Create iRule for this
Rule:
Create a new rule called Insert_CertObject_Header
Definition:
when HTTP_REQUEST {
HTTP::header insert X-Client-Cert [X509::subject [SSL::cert 0]]
}
Other area can be returned:
Replace X509::subject with it.
- X509::cert_fields – Returns a list of X509 certificate fields to be added to HTTP headers for ModSSL behavior.
- X509::extensions – Returns the X509 extensions set on an X509 certificate.
- X509::hash – Returns the MD5 hash (fingerprint) of an X509 certificate.
- X509::issuer – Returns the issuer of an X509 certificate.
- X509::not_valid_after – Returns the not-valid-after date of an X509 certificate.
- X509::not_valid_before – Returns the not-valid-before date of an X509 certificate.
- X509::pem2der – Returns an X509 certificate in DER format
- X509::serial_number – Returns the serial number of an X509 certificate.
- X509::signature_algorithm – Returns the signature algorithm of an X509 certificate.
- X509::subject – Returns the subject of an X509 certificate.
- X509::subject_public_key – Returns the subject’s public key of an X509 certificate.
- X509::subject_public_key_RSA_bits – Returns the size of the subject’s public RSA key of an X509 certificate.
- X509::subject_public_key_type – Returns the subject’s public key type of an X509 certificate.
- X509::verify_cert_error_string – Returns an X509 certificate error string.
- X509::version – Returns the version number of an X509 certificate.
- X509::whole – Returns an X509 certificate in PEM format.
Setting requirement:
Import CA cert
System >> Certificate Management > Traffic Certificate Management > SSL Certificate List
Click Import, Give it a name, and browse CA cert to import.
Enable SSL client profile
Under Virtual Server, find the Virtual Server you created
Under tab Properties:
SSL Profile (client) add clientssl from Available to Selected.
Profiles > SSL > Client ›› clientssl
Client Authentication:
Client Certificate: require
Frequency: Always
Trusted Certificate Authorities: Select the CA issued the client cert.
Under tab Resources:
After iRules, click button Manage…, select Insert_CertObject_Header from Available, click << to move it to Enabled.then click finished
Test
open a webbrowser, open virtual server IP on F5:
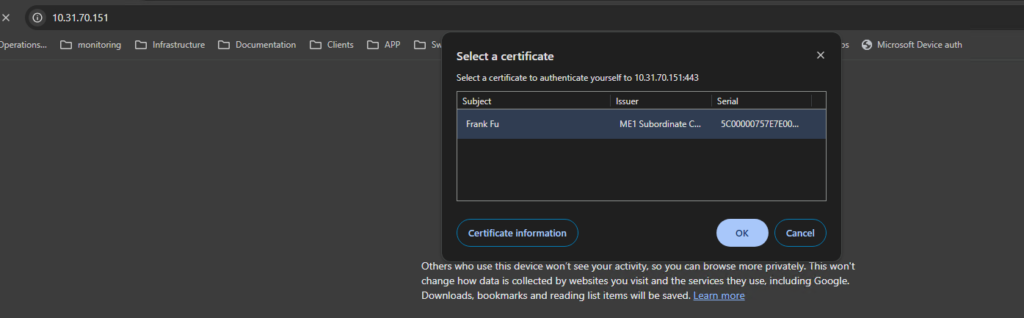
On the Server side, wireshark should capture this:
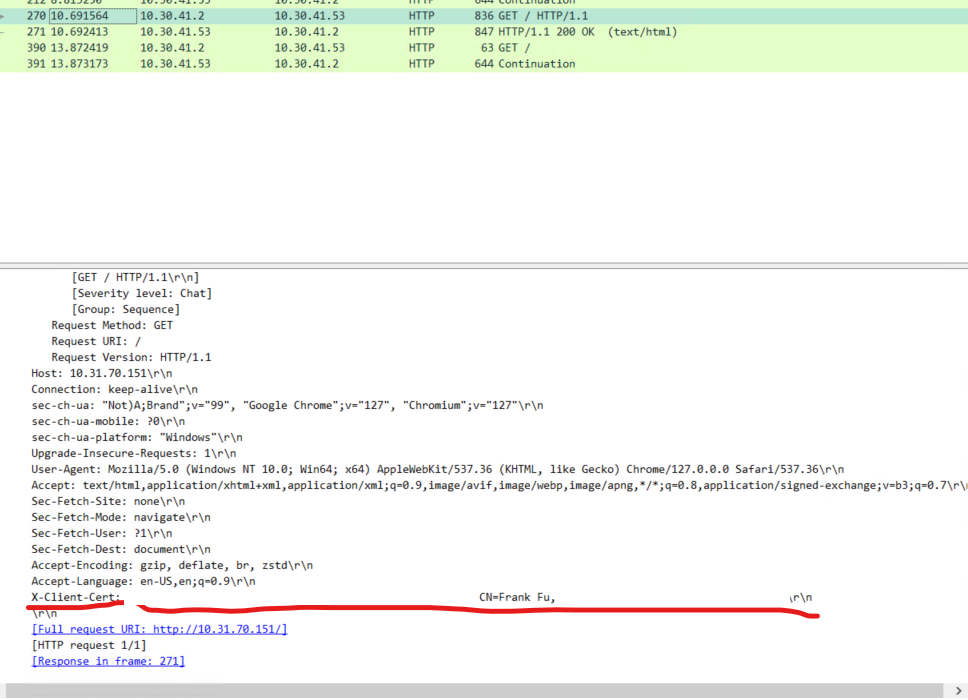
Ref:
https://my.f5.com/manage/s/article/K95338243