Use Group policy and UAC can give some kind of restriction on the users. we can find them under: computer configuration>windows settings>security settings>Local Policy>security options
Scroll down, you can find 10 item start with “User Account Control:”
Some item is so confusing, here is one example:
| User Account Control: Detect application installations and prompt for elevation | EnableInstallerDetection | Enabled (default for home)
Disabled (default for enterprise) |
| User Account Control: Only elevate executables that are signed and validated | ValidateAdminCodeSignatures | Disabled |
Before we configure these two, let’s have a look at the difference between the signed and validated installation program:
If I log in the system with standard user, the unsigned and invalidated program will have a little shield on the right bottom of the icon. the signed one does not have it and the system will never ask you for password to elevate permission.
If I switch to a admin user, the shields all gone.
The first one: UAC will ask you to provide admin password when you try to install software which is unsigned and invalidated.
Second one: if you choose Disable, means elevate all executable files for “not signed or validated”.
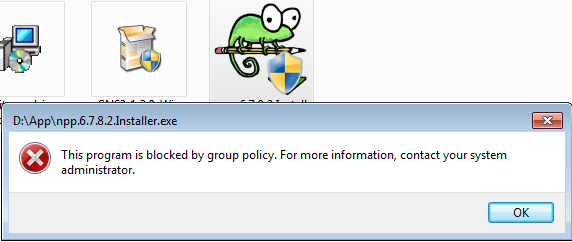
if you choose enable, and try to install a third-party software which is not signed or validated by microsft, it will pop up this
 I reckon it will just deny it without even bother to elevate it.
I reckon it will just deny it without even bother to elevate it.
It is really similar to this option “User Account Control: Behavior of the elevation prompt for standard users” changed to “Automatically deny elevation requests” but different error message.
For more , check here.