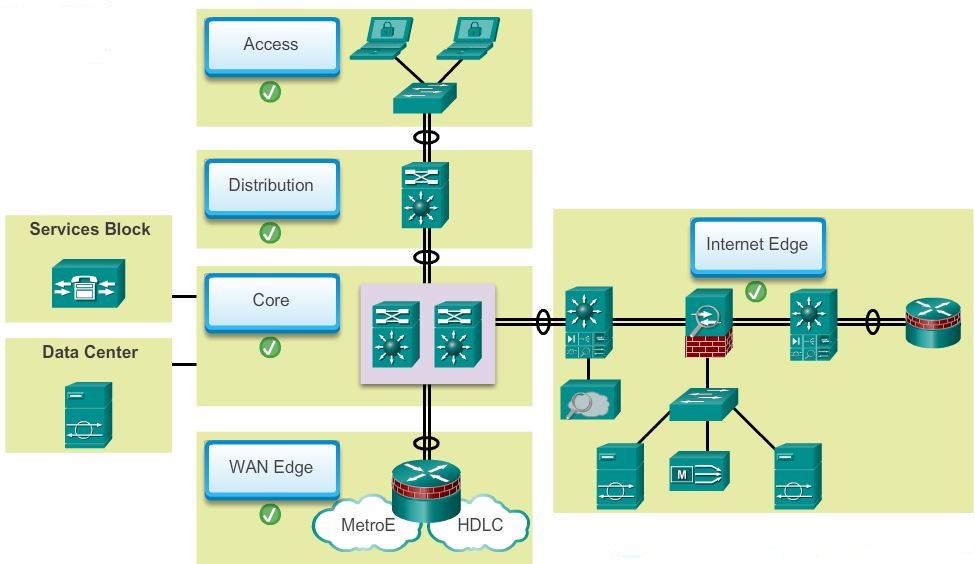
A typical enterprise hierarchical LAN campus network design includes the following three layers:
- Distribution layer – Provides policy-based connectivity and controls the boundary between the access and core layers.
the distribution layer is the boundary between the Layer 2 domains and the Layer 3 routed network.The distribution layer device is the focal point in the wiring closets. Either a router or a multilayer switch is used to segment workgroups and isolate network problems in a campus environment.A distribution layer switch may provide upstream services for many access layer switches.The distribution layer can provide:- Aggregation of LAN or WAN links
- Policy-based security in the form of access control lists (ACLs) and filtering
- Routing services between LANs and VLANs and between routing domains (e.g., EIGRP to OSPF)
- Redundancy and load balancing
- A boundary for route aggregation and summarization configured on interfaces toward the core layer
- Broadcast domain control, because routers or multilayer switches do not forward broadcasts. The device acts as the demarcation point between broadcast domains
- Access layer – Provides workgroup/user access to the network.
The access layer serves a number of functions including:- Layer 2 switching
- High availability
- Port security
- QoS classification and marking and trust boundaries
- Address Resolution Protocol (ARP) inspection
- VLAN Access Control List (VACL)
- Spanning tree
- Power over Ethernet (PoE) and auxiliary VLANs for VoIP
- Core layer – Provides fast transport between distribution switches within the enterprise campus.
The core layer consists of high-speed network devices such as the Cisco Catalyst 6500 or 6800. These are designed to switch packets as fast as possible and interconnect multiple campus components, such as distribution modules, service modules, the data center, and the WAN edge.The core layer is critical for interconnectivity between distribution layer devices; for example, interconnecting the distribution block to the WAN and Internet edge. The core should be highly available and redundant. The core aggregates the traffic from all the distribution layer devices, so it must be capable of forwarding large amounts of data quickly.Considerations at the core later include:- Providing high-speed switching (i.e., fast transport)
- Providing reliability and fault tolerance
- Scaling by using faster, and not more, equipment
- Avoiding CPU-intensive packet manipulation caused by security, inspection, quality of service (QoS) classification, or other processes
The benefit of dividing a flat network into smaller, more manageable blocks is that local traffic remains local. Only traffic that is destined for other networks is moved to a higher layer.
Note: There are no absolute rules for the way a campus network is physically built. While it is true that many campus networks are constructed using three physical tiers of switches, this is not a strict requirement. In a smaller campus, the network might have two tiers of switches in which the core and distribution elements are combined in one physical switch. This is referred to as a collapsed core design.
A “collapsed core” is when the distribution layer and core layer functions are implemented by a single device. The primary motivation for the collapsed core design is reducing network cost, while maintaining most of the benefits of the three-tier hierarchical model.
Modular Network
A modular network design separates the network into various functional network modules, each targeting a specific place or purpose in the network. The modules represent areas that have different physical or logical connectivity. They designate where different functions occur in the network. Using a modular approach has several benefits, including:
- Failures that occur within a module can be isolated from the remainder of the network, providing for simpler problem detection and higher overall system availability.
- Network changes, upgrades, or the introduction of new services can be made in a controlled and staged fashion, allowing greater flexibility in the maintenance and operation of the campus network.
- When a specific module no longer has sufficient capacity or is missing a new function or service, it can be updated or replaced by another module that has the same structural role in the overall hierarchical design.
- Security can be implemented on a modular basis allowing for more granular security control.
Basic network modules include:
- Access-distribution – Also called the distribution block, this is the most familiar element and fundamental component of a campus design.
- Services – This is a generic block used to identify services such as centralized Lightweight Access Point Protocol (LWAPP) wireless controllers, unified communications services, policy gateways, and more.
- Data center – Originally called the server farm. This block is responsible for managing and maintaining many data systems that are vital to modern business operations. Employees, partners, and customers rely on data and resources in the data center to effectively create, collaborate, and interact.
- Enterprise Edge – Consists of the Internet Edge and the WAN Edge. These blocks offer connectivity to voice, video, and data services outside the enterprise.
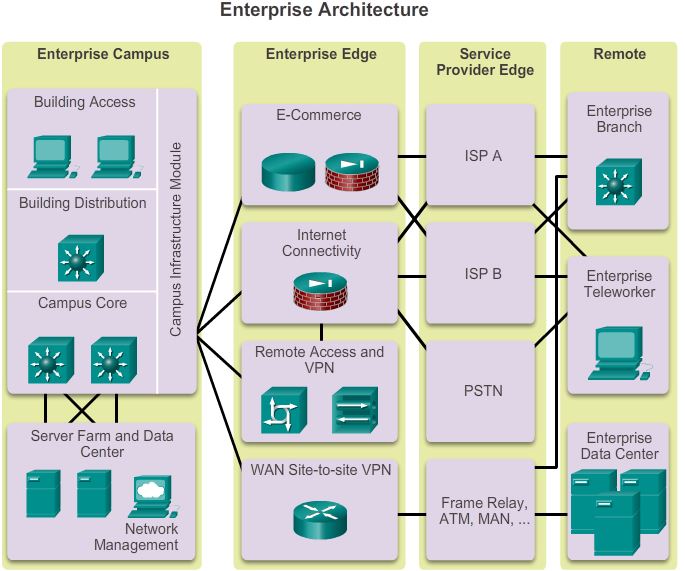
The Cisco Enterprise Architecture model separates the enterprise network into functional areas that are referred to as modules. The modularity that is built into the architecture allows flexibility in network design and facilitates implementation and troubleshooting.
As shown in the figure, the following are the primary Cisco Enterprise Architecture modules:
- Enterprise Edge
The enterprise edge module provides connectivity for voice, video, and data services outside the enterprise. This module often functions as a liaison between the enterprise campus module and the other modules.The enterprise edge module consists of the following submodules:- E-commerce networks and servers – The e-commerce submodule enables enterprises to support e-commerce applications through the Internet. It uses the high availability designs of the data center module. Devices located in the e-commerce submodule include web, application, and database servers, firewall and firewall routers, and network intrusion prevention systems (IPS).
- Internet connectivity and demilitarized zone (DMZ) – The Internet submodule of the enterprise edge provides internal users with secure connectivity to Internet services such as public servers, email, and DNS. Connectivity to one or several Internet Service Providers (ISP) is also provided. Components of this submodule include firewall and firewall routers, Internet edge routers, FTP and HTTP servers, SMTP relay servers, and DNS servers.
- Remote Access and VPN – The VPN/remote access submodule of the enterprise edge provides remote-access termination services, including authentication for remote users and sites. Components of this submodule include firewalls, dial-in access concentrators, Cisco Adaptive Security Appliances (ASA), and network Intrusion Prevention System (IPS) appliances.
- WAN – The WAN submodule uses various WAN technologies for routing traffic between remote sites and the central site. Enterprise WAN links include technologies such as Multiprotocol Label Switching (MPLS), Metro Ethernet, leased lines, Synchronous Optical Network (SONET) and Synchronous Digital Hierarchy (SDH), PPP, Frame Relay, ATM, cable, digital subscriber line (DSL), and wireless.
- Enterprise Campus
A campus network is a building or group of buildings connected into one enterprise network that consists of many LANs. A campus is generally limited to a fixed geographic area, but it can span several neighboring buildings, for example, an industrial complex or business park environment. Regional offices, SOHOs, and mobile workers may need to connect to the central campus for data and information.The enterprise campus module describes the recommended methods to create a scalable network, while addressing the needs of campus-style business operations. The architecture is modular and can easily expand to include additional campus buildings or floors as the enterprise grows.The enterprise campus module consists of the following submodules:- Building access
- Building distribution
- Campus core
- Data center: A high-capacity, centralized data center module can provide internal server resources to users. The data center module typically also supports network management services for the enterprise, including monitoring, logging, troubleshooting, and other common management features from end to end. The data center submodule typically contains internal email and corporate servers that provide application, file, print, email, and Domain Name System (DNS) services to internal users.
Together these submodules:
- Provide high availability through a resilient hierarchical network design.
- Integrate IP communications, mobility, and advanced security.
- Utilize multicast traffic and QoS to optimize network traffic.
- Provide increased security and flexibility using access management, VLANs and IPSec VPNs.
The enterprise campus module architecture provides the enterprise with high availability through a resilient multilayer design, redundant hardware and software features, and automatic procedures for reconfiguring network paths when failures occur. Integrated security protects against and mitigates the impact of worms, viruses, and other attacks on the network, even at the switch port level.
- Service Provider Edge
Enterprises use Service Providers (SPs) to link to other sites. As shown in Figure, the SP edge module can include:- Internet Service Providers (ISPs)
- WAN services such as Frame Relay, ATM, and MAN
- Public Switched Telephone Network (PSTN) services
The SP edge provides connectivity between the enterprise campus module to the remote enterprise data center, enterprise branch, and enterprise teleworker modules.
The SP edge module:
- Spans across large geographic areas in a cost effective manner
- Converges voice, video, and data services over a single IP communications network
- Supports QoS and service level agreements
- Supports security using VPNs (IPsec / MPLS) over Layer 2 and Layer 3 WANs
When acquiring Internet services from an ISP, redundancy or failover should be considered. Redundant connections to a single ISP can include:

- Single-homed – A single connection to an ISP
- Dual-homed – Two or more connections to a single ISP
Alternatively, it is possible to set up redundancy using multiple ISPs. Options for connecting to multiple ISPs include:
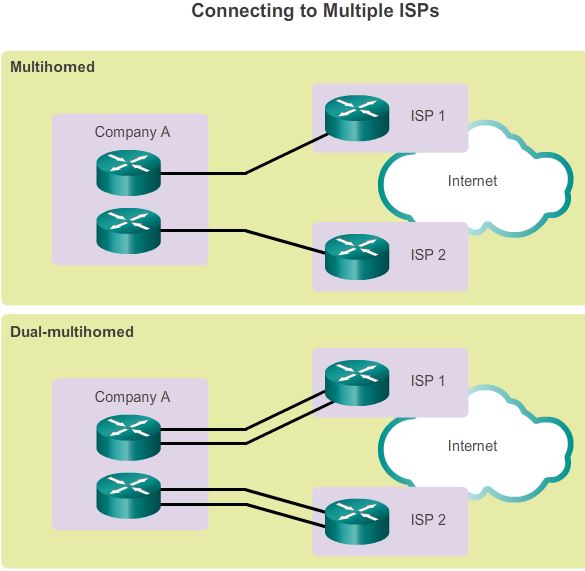
- Multihomed – Connections to two or more ISPs
- Dual-multihomed – Multiple connections to two or more ISPs.
Connected to the Service Provider Edge are additional modules including:- Enterprise Data Center
- Enterprise Branch
- Enterprise Teleworker
-
The remote functional area is responsible for remote connectivity options and includes several modules:
Enterprise Branch
The enterprise branch module includes remote branches that allow employees to work at non-campus locations. These locations are typically responsible for providing security, telephony, and mobility options to employees, as well as general connectivity into the campus network and the different components located inside the enterprise campus. The enterprise branch module allows enterprises to extend head-office applications and services, such as security, Cisco Unified Communications, and advanced application performance, to the remote branches. The edge device connecting the remote site to the central site varies depending on the needs and size of the site. Large remote sites may use high-end Cisco Catalyst switches, while smaller sites may use an ISR G2 router. These remote sites rely on the SP edge to provide services and applications from the main site. In the figure the enterprise branch module connects to the enterprise campus site primarily using a WAN link; however, it also has an Internet link as a backup. The Internet link uses site-to-site IPsec VPN technology to encrypt corporate data.
Enterprise Teleworker
The enterprise teleworker module is responsible for providing connectivity for workers who operate out of different geographically dispersed locations, including home offices, hotels or customer/client sites. The teleworker module recommends that mobile users connect to the Internet using the services of a local ISP, such as cable modem or DSL. VPN services can then be used to secure communications between the mobile worker and central campus. Integrated security- and identity-based networking services enable the enterprise to extend campus security policies to the teleworker. Staff can securely log into the network over the VPN and gain access to authorized applications and services from a single cost-effective platform.
Enterprise Data Center
The enterprise data center module is a data center with all of the same functional options as a campus data center, but exists at a remote location. This provides an added layer of security as the offsite data center can provide disaster recovery and business continuance services for the enterprise. High-end switches such as the Cisco Nexus series switch use fast WAN services such as Metro Ethernet (MetroE) to connect the enterprise campus to the remote enterprise data center. Redundant data centers provide backup using synchronous and asynchronous data and application replication. Additionally, the network and devices offer server and application load balancing to maximize performance. This solution allows the enterprise to scale without major changes to the infrastructure.