Traditional method:
Before the LAPS, we can change the local admin password either via GPO or startup powershell script:
The GPO method has been deprecated since one of the windows update in 2015, the powershell script can work as bellow:
$computer=$env:computername $user = "administrator" $Password = "password" $user = [adsi]"WinNT://$computer/$user,user" $user.SetPassword($Password) net user administrator /active:yes
You need to set the permission of the script file carefully, Or you can change the clear text to secure string to add a layer of security.
However, the LAPS is a more preferable way.
LAPS
Microsoft is offering the Local Administrator Password Solution (LAPS) that provides a solution to the issue of using a common local account with an identical password on every computer in a domain. LAPS resolves this issue by setting a different, random password for the common local administrator account on every computer in the domain. Domain administrators using the solution can determine which users, such as helpdesk administrators, are authorized to read passwords.
Why use LAPS instead of other password managers/vaults?
Other password managers typically require either, additional hardware (IIS/SQL), trusting a third party, or ad hoc practices (Excel spreadsheet of passwords = huge security hole).
LAPS provides a streamlined approach to:
- Periodically randomizing local administrator passwords – ensures password update to AD succeeds before modifying local secrets/passwords
- Centrally store secrets in existing infrastructure – Active Directory (AD)
- Control access via AD ACL permissions
- Transmit encrypted passwords from client to AD (using Kerberos encryption, AES cypher by default)
Components
- Agent – Group Policy Client Side Extension (CSE) – installed via MSI
- Event logging
- Random password generation – written from client computer to AD computer object
- PowerShell module
- Solution configuration
- Active Directory – centralized control
- Audit trail in security log of domain controller
- Computer object, confidential attribute
Deployment
The installation steps can be found in the documents where the app is downloaded.
Troubleshooting
1.LAPS UI/Powershell Password showing Blank
The issue could be, permission issue on the computer object, group policy password policy is conflicting with LAPS. Let’s start from the potential permission issue part:
Before troubleshooting you should know below two info:
- which OU did you delegate the password reset, read, computer self update password permission to, note down the OU name ABC.
- Which group did you allow to reset and read the password, note down the group XYZ.
This stage, check following, use powershell command import-module AdmPwd.PS, get-AdmPwdPassword -computerName xxxx, where this computer xxxx should under OU ABC or sub OU of ABC, note down the Expiration time stamp, then type command reset-AdmPwdPassword -ComputerName xxxx , then type get-AdmPwdPassword -computerName xxxx again. see if the timestamp changed to the time you type command reset-AdmPwdPassword.
If no change on the time stamp,which means you or the computer do not have permission to write attributes on the Computer object.
check both the permission you have on the OU ABC. Go to Active Directory Users and Computers, find the computer xxxx, right click go to properties > Security > Advanced > Effective Access tab > Select a user XYZ > make sure the Read ms-Mcs-AdmPwd, Write ms-Mcs-AdmPwd, Read ms-Mcs-AdmPwdExpirationTime, Write ms-Mcs-AdmPwdExpirationTime are green tick under Effective Access.
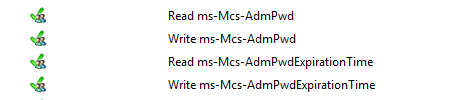
Then check if the computer can update the password and expiration timestamp of its own managed local Administrator password.
click the Select a user again, Type SELF and then View effective access. note that Read ms-Mcs-AdmPwd is not necessary. you should have Write ms-Mcs-AdmPwd, Read ms-Mcs-AdmPwdExpirationTime, Write ms-Mcs-AdmPwdExpirationTime are green tick under Effective Access.
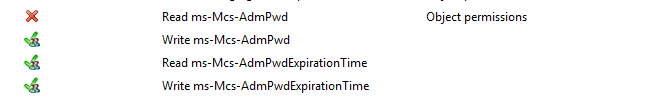
retype bellow command if required:
Grant Write permission on ms-Mcs-AdmPwd, ms-Mcs-AdmPwdExpirationTime for group XYZ:
Set-AdmPwdResetPasswordPermission -OrgUnit <name of the OU to delegate permissions> -AllowedPrincipals <users or groups>
Grant Write permission for ms-Mcs-AdmPwd, ms-Mcs-AdmPwdExpirationTime for computer itself:
Set-AdmPwdComputerSelfPermission -OrgUnit <name of the OU to delegate permissions>
If the time stamp changes but password not showing, which means you or the computer have permission to write attributes on the Computer object, but you may not have read permission. This may caused by the permisison on the object, do same troubleshooting above. And use command below if any read permission is missing for the user group. Note that Read ms-Mcs-AdmPwd is not necessary for computer it self, which reflects on the SELF user tab.
Set-AdmPwdResetPasswordPermission -OrgUnit <name of the OU to delegate permissions> -AllowedPrincipals <users or groups>
If all the Read ms-Mcs-AdmPwd is ticked for the user, and password still could not show in the powershell or LAPS GUI, then the password could not be stored in AD or not readable by AD due to some reason. This could be caused by GPO settings.
First of all, make sure Computer Configuration\Policies\Administrative Templates\LAPS\Enable local admin password management is Enabled.
Then let’s check the group policy setting in the Computer Configuration\Policies\Windows Settings\Security Settings\Account Policies\Password Policy node, and Computer Configuration\Policies\Administrative Templates\LAPS\Password Settings node. Check below setting
- LAPS password Policy must comply with GPO Domain password policy, which typically means password length configured under LAPS node should be longer than that under Password Policy node.
- Store passwords using reversible encryption: must be enabled. According to the architecture explanation:
Core of the solution is GPO Client side Extension (CSE) that performs the following tasks during GPO update:- Checks whether the password of local Administrator account has expired or not
- Generates the new password when old password expired or is required to be changed prior to expiration
- Changes the password of Administrator account
- Reports the password to password Active Directory, storing it in confidential attribute with computer account in AD
- Reports the next expiration time to Active Directory, storing it in confidential attribute with computer account in AD
- Password then can be read from AD by users who are allowed to do so
- Password can be forced to be changed by eligible users
Password has to be stored in a reversible encryption way, so it is visible in AD object attribute.
Work with ADMX central store
If your domain has enabled ADMX central store, the Group policy manager will read file from network share instead of local store, you may not be able to find the Settings in GPO, instead, if you go to Settings tab, they are showing under Extra Registry Settings. To fix this:
- copy the file AdmPwd.admx from %windir%\PolicyDefinitions\ to \\domain\SYSVOL\domain\Policies\PolicyDefinitions
- Copy the AdmPwd.admx from %windir%\PolicyDefinitions\en-US to \\domain\SYSVOL\domain\Policies\PolicyDefinitions\en-US
Restart the group policy management console.
Reference
https://technet.microsoft.com/en-us/library/security/3062591.aspx
Local Administrator Password Solution: https://technet.microsoft.com/en-us/mt227395.aspx
Download: https://www.microsoft.com/en-us/download/details.aspx?id=46899
https://blogs.technet.microsoft.com/askpfeplat/2015/12/28/local-administrator-password-solution-laps-implementation-hints-and-security-nerd-commentary-including-mini-threat-model/