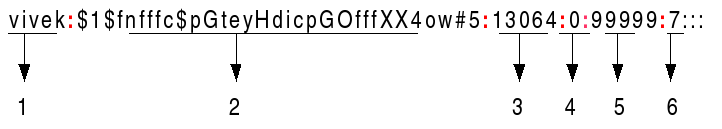Navigate file system
ls command
most common for me ls -flh
show hidden files, in list, with easy ready size format.
File management tasks
create directories, copy, move files, delete files and directories.
- mkdir: make directory.
- mv: move file or directory.
- cp: copy file or directory.
To copy a directory full of files in Linux, you must tell the command that the copy will be recursive (involve files and subdirectories too) by using the –R option. - -i option: to prompt if overwrite the target file if the source and target file are same name.
- rm : delete file. -i option to confirm, -f option to force delete file quickly.
- rmdir: delete a directory with no file in it.
To delete directory with files and subdirectoris, use rm with -R option.
Find files
1. Locate command:
Based on a premade database (/var/lib/mlocate/mlocate.db) which is updated daily. Searching speed is fast.
To manual update it, use command updatedb
2. Find command
It searches the directory tree recursively. Slower but more versatile.
Syntax: find <start directory> -criteria <what to find>
example: find /etc -name inittab
Support wildcard in the name. example: find all the php files.
# find . -type f -name "*.php" ./tecmint.php ./login.php ./index.php
Criteria:
- -iname: ignore case.
# find /home -iname tecmint.txt ./tecmint.txt ./Tecmint.txt
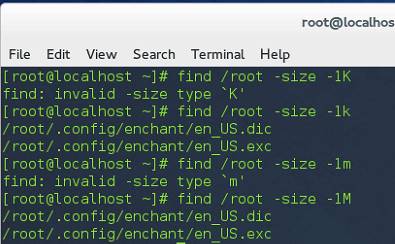
- -size : find files that are bigger than a size, the k should be lower case in fedora 20; if use Megabyte, should be capital M.
find /var -size +4096k
- k: Kilobytes
- M: Megabytes
- G: Gigabytes
- b: 512-byte blocks
- +: bigger than
- -: smaller than
- -type: find directories by d argument ; find files by f argument.
find /boot -type - -empty: find empty files or directories.
# find /tmp -type f -empty
# find /tmp -type d -empty
- To find all hidden files, use below command.
# find /tmp -type f -name ".*"
- To find all the files which are accessed in last 1 hour.
# find / -amin -60
- To find all the files which are accessed 50 days back.
# find / -atime 50
- To find all the files which are modified in last 1 hour.
# find / -mmin -60
- To find all the files which are modified more than 50 days back and less than 100 days.
# find / -mtime +50 –mtime -100
- To find all the files which are changed in last 1 hour.
# find / -cmin -60
- -perm: find the files according to the permission, find file with 777 permission.
# find / -type f -perm 777
without permissions: add ! in front of -perm
# find / -type f ! -perm 777
- Find executable file:
# find / -perm /a=x
- To find all files that belongs to user Bella under /home directory.
# find /home -user Bella
- To find all files that belongs to group Developer under /home directory.
# find /home -group developer
- Find the files with permission 777 and change into 644 in directory /root
# find /root -type f -perm 0777 -print -exec chmod 644 {} \; - -print : show the affected file of this command.in this example, In the first command line, I did not add the -print option, the find and chmod just did it silently.
Then, in the second command line, I find and chmod back to the orignal state. In the third command line, I issued the same command as the first command line but add the option -print, and the command showed the affected files by this command.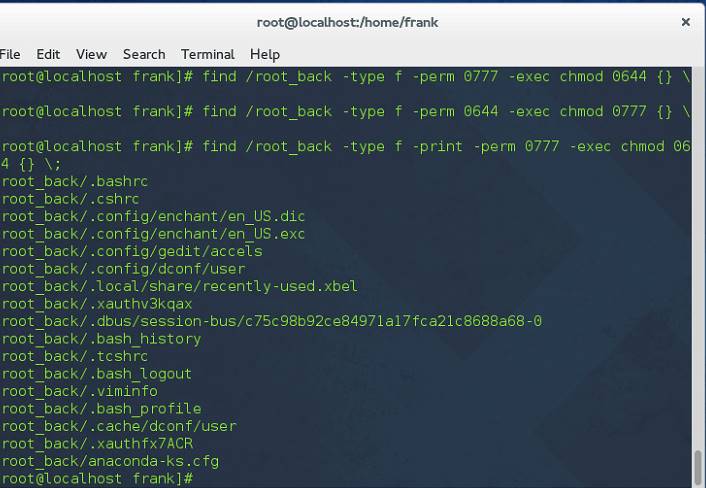
Then we can verify it: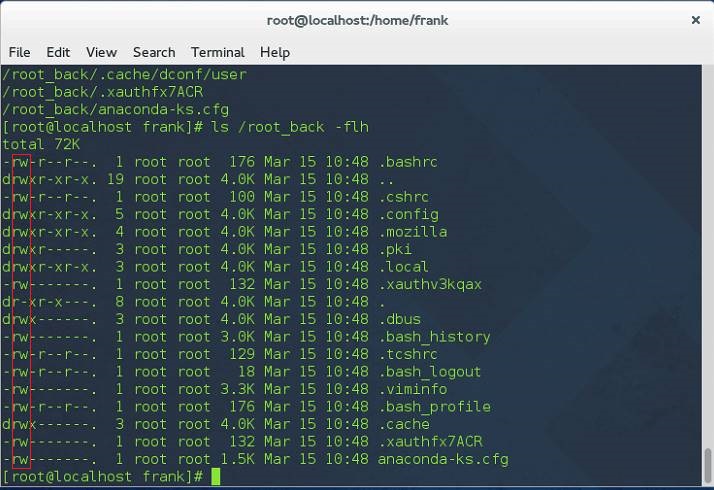
- Find a file and remove it.
# find . -type f -name "tecmint.txt" -exec rm -f {} \;
3. which command
If the file name that you are searching for is an executable file, that file can likely be found in less time using the which command. Because it only searches directories that are listed in a special variable called the PATH variable in the current BASH shell.
To see which folders are included in the PATH variable, issue command echo $PATH
Linking files
Superblock
The superblock is the section that contains information about the file system in general, such as the number of inodes and data blocks, as well as how much data a data block stores, in kilobytes.
Inode
The inode table consists of several inodes (information nodes); each inode describes one file or directory on the file system,and contains a unique inode number for identification.
What is more important, the inode stores information such as the file size, data block locations, last date modified,permissions,and ownership. When a file is deleted, only its inode (which serves as a pointer to the actual data) is deleted.
To view the inode number of the file, add -i option to the ls command.
Data block
The data that makes up the contents of the file as well as the file name are stored in data blocks, which are referenced by the inode.
In file system-neutral terminology, blocks are known as allocation units because they are the unit by which disk space is allocated for storage.
Hardlink
Hard-linked files share the same inode.
Syntax: use ln <existing file> <new_hardlink_file> command.
To hard-link directories in some cases,using the -F or –d option to the command.
On MAC, you can not use either -F or -d, use -s to create a symbolic link instead.
Symbolic link
Do not share the same inode and data blocks with their target file. The data blocks in a symbolically linked file contain only the path name to the target file.
Syntax: add -s option to the ln command.
File and directory permissions
Use current use name,use whoami command, to view the group , use groups command.
To change the ownership of a file or directory, use chown command.
Two arguments: first one is the new owner and second one is the files or directories to change. Add -R to change the recursively throughout the directory tree.
To change the group owner of a file or directory: chgrp
Two arguments: new owner group and files or directories to change.
To change the ownership and group ownership at same time, use “.” or “:”between them, there should be no space before or after the “.” or “:”
chown user1.root file1
change the file1 owner to user1, owner group to root.
Managing file and directory permissions
Talk about user before the permissions:
/etc/shadow :
The /etc/shadow file stores actual password in encrypted format for user’s account with additional properties related to user password i.e. it stores secure user account information. All fields are separated by a colon (:) symbol. It contains one entry per line for each user listed in /etc/passwd file Generally, shadow file entry looks as follows :
- Username : It is your login name.
- Password : It is your encrypted password. The password should be minimum 6-8 characters long including special characters/digits and more.
- Last password change (lastchanged) : Days since Jan 1, 1970 that password was last changed
- Minimum : The minimum number of days required between password changes i.e. the number of days left before the user is allowed to change his/her password
- Maximum : The maximum number of days the password is valid (after that user is forced to change his/her password)
- Warn : The number of days before password is to expire that user is warned that his/her password must be changed
- Inactive : The number of days after password expires that account is disabled
- Expire : days since Jan 1, 1970 that account is disabled i.e. an absolute date specifying when the login may no longer be used.
Example: create a user called peter, and disable it.
1,sudo adduser peter
2, sudo passwd peter :to create a password for user.
3, sudo gedit /etc/shadow , then delete the second column after the name to disable the account.
the * and ! in the second column, * means the demon account, the ! means account has been disabled.