trust
No matter which kind of trust, make sure that DNS must be configured so that the FQDN of all participating domains can be resolved.
This can be done via AD-integrated forest-wide replication, conditional forwarders, stub zones. Use nslookup or similar tool to test after configuration.
Configure forest trust
Forest trust provides a one-way or two -way trust between forests that allows security principals in one forest to access resources in any domain in another forest.
We have forest “frankfu.com” with dc1 as the GC and ” frankfu.net” with dc3 as the GC. The interfaces are like following: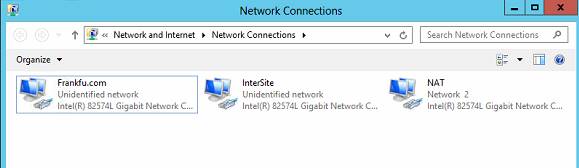
| DC1(Frankfu.com) | Frankfu.com | 192.168.0.10 | Connected to local forest |
| InterSite | 192.168.1.11 | Connected to Frankfu.net | |
| NAT | DHCP | Connected to ISP | |
| DC3(Frankfu.net) | Frankfu.net | 192.168.1.10 | Connected to Frankfu.com |
We want to create a forest trust between frankfu.com and frankfu.net.
1. Configure conditional forwarder DNS.
Create a stub zone on the frankfu.com DNS server and conditional forwarder on the frankfu.net DNS server.
On DC1, open DNS manager, right click Forward Lookup Zones and click New zone; Select Stub Zone as the zone type; make sure that Store the zone in the Active Directory is selected; in the Active Directory Zone replication scope window, select “To all DNS servers in this domain”( if have multiple domains, may need choose “To all DNS servers in this Forest” ); in the zone name, type frankfu.net; in the Master DNS servers, type the IP address of the server DC1(192.168.1.10); then open a command prompt window, type nslookup frankfu.net
On DC3, open DNS manager, expand the server node, right click the conditional forwarders and click New conditional forwarder; in the New conditional forwarder dialog box, type frankfu.com in the DNS domain text box and click <click here to add an IP address or DNS name> type 192.168.1.11, then Enter, click OK. test it by open a cmd, type nslookup frankfu.com
2. test access:
on DC3, type \\dc1.frankfu.com in the address area of explorer, then you will get the credential prompt. Try a user account which belongs to frankfu.net but not to frankfu.com, the logon should be unsuccessful.
3. Cerate a forest trust:
logon to DC1 as admin, open Active Directory Domains and Trusts; right click the frankfu.com and click properties; click the Trusts tab, then New Trust button; Type “frankfu.com” in the Name text box; Choose the Forest trust option; Two-way; in the Sides of trust window, click Both this domain and the specified domain; type frankfu.net\administrator in the user name and the password in the Password box; “Outgoing trust Authentication level-local forest” select “forest-wide“; next, next, in the confirm outgoing trust window, click “yes, confirm the outgoing trust“; in the confirm incoming trust window, click ” yes, confirm the incoming trust”; finish.
4. Confirm cross-forest access
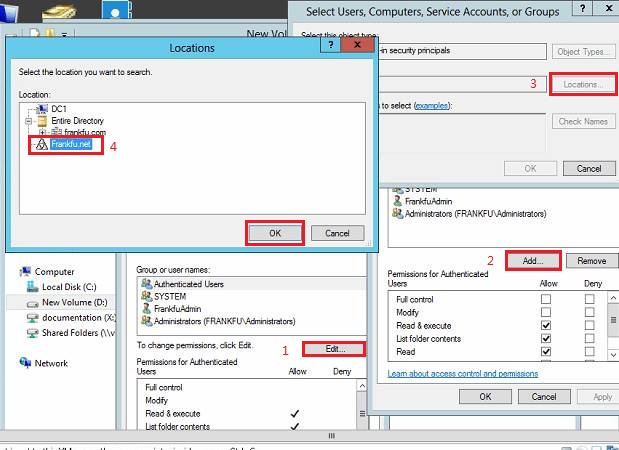
Log on to DC1, create a new folder in a drive, right click on the folder click property, then choose security tab. click Edit, then choose Add…; click location; you will see the new forest ” frankfu.net”, choose it, click ok; then type a user name which belongs to frankfu.net domain, click OK 3 times. Then share this folder and give authenticated user write and read permission.
Log on to DC3, type \\dc1.frankfu.com in the address area of the explorer, then provide the user name and password which was added above. You can see all the shared folders on DC1 and have read and write permission on the folder created above.
External and Realm trusts
External trust is created
- between domains in different forests
- between domains in a Windows Server 2003/2008 forest and a win2000 forest or Win NT domain.
Because windows 2000 server and Windows NT don’t support forest trusts, external trust is the only way to build a trust relationship between forests in these OSs and Win 2003/2008 forests - Windows domains on both sides of the trust
- Not transitive
- Need not be created between the forest root domains of two forests
- SID filtering is enabled by default in external trust.
Realm trust is created
- between a windows domain and a non-windows OS running the Kerberos v5 authentication protocol.
Configure the trust properties
Applies To: Windows Server 2008, Windows Server 2008 R2, Windows Server 2012
Open Active Directory Domain and Trusts, right click the FQDN of the domain, choose property, click trust tab, then choose the FQDN , click Properties… on the right hand side.
1. The general tab
| Item | Details | ||
|---|---|---|---|
| This Doman: | Displays the fully qualified domain name (FQDN) of the domain that is the current focus of the Active Directory Domains and Trusts snap-in. | ||
| Other Domain: | Displays the FQDN of the other domain in the selected trust relationship. | ||
| Trust type | Specifies the type of the selected trust relationship. | ||
| The other domain supports Kerberos AES Encryption | Specifies whether the other domain in the selected trust relationship supports Kerberos AES Encryption.
|
||
| Direction of trust | Informational purpose. Specifies the direction of the selected trust relationship. You have to delete and recreate the trust to change the trust direction. | ||
| Transitivity of trust | Informational purpose. Specifies whether the selected trust relationship is transitive. You can’t change the transitivity without recreating the trust. Note, some trusts, such as a forest and shortcut trust, are always transitive. |
||
| Validate | Click to confirm or reset the selected trust relationship. It performs the same action as the confirmation process at the end of the New Trust Wizard. If you didn’t create both sides of the trust with the wizard, you should validate the trust with this option after both sides have been created. |
||
| Save As | Click to save a file with the details about the status of the names that is associated with the selected trust relationship. |
2. The name suffix routing tab
You can control which name suffixes used by the trusted forest are routed for authentication. The name suffix routing tab displays all available name suffixes in the trusted forest, and you can enable or disable them.
For example, Forest A contains multiple trees-frankfu.com and frankfu.net- and Forest A is trusted by forest B. Only users from frankfu.com should have access to forest B resources, however. To do this, the Forest B administrator can disable authentication requests containing the name suffix frankfu.net.
| Item | Details |
|---|---|
| Name suffixes in the <DNS name> forest: |
|
| Enable | Click to set the routing status of the selected name suffix to Enabled. |
| Disable | Click to set the routing status of the selected name suffix to Disabled. |
| Refresh | Click to refresh the list of name suffixes in the local forest. |
| Edit | Click to exclude name suffixes from routing to the local forest. |
3. Authentication tab
- Forest-wide Authentication: Means windows should authenticate all users in the specified forest for all resources in the local forest.
Is recommended if both forests belong to the same organization. - Selective Authentication: choose which local forest resources that users in the specified forest can be authenticated to. Users from the trusted forest or domain can’t authenticate to the trusting forest or domain. If users try to authenticate to a computer in the trusting domain or forest and haven’t been granted authentication permission, they get an error message:
” \\xxxxx is not accessible. You might not have permission to use this network resource. Contact the administrator of this server to find out if you have access permissions. The computer you are signing into is protected by an authentication firewall. The specified account is not allowed to authenticate to the computer.”
After choosing this option, you have to give users or groups from the trusted forest the “Allowed to authenticate” permission to these computer accounts.
Is recommended for different organizations.
Consideration for Selective authentication
- To perform this procedure, you must be a member of the Domain Admins group or Enterprise Admins group in Active Directory Domain Services (AD DS), or you must have been delegated the appropriate authority. As a security best practice, consider using Run as to perform this procedure. For more information, search for “using run as” in Help and Support.
- For an external trust, if you select Selective authentication , you must enable permissions manually on the local domain and on the resource to which you want users in the external domain to have access.
- For a forest trust, if you select Selective authentication , you must enable permissions manually on each domain and resource in the local forest to which you want users in the second forest to have access.
- You can use selective authentication only on external trusts and forest trusts.
 Note
Note