Driver module missing:
By comparing the output of the dmesg, lshw , lsusb, and lspci commands to the output of the lsmod command, you can determine whether a driver module is missing for a hardware device in your system.
how? any script can do this?
Possible solution:
$ diff -u file1 file2 > file3
compare the difference between file1 and file2, and print it in file3.
Maybe use dmesg | grep <hardware_name>
Problem, these three command give outputs in three different format, how to make them into same format?
Library problem
Check the shared libraries are required by a certain program: ldd command, eg.
ldd /bin/bash
Ensure the list of shared library directories (/etc/ld.so.conf) and the list of shared libraries (/etc/ld.so.cache) are updated: ldconfig
File handle limit
File handles: processes can initiate numerous connections to files on the file system in addition to Standard Input, Standard Output,and Standard Error, these connections are called file handles.
The shell restricts the number of file handles that programs can open to 1024, to increase this number to 3000, use command ulimit -n 3000
To increase the maximum number of user processes to 20000, use command ulimit -u 20000.
check the log file
Most application log files are stored in the /var/log directory or subdirectories of the /var/log.
Eliminates BIOS problems with large hard disks
Ensure the Linux Kernel resides before the 1024th cylinder of the hard disk and that 32-bit large block addressing (lba32) keyword is specified in the boot loader configuration file.
Bus mastering
Some peripheral devices can perform a great deal of processing that is normally performed by the CPU.
Mornitoring performance with sysstat
System Statistics ( sysstat) package contains a wide range of utilities that monitor the system.
- mpstat:
mpstat [ -P { cpu | ALL } ] [ -V ] [ interval [ count ] ]for example, mpstat -P 2 2 10 means report the third cpu’s statistic every 2 second, 10 groups of data.
multiple processor statistics, -P # to measure a single CPU, # is the processor number, start from 0.- %usr: indicate the percentage of time the processor spent executing user programs and daemons.
- %nice: the percentage of time the processor spent executing user programs and daemons that had nondefault nice values.
- %sys: amount of time the system spent maintaining it self.
the %usr +%nice should be bigger than the %sys, or else too many resource-intensive programs. - %iowait: indicates the percentage of time the CPU was idle when an outstanding disk I/O request existed.
- %irq and %soft: the percentage of time the CPU is using to respond to normal interrupts and interrupts that span multiple CPUs.
- %guest: the percentage of time the CPU is executing another virtual CPU.
- %gnice: the percentage of time the processor spent executing user programs and daemons in the virtual CPU that had nondefault nice values.
- %steal: percentage of time the CPU is waiting to respond to virtual CPU requests.
- %idle: the percentage of time the CPU did not spend executing tasks, should be greater than 25percent.
- iostat:
iostat [ -c | -d ] [ -k ] [ -t ] [ -V ] [ -x ] [ { device [ ... ] | ALL } ] [ -p [ { device | ALL } ] ] [ interval [ count ] ]OPTIONS
-c The -c option is exclusive of the -d option and displays only the CPU usage report. -d The -d option is exclusive of the -c option and displays only the device utilization report. -k Display statistics in kilobytes per second instead of blocks per second. Data displayed are valid only with kernels 2.4 and newer. -p device | ALL The -p option is exclusive of the -x option and displays statis- tics for block devices and all their partitions that are used by the system. If a device name is entered on the command line, then statistics for it and all its partitions are displayed. Last, the ALL keyword indicates that statistics have to be dis- played for all the block devices and partitions defined by the system, including those that have never been used. Note that this option works only with post 2.5 kernels. -t Print the time for each report displayed. -V Print version number and usage then exit. -x Display extended statistics. This option is exclusive of the -p one, and works with post 2.5 kernels since it needs /proc/diskstats file or a mounted sysfs to get the statistics. This option may also work with older kernels (e.g. 2.4) only if extended statistics are available in /proc/partitions (the ker- nel needs to be patched for that).Report
Device Utilization Report The second report generated by the iostat command is the Device Utilization Report. The device report provides statistics on a per physical device or partition basis. Block devices for which statistics are to be displayed may be entered on the command line. Partitions may also be entered on the command line provid- ing that option -x is not used. If no device nor partition is entered, then statistics are displayed for every device used by the system, and providing that the kernel maintains statistics for it. If the ALL keyword is given on the command line, then statistics are displayed for every device defined by the system, including those that have never been used. The report may show the following fields, depending on the flags used: Device: This column gives the device (or partition) name, which is displayed as hdiskn with 2.2 kernels, for the nth device. It is displayed as devm-n with 2.4 kernels, where m is the major number of the device, and n a distinctive number. With newer kernels, the device name as listed in the /dev directory is displayed. tps Indicate the number of transfers per second that were issued to the device. A transfer is an I/O request to the device. Multiple logical requests can be combined into a single I/O request to the device. A transfer is of inde- terminate size. Blk_read/s Indicate the amount of data read from the drive expressed in a number of blocks per second. Blocks are equivalent to sectors with 2.4 kernels and newer and therefore have a size of 512 bytes. With older kernels, a block is of indeterminate size. Blk_wrtn/s Indicate the amount of data written to the drive expressed in a number of blocks per second. Blk_read The total number of blocks read. Blk_wrtn The total number of blocks written. kB_read/s Indicate the amount of data read from the drive expressed in kilobytes per second. Data displayed are valid only with kernels 2.4 and newer. kB_wrtn/s Indicate the amount of data written to the drive expressed in kilobytes per second. Data displayed are valid only with kernels 2.4 and newer. kB_read The total number of kilobytes read. Data displayed are valid only with kernels 2.4 and newer. kB_wrtn The total number of kilobytes written. Data displayed are valid only with kernels 2.4 and newer. rrqm/s The number of read requests merged per second that were issued to the device. wrqm/s The number of write requests merged per second that were issued to the device. r/s The number of read requests that were issued to the device per second. w/s The number of write requests that were issued to the device per second. rsec/s The number of sectors read from the device per second. wsec/s The number of sectors written to the device per second. rkB/s The number of kilobytes read from the device per second. wkB/s The number of kilobytes written to the device per second. avgrq-sz The average size (in sectors) of the requests that were issued to the device. avgqu-sz The average queue length of the requests that were issued to the device. await The average time (in milliseconds) for I/O requests issued to the device to be served. This includes the time spent by the requests in queue and the time spent servic- ing them. svctm The average service time (in milliseconds) for I/O requests that were issued to the device. %util Percentage of CPU time during which I/O requests were issued to the device (bandwidth utilization for the device). Device saturation occurs when this value is close to 100%.
Security
iptable
Whenever a packet arrives at the firewall, it will be either processed or disregarded. The disregarded packets would normally be those, which are malformed in some way or are invalid in some technical way. Based on the packet activity of those that are processed, the packets are enqueued in one of the three builtin ‘tables.’ The first table is the mangle table. This alters the service bits in the TCP header. The second table is the filter queue, which takes care of the actual filtering of the packets. This consists of three chains, and you can place your firewall policy rules in these chains (shown in the diagram below):
– Forward chain: It filters the packets to be forwarded to networks protected by the firewall, such as a router.
– Input chain: It filters the packets arriving at the firewall, such as a server receiving request.
– Output chain: It filters the packets leaving the firewall, such as a server sending data..
The third table is the NAT table. This is where the Network Address Translation or NAT is performed. There are two built-in chains in this:
– Pre-routing chain: It NATs the packets whose destination address needs to be changed.
– Post-routing chain: It NATs the packets whose source address needs to be changed.
Whenever a rule is set, the table it belongs has to be specified. The ‘Filter’ table is the only exception. This is because most of the ‘iptables’ rules are the filter rules. Therefore, the filter table is the default table.
The diagram below shows the flow of packets within the filter table. Packets entering the Linux system follow a specific logical path and decisions are made backed on their characteristics. The path shown below is independent of the network interface they are entering or exiting:
The Filter Queue Table
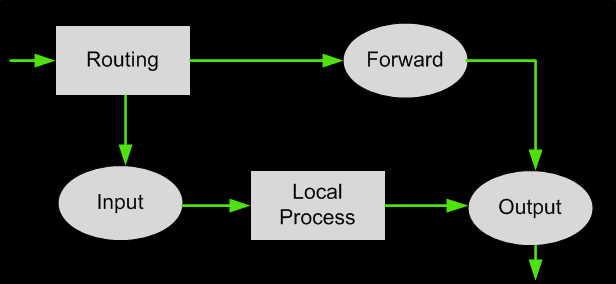
Each of the chains filters data packets based on:
- Source and Destination IP Address
- Source and Destination Port number
- Network interface (eth0, eth1 etc)
- State of the packet
iptables -A chain_name -i input_interface -s source_host/network -o output_interface -m state established,related -j action
Target for the rule: ACCEPT, DROP, REJECT, QUEUE, RETURN and LOG.
- -A : add a rule to the bottom, which will be assessed last.
- -I : Inserts a rule on the top, which will be assessed first
- -p :The connection protocol used
- –dport : The destination port(s) required for this rule. Note this must follow the -p parameter.
- –sport : The source port(s) required for this rule. Note this must follow the -p parameter.
- -j : action can be ACCEPT or DROP
- -L : list all the rules.
Change the default action
The default action is allow.
Note that these entries will be deleted after a reboot, to make them persistent, follow below steps:
Ubuntu:
You may want to use the iptables-persistent package rather than mess with your boot scripts. First, run your script to set up the firewall rules. Secondly, run sudo apt-get install iptables-persistent, and follow the prompts. When it asks to save the current rules, hit “Yes” at both prompts. Now, on reboots, your iptables rules will be restored.
NOTE: If you change your rules after this, you will need to do the following command(s) after the changes:
To save your IPv4 iptables rules: sudo su -c 'iptables-save > /etc/iptables/rules.v4'
To save your IPv6 ip6tables rules: sudo su -c 'ip6tables-save > /etc/iptables/rules.v6'
CentOS 7:
Enable iptables-services service
# yum install iptables-services # touch /etc/sysconfig/iptables # touch /etc/sysconfig/ip6tables # systemctl start iptables # systemctl start ip6tables # systemctl enable iptables # systemctl enable ip6tables
Save iptables and ip6tables rules
Backup the configuration before saving:
# cp /etc/sysconfig/iptables /etc/sysconfig/iptables-date +%s # cp /etc/sysconfig/ip6tables /etc/sysconfig/ip6tables-date +%s
Then save the iptables rules:
# iptables-save >/etc/sysconfig/iptables # ip6tables-save >/etc/sysconfig/ip6tables
If it does not work, you may need to use crontab to restore iptables:
crontab -e @reboot sudo iptables-restore /etc/sysconfig/iptables
Firewall-cmd
syntax : firewall-cmd –action –option
| –get-zones | Displays all available network zones. |
| –get-services | Displays a list of names used by firewalld to identify network services. |
| –get-default-zone | Specifies the source port number for a rule. |
| –set-default-zone=zone | Specifies the destination port number for a rule. |
| –get-active-zones | Displays the network interfaces that are active for each network zone. |
| –list-all-zones | Displays the services that are enabled (allowed) for each network zone. |
| –list-all | Displays the services that are enabled (allowed) for the current network zone. |
| –add-service=service | Enable (allow) the specified service within the current network zone. |
| –permanent | Ensure that the specified service is enabled (allowed) within the current network zone at boot time. |
| –add-port= port | Enable (allow) the specified port within the current network zone. |
| –remove-service=service | Disable (disallow) the specified service within the current network zone. |
| –remove-port=port | Disable (disallow) the specified port within the current network zone. |
| –query-service=service | Returns yes if the specified service is enabled (allowed) within the current network zone, and no if it is not. |
| –query-port=port | Returns yes if the specified port is enabled (allowed) within the current network zone, and no if it is not. |
Network zones:
| Network Zone | Type | Description |
| drop | Immutable | Deny all incoming connections; outgoing ones are accepted. |
| block | immutable | Deny all incoming connections, with ICMP host-prohibited messages issued to the sender |
| trusted | immutable | Allow all network connections. |
| public | mutable | Public areas, do not trust other computers. |
| external | mutable | For computers with masquerading enabled, protecting a local network. |
| DMZ | mutable | For computers publicly accessible with restricted access. |
| work | mutable | For trusted work areas. |
| home | mutable | For trusted home network connections. |
| internal | mutable | For internal network, restrict incoming connections. |
E.g.
firewall-cmd --add-port=22/tcp firewall-cmd --add-service=squid --permanent
Command to manage the firewall:
systemctl status firewalld systemctl start firewalld systemctl stop firewalld
Example
Redirect port from 80 to 8080:
iptables -A PREROUTING -t nat -i eth0 -p tcp --dport 80 -j REDIRECT --to-port 8080
iptables -t nat -I OUTPUT -p tcp -o lo --dport 80 -j REDIRECT --to-ports 8080reference
Configure Linux Firewall: http://www.firewall.cx/linux-knowledgebase-tutorials/system-and-network-services/850-linux-services-firewall.html