Definition
Security descriptors define the security attributes of securable objects such as files, registry keys, WMI namespaces, printers, services, or shares. A security descriptor contains information about the owner and primary group of an object. A provider can compare the resource security descriptor to the identity of a requesting user, and determine whether or not the user has the right to access the resource that a user is requesting.
Some WMI methods, such as GetSD, return a security descriptor in the binary byte array format. Starting with Windows Vista, use the methods of the Win32_SecurityDescriptorHelper class to convert a binary security descriptor to an instance of Win32_SecurityDescriptor
Access Control and WMI Security Objects
The following is a list of WMI security objects:
The following diagram shows the relationships among WMI security objects.
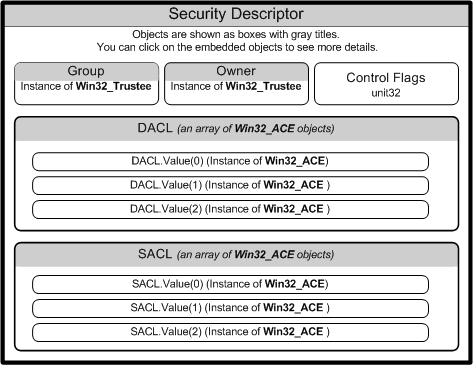
Win32_SecurityDescriptor Object
The following table lists the Win32_SecurityDescriptor class properties.
| Property | Description |
|---|---|
| ControlFlags | Set of control bits that qualify the meaning of an SD or its individual members. For more information about setting the ControlFlags bit values, see Win32_SecurityDescriptor. |
| DACL | Discretionary Access Control List (ACL) of users and groups, and their access rights to a secured object. This property contains an array of Win32_ACE instances that represent Access Control Entries. For more information, see Creating a DACL. |
| Group | Group to which this secured object belongs. This property contains an instance of Win32_Trustee that contains the name, domain, and security identifier (SID) of the group to which the owner belongs. |
| Owner | Owner of this secured object. This property contains an instance of Win32_Trustee that contains the name, domain, and security identifier (SID) of the owner. |
| SACL | System Access Control List (ACL) contains an array of Win32_ACE instances that represent the type of access attempts that generate audit records for users or groups. For more information, see SACL for a New Object. |
DACL and SACL
The arrays of Win32_ACE objects in the discretionary access control list (DACL) and system access control list {SACL) create a link between a user or group and their access rights.
When a DACL property does not contain an access control entry (ACE), access rights are not granted and access to the object is denied.
Win32_ACE, Win32_Trustee, Win32_SID
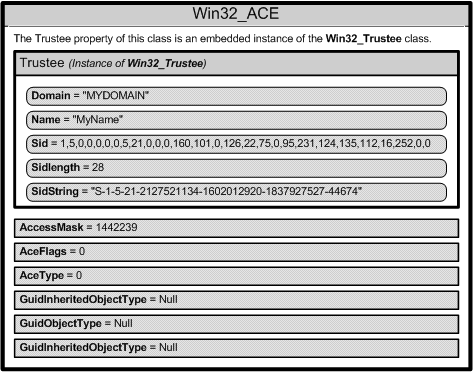
A Win32_ACE object contains an instance of the Win32_Trustee class that identifies a user or group, and an AccessMask property that is a bitmask, which specifies the actions that a user or group can take. For example, a user or group might be granted the right to read a file but not write to the file. A Win32_ACE object also contains an ACE that indicates whether or not it is an allow or a deny access.
Each user account or group represented by a Win32_Trustee has a security identifier (SID) that uniquely identifies an account, and specifies the access privileges of the account. How you specify the SID data depends on the operating system. For more information, see Changing Access Security on Securable Objects.
The following diagram shows the contents of one Win32_ACE instance.
Two items that Windows uses to help keep track of a user’s security rights and identity are
■ Security identifiers
■ Relative identifiers
Security Identifi ers (SIDs) are a data structure of variable length that identifies user, group, and computer accounts. For example, a SID of S-1-1-0 indicatesa group that includes all users. Closely tied to SIDs are Relative Identifiers (RIDs).
A RID is a part of the SID that identifi es a user or group in relation to the authority that user has. Here is an example:
S-1-5-21-1607980848-492894223-1202660629-500
- S for security id
- 1 Revision level
- 5 Identifier Authority (48 bit) 5 = logon id
- 21 Sub-authority (21 = nt non unique)
- 1607980848 SA
- 492894223 SA domain id
- 1202660629 SA
- 500 User id
Notice the last line. This value (known as a RID) is the user ID and specifies a definite user. Table 5-2 lists some common RIDs.
Table 5-2: User IDs and RIDs
| USER ID | RID CODE |
| Administrator | 500 |
| Guest | 501 |
| Kerberos | 502 |
| 1st user | 1000 |
| 2st user | 1001 |
This is somewhat similar to the way that Linux controls access for users and system processes by using an assigned user ID (UID) and a group ID (GID) that is found in the /etc/passwd file.
Reference
https://msdn.microsoft.com/en-us/library/aa394577(v=vs.85).aspx