Managing GPOs
The following sections discuss GPO backup and restore, GPO import and copy, GPO migration, and GPO delegation.
GPO backup and Restore
In a large, complex network, with many different policy needs for users, servers, and 10 workstations, configuring and testing GPOs often takes many hours. Thankfully, Windows has a solution for backing up and restoring GPOs in case disaster strikes: GPO backups. GPO backups are also useful if you need to revert to an older version of a GPO or if you delete a GPO accidentally. For example, if many changes are made to a GPO and the changes cause unexpected problems, you might save time by restoring an older version instead of trying to undo the changes.
When you back up a GPO, the policy settings are backed up, but so are the security filtering settings, delegation settings, and WMI filter links. What’s not backed up are the WMI filter files associated with the WMI links, IPsec policies, and GPO container links.
Backing up a GPO is a simple three-step process:
1. In the GPMC, right-click the GPO in the Group Policy Objects folder (because you can’t back up a GPO from the shortcut link to an Active Directory container) and click Back Up.
2. Select (or create) a folder where the GPO should be stored. 3. Enter a description of the GPO, if you want, and click Back Up.
Multiple GPOs can be stored in the same folder, so you don’t need to create a folder each time you back up a GPO. The folder where you store GPO backups should be secure and backed up by a regular system backup routine. You can also right-click the Group Policy Objects folder and select options to back up all GPOs and manage backups.
The procedure for restoring a GPO varies, as follows:
• Restore a previous version—If the settings of a backed-up GPO have been changed and you need to revert to an older version, right-click the GPO in the Group Policy Objects folder, and click Restore from Backup. All policy and security settings in the current GPO are replaced by the backup GPO’s settings.
• Restore a deleted GPO—Right-click the Group Policy Objects folder and click Manage Backups to open the Manage Backups dialog box.
• Import settings—You can import settings from a backed-up GPO to an existing GPO by right-clicking the GPO and clicking Import Settings. This action is similar to restoring a GPO, except the existing GPO need not be the same GPO as the backed-up GPO. As with a GPO restore, all existing settings in the current GPO are deleted.
GPO Copy and Paste
If you simply want to copy the settings of a GPO into a new GPO, you can do so using the following steps from GPMC:
1. Right-click a GPO in the Group Policy Objects folder and click Copy.
2. Right-click the Group Policy Objects folder.
3. Click Paste. You’re asked whether to use the default permissions for the new GPO or preserve the existing permissions of the copied GPO. Make your choice and click OK.
4. Click OK in the progress dialog box after the copy is finished. The new GPO is named “Copy of OriginalGPOName.” For example, if you copied GPO1, the new GPO is named “Copy of GPO1.”
5. Rename the copied GPO by right-clicking it and clicking Rename.
Resetting Default GPOs
Making changes to the two default GPOs (Default Domain Policy and Default Domain Controller Policy) isn’t recommended. However, if you do make changes and need to revert to the original settings, you can do so without using a backup and restore operation. You can use the command-line program dcgpofix.exe to reset settings for either or both default GPOs. This command also resets permissions and any existing security or WMI filters:
• dcgpofix—Resets both the Default Domain Policy and the Default Domain Controllers Policy
• dcgpofix /target:DC—Resets the Default Domain Controllers Policy
• dcgpofix /target:domain—Resets the Default Domain Policy
GPO Migration
You might need to migrate GPOs from one domain to another for a variety of reasons. For example, you have a multidomain environment, and two domains have similar policy require- ments. After perfecting the GPOs in one domain, you can migrate them to be used in the other domain. Migration is also useful when you have set up a test environment that’s similar to one of your production domains. You can configure and test a GPO in the test environment thoroughly, and then migrate it to the production domain.
GPOs can be migrated across domains in the same or different forests by adding the domain to the GPMC. To add a domain in the same forest, right-click the Domains node in the left pane of the GPMC and click Show Domains to open the dialog box. Then select the domains you want to add to the GPMC.
To add a domain from a different forest, right-click the Group Policy Management node in the left pane of the GPMC and click Add Forest. Then enter the name of the domain in the forest that you want to add.
When you have multiple domains in the GPMC, you can simply copy and paste a GPO from the source domain’s Group Policy Objects folder to the target domain’s Group Policy Objects folder. When you click Paste in the target folder, the Cross-Domain Copying Wizard starts. It gives you the option to use default permissions or preserve existing permissions on the GPO and translates any security principals or UNC paths in the GPO.
A second method for migrating GPOs uses the backup and import procedure. The biggest difference between these two methods is that the copy-and-paste method creates a new GPO, and the backup and import procedure overwrites settings in an existing GPO in the target domain.
Configuring a Migration Table
If you’re migrating several GPOs from one domain to another, you might want to use a migration table to map security principals and UNC paths. A migration table is a list of security principals and UNC paths in a GPO that can be mapped to the security principals and UNC paths in the destination domain. The migration table can then be used when copying a GPO from one domain to another.
You create a migration table by right-clicking the Domains node in the GPMC and clicking Open Migration Table Editor or using the Cross-Domain Copying Wizard. In the Migration Table Editor, click Tools, and then choose Populate from GPO or Populate from Backup. All security principals and UNC paths used in the selected GPO are listed. By default, the Destination Name column is set to “<Same As Source>.” You change this column to translate information, as in the second entry in this figure. Special identities and built-in groups don’t need to be translated.
GPO Management Delegation
The possible permissions for GPO delegation depend on whether you’re working with the GPO or the target the GPO is linked to. Eight possible permissions can be applied to GPOs and the container objects they’re linked to through delegation:
On Group Policy Objects folder
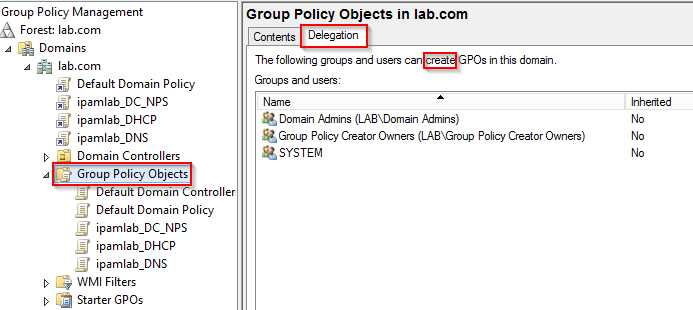
- Create GPOs—This permission applies only to the Group Policy Objects folder where you can find all GPOs in the GPMC. When you click the Group Policy Objects folder and click the Delegation tab in the right pane, you can view, add, and remove security principals who are allowed to create GPOs in the domain. By default, Domain Admins, Group Policy Creator Owners, and the System special identity have this permission.
On site, domain and OU
- Link GPOs—This permission can be set on sites, domains, and OUs and determines who can link or unlink a GPO to or from the container. Administrators, Domain Admins, Enterprise Admins, and the System special identity are granted this permission by default.
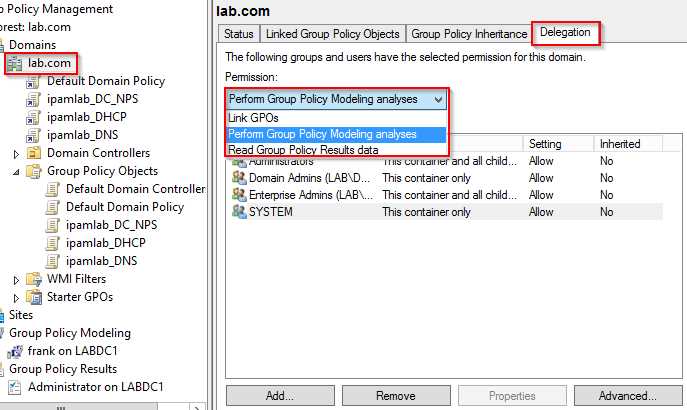
- Perform Group Policy Modeling analyses—See figure 2, This permission is set on domains and OUs and determines who can run the GPO Modeling Wizard (discussed in “Group Policy Results and Modeling” earlier in this chapter) on the specified container. The default users are the same as for the Link GPOs permission.
- Read Group Policy Results data—See figure 2, This permission is set on domains and OUs and determines who can run the Group Policy Results Wizard (discussed in “Group Policy Results and Modeling” earlier in this chapter) on users and/or computers. The default users are the same as for the Link GPOs permission.
On GPO
- Read—This permission is set on GPOs; users with this permission can view settings and back up a GPO. By default, the Enterprise Domain Controllers universal group has this permission for all GPOs.
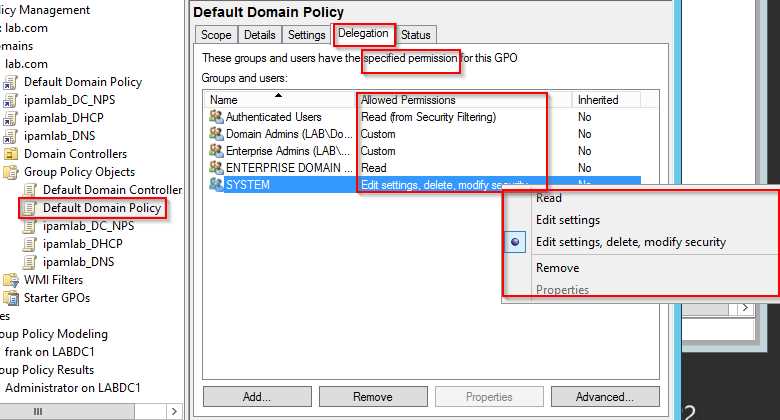
- Read (from Security Filtering)—This permission is used in group policy filtering. By default, the Authenticated Users group has this permission for all GPOs. It includes both the Read and Apply Group Policy permission and is generally set in the Scope tab of a GPO’s Proper- ties dialog box.
- Edit settings, delete, modify security—This permission is set on GPOs and determines who can edit, change status on, back up, delete, and change security on a GPO. By default, Domain Admins, Enterprise Admins, and the System special identity are granted this permission.
- Edit Settings—With this permission, security principals can change existing settings, import settings, and enable or disable a GPO. No users are granted this permission by default.
Reference
Group Policy Best practices: http://m.windowsitpro.com/group-policy/group-policy-design-best-practices