Password restrictions:
- At least 6 characters
- can use alphabetic, numeric,and special characters, except control characters.
- Must contain at least one change of case or character class.
User working directory
The system generates a home directory for new user. It can be changed in operational mode: “set cli directory directory “command.
Authentication order:
The three supported authentication methods are: RADIUS, TACACS+, local password. Authentication Order is from left to right.
If the system try to communicate with authentication server and no reply got, the system will consults local authentication as a last resort.
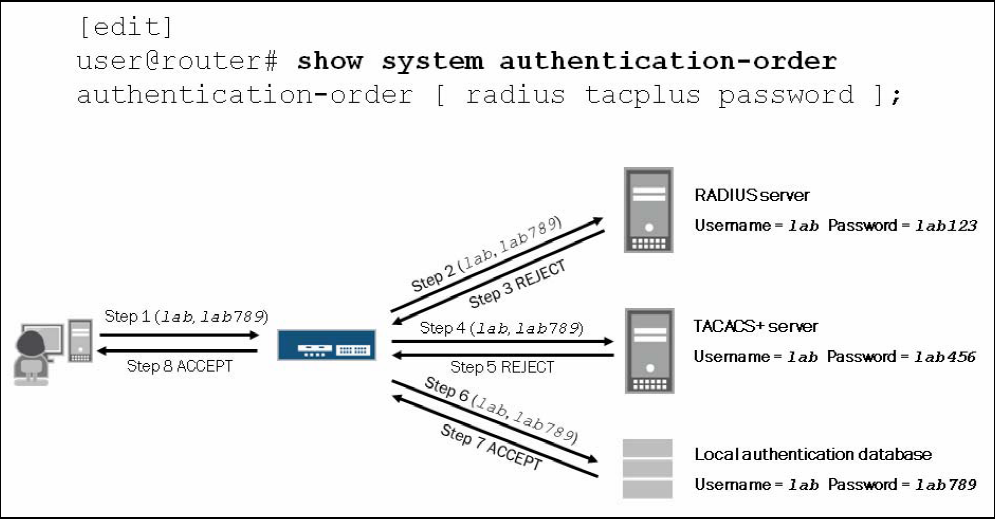
eg1:
user@router# show system authentication-order
authentication-order[ radius tacplus password];
The 1st step is user send user name and password to access point, step 2 u and p are sent to RADIUS server to verify, step3 RADIUS server give the reply; if matches, user get logged in, if no, u and p are sent to TACACS server for 2nd round verification. then 3rd round check the local database.
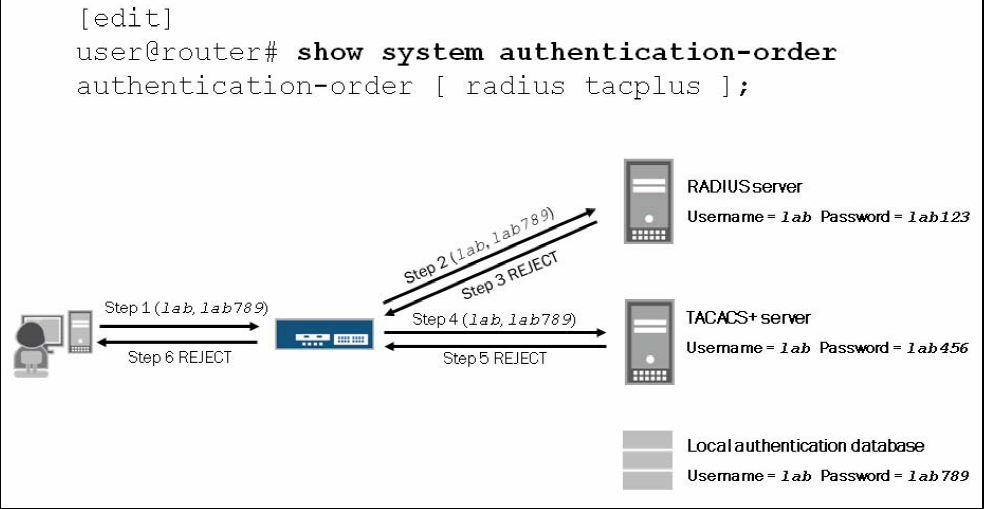
eg2
user@router# show system authentication-order
authentication-order[ radius tacplus ]
in this case, if all the server send back a respond and user name and password passed none of the server, the user will get rejected even if the input username and password match the local database.

One extreme case is, if both RADIUS server and TACACS+ server are down, the user can’t contact with anyone, the access point will use local database to consult.
Authorization overview
After authentication, the system will consult the user permission levels, this applies to both the CLI and J-web interface.
User–>class–>Permissions–> Deny-commands, deny-configurations–>allow-commands,allow-configurations–>Authorized or Denied
Junos applies authorization to all nonroot users and you can not disable this feature.
Users, class, permissions
Users are members of a single login class, multiple remotely authenticated users can be mapped to a locally defined template user.
Class: There are 4 predefined login classes exist to handle most situations.
- super-user: all permissions
- operator: clear, network, reset, trace, and view permissions
- read-only: view permissions
- unauthorized: no permissions
Beside these 4 permissions, we can configure custom login classes according to need.
Permission tags:
- Access: allows the viewing of network access configuration
- Access-control: allows the modifying of network access configuration
- Admin: allows the viewing of user accounts
- Admin-control: allows the modifying of user accounts
- All: enables all permission bits to be turned on.
- Clear: allows the clearing of learned network information
- Configure: allows the entering of configuration mode
- control: allows the modifying of any configuration values ( must be used in conjunction with the configure permission):
- field:Can view field debug commands.
- Firewall: Can view the firewall filter configuration in configuration mode.
- Firewall-control: Can view and configure firewall filter information at the [edit dynamic-profiles firewall], [edit firewall], and [edit logical-systems firewall] hierarchy levels.
- Floppy: Can read from and write to the removable media.
- Flow-tap:Can view the flow-tap configuration in configuration mode.
You can use Deny-commands, allow-commands, deny-configuration, allow-configuration statements to define regular expressions. Allow-command override deny-command. Because no matter which one the user input first, System process deny-command first then process allow-commands.
Show command:
[edit]
user@router#show system authentication-order
In [edit system] level!
show radius-server
Show tacplus-server
show login user username
System Logging
Junos syslog operations use a UNIX syslog-style to record system-wide,high-level operations.
The results file of the logging operations are stored in /var/log directory.
The primary syslog file, which is included in the factory-default configurations is the /var/log/messages file.
We can enabled or modify the syslog operations at the [edit system syslog] level and [edit routing-options options syslog] hierarchy level.
- The facility: it is listed first and defines the class of log messages.
- Severity level: listed second and determines the level of the detail to be logged.
|
Facility |
Type of Event or Error |
|---|---|
|
any |
All (messages from all facilities) |
|
authorization |
Authentication and authorization attempts |
|
change-log |
Changes to the Junos OS configuration |
|
conflict-log |
Specified configuration is invalid on the router type |
|
daemon |
Actions performed or errors encountered by system processes |
|
dfc |
Events related to dynamic flow capture |
|
firewall |
Packet filtering actions performed by a firewall filter |
|
ftp |
Actions performed or errors encountered by the FTP process |
|
interactive-commands |
Commands issued at the Junos OS command-line interface (CLI) prompt or by a client application such as a Junos XML protocol or NETCONF XML client |
|
kernel |
Actions performed or errors encountered by the Junos OS kernel |
|
pfe |
Actions performed or errors encountered by the Packet Forwarding Engine |
|
user |
Actions performed or errors encountered by user-space processes |
Severities:
|
Severity Level |
Description |
|---|---|
|
any |
Includes all severity levels |
|
none |
Disables logging of the associated facility to a destination |
|
emergency |
System panic or other condition that causes the router to stop functioning |
|
alert |
Conditions that require immediate correction, such as a corrupted system database |
|
critical |
Critical conditions, such as hard errors |
|
error |
Error conditions that generally have less serious consequences than errors at the emergency, alert, and critical levels |
|
warning |
Conditions that warrant monitoring |
|
notice |
Conditions that are not errors but might warrant special handling |
|
info |
Events or nonerror conditions of interest |
We can use wildcard mask in the severity-levels.
Syslog configuration options:
- Host name or ip address: send the syslog messages to a remote host.
- archive: how to archive system loggin files.
- console: type of syslog messages to log to the system console
- facility: displays the class of log messages
- severity: display the severity level of log messages.
- file filename: configures the name of the log file.
- file number: displays maximum number of system log files.
Syslog fields:
Timestamp: hostname: software process name or PID: a message code: message text
- Timestamp: indicates when the message was logged
- Name: displays the configured system name
- Process name or PID: displays the name of the process
- Message-code: provides a code that identifies the general nature and purpose of the message (eg: UI_DBASE_LOGOUT_EVENT)
- Message-text: Additional information related to the message code.
When you add the explicit-priority statement, the Junos OS alters the syslog message format to include a numeric priority value. 0 indicates most significant and 7 indicates debug-level message.
View syslog
- Syntax: show log file-name
- Pipe(|): screening the result. logical behind the pipe.
- when the pipe used together with “” means “or” not “and” , eg: “error|kernel|pack” ,means just need to match one of them.
- when the pipe is solo used, means “and”, eg show log messages |match “support”|match “Apr 1 15”, means need to match both “support” and “Apr 1 15”.