Netflow
NetFlow is a Cisco IOS technology that provides statistics on packets flowing through a Cisco router or multilayer switch. NetFlow is the standard for collecting IP operational data from IP networks.
While SNMP attempts to provide a very wide range of network management features and options, NetFlow is focused on providing statistics on IP packets flowing through network devices.
Flexible NetFlow is the latest NetFlow technology. Flexible NetFlow improves on “original NetFlow” by adding the capability to customize the traffic analysis parameters for the specific requirements of a network administrator. Flexible NetFlow facilitates the creation of more complex configurations for traffic analysis and data export through the use of reusable configuration components.
Flexible NetFlow uses the Version 9 export format. The distinguishing feature of the NetFlow Version 9 export format is that it is template-based. Templates provide an extensible design to the record format, a feature that allows future enhancements to NetFlow services without requiring concurrent changes to the basic flow-record format. It is important to note that many useful Flexible NetFlow commands were introduced with Cisco IOS Release 15.1.
Most organizations use NetFlow for some or all of the following important data collection purposes:
- Measuring who is using what network resources for what purpose.
- Accounting and charging back according to the resource utilization level ( by ISP ).
- Using the measured information to do more effective network planning so that resource allocation and deployment is well-aligned with customer requirements.
- Using the information to better structure and customize the set of available applications and services to meet user needs and customer service requirements.
NetFlow uses a “push-based” model. The collector simply listens for NetFlow traffic, and the networking devices are in charge of sending NetFlow data to the collector, based on changes in their flow cache. Another difference between NetFlow and SNMP is that NetFlow only gathers traffic statistics, as shown in the figure, whereas SNMP can also collect many other performance indicators, such as interface errors, CPU usage, and memory usage. On the other hand, the traffic statistics collected using NetFlow have a lot more granularity than the traffic statistics that can be collected using SNMP.
Note: Do not confuse NetFlow’s purpose and results with that of packet capture hardware and software.
When Cisco sought out to create NetFlow, two key criteria provided guidance in its creation:
- NetFlow should be completely transparent to the applications and devices in the network.
- NetFlow should not have to be supported and running on all devices in the network to function.
Achieving these design criteria ensured that NetFlow is very easy to implement in the most complex modern networks.
Note: Although NetFlow is simple to implement and transparent to the network, it does consume additional memory on the Cisco device, because NetFlow stores record information in “cache” on the device. The default size of this cache varies based on the platform, and the administrator can adjust this value.
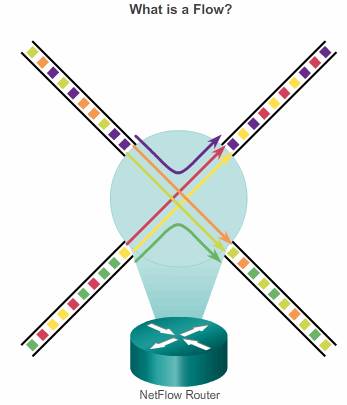
Flow
NetFlow breaks down TCP/IP communications for statistical record keeping using the concept of a flow.
A flow is a unidirectional stream of packets between a specific source system and a specific destination. The source and destination are defined by their network layer IP addresses and their transport layer source and destination port numbers.
“original NetFlow” distinguished flows using a combination of seven fields. Should one of these fields vary in value from another packet, the packets could be safely determined to be from different flows:
- Source IP address
- Destination IP address
- Source port number
- Destination port number
- Layer 3 protocol type: The Layer 3 protocol type identifies the type of header that follows the IP header (usually TCP or UDP, but other options include ICMP).
- Type of Service (ToS) marking: The ToS byte in the IPv4 header holds information about how devices should apply quality of service (QoS) rules to the packets in that flow.
- Input logical interface
When defining records for a Flexible NetFlow flow monitor cache, they are referred to as user-defined records. The values in optional fields are added to flows to provide additional information about the traffic in the flows. A change in the value of an optional field does not create a new flow.
Configure Netflow
NetFlow configuration considerations:
- Newer Cisco routers, such as the ISR G2 series, support both NetFlow and Flexible NetFlow.
- Newer Cisco switches, such as the 3560-X series switches, support Flexible NetFlow; however, some Cisco switches, such as Cisco 2960 Series switches, do not support NetFlow or Flexible NetFlow.
- NetFlow consumes additional memory. If a Cisco networking device has memory constraints, the size of the NetFlow cache can be pre-set so that it contains a smaller number of entries. The default cache size depends on the platform.
- NetFlow software requirements for the NetFlow collector vary. For example, the Scrutinizer NetFlow software on a Windows host requires 4 GB of RAM and 50 GB of drive space.
Note: The focus here is on Cisco router configuration of the original NetFlow (referred to simply as NetFlow in the Cisco documentation). The configuration of Flexible Netflow is beyond the scope of this course.
To implement NetFlow on a router:
Step 1. Configure NetFlow data capture – NetFlow captures data from ingress (incoming) and egress (outgoing) packets.
A NetFlow flow is unidirectional. This means that one user connection to an application exists as two NetFlow flows, one for each direction. To define the data to be captured for NetFlow in interface configuration mode:
- Capture NetFlow data for monitoring incoming packets on the interface using the
R1(config-if)#ip flow ingresscommand.
- Capture NetFlow data for monitoring outgoing packets on the interface using the
R1(config-if)#ip flow egresscommand.
Step 2. Configure NetFlow data export – The IP address or hostname of the NetFlow collector must be specified and the UDP port to which the NetFlow collector listens.
To enable the NetFlow data to be sent to the NetFlow collector, there are several items to configure on the router in global configuration mode:
- NetFlow collector’s IP address and UDP port number – Use the
R1(config)#ip flow-export destination ip-address udp-portcommand. The collector has one or more ports, by default, for NetFlow data capture. The software allows the administrator to specify which port or ports to accept for NetFlow capture. Some common UDP ports allocated are 99, 2055, and 9996.
- (Optional) NetFlow version to follow when formatting the NetFlow records sent to the collector – Use the
R1(config)#ip flow-export version versioncommand. NetFlow exports data in UDP in one of five formats (1, 5, 7, 8, and 9). Version 9 is the most versatile export data format, but it is not backward compatible with previous versions. Version 1 is the default version if the version is not specified with Version 5. Version 1 should be used only when it is the only NetFlow data export format version that is supported by the NetFlow collector software.
- (Optional) Source interface to use as the source of the packets sent to the collector – Use the
R1(config)#ip flow-export source typenumbercommand.
Step 3. Verify NetFlow, its operation and statistics – After configuring NetFlow, the exported data can be analyzed on a workstation running an application, such as SolarWinds NetFlow Traffic Analyzer, Plixer Scrutinizer, or Cisco NetFlow Collector (NFC). Minimally, one can rely on the output from a number of show commands on the router itself.
Example:
Verify Netflow
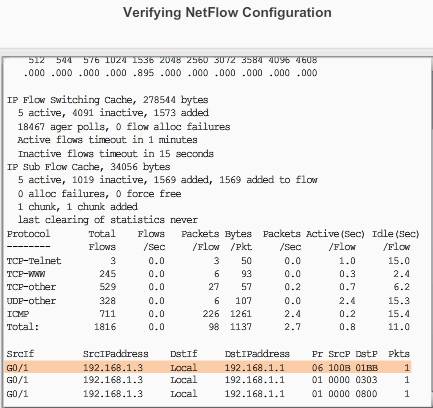
To display a summary of the NetFlow accounting statistics, as well as which protocol uses the highest volume of the traffic, and to see between which hosts this traffic flows, use the show ip cache flow command in user EXEC or privileged EXEC mode.
It also shows the source port (SrcP) and destination port (DstP) in hexadecimal.
Note: Hexadecimal 01BB is equal to decimal 443, the well-known TCP port for HTTPS.
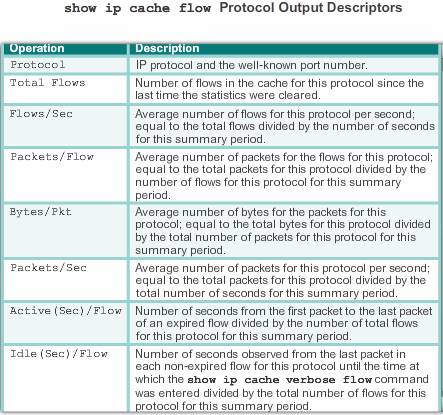
The significant fields in the flow switching cache lines of the show ip cache flow command output.
| Field | description |
| bytes | number of bytes of memory used by the Netflow cache |
| active | number of active flows in the Netflow cache at the time this command was entered. |
| inactive | number of flow buffers that are allocated in the Netflow cache, but were not currently assigned to a specific flow at the time this command was entered. |
significant fields in the activity:
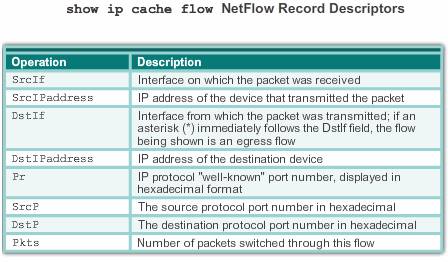
Netflow record descriptors
Examin traffic patterns
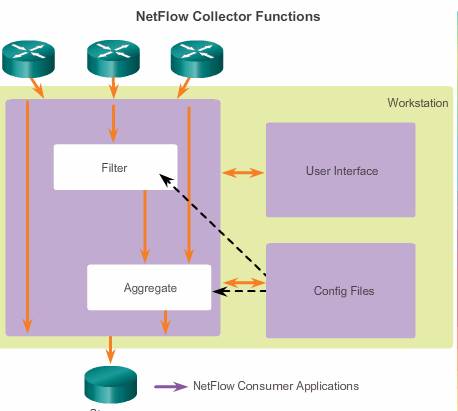
A NetFlow collector is a host that is running application software. This software is specialized for handling raw NetFlow data. This collector can be configured to receive NetFlow information from many networking devices. NetFlow collectors aggregate and organize NetFlow data as prescribed by the network administrator within the constraints of the software.
Figure above illustrates a NetFlow collector passively listening for exported NetFlow datagrams. A NetFlow collector application provides a high-performance, easy-to-use, scalable solution to accommodate consumption of NetFlow export data from multiple devices.
The intended use by an organization varies, but often the purpose is to support critical flows associated with consumer applications. These include accounting, billing, and network planning and monitoring.
Based on usage of NetFlow analyzers, a network administrator is able to identify:
- Who are the top talkers and to whom are they talking?
- What websites are routinely visited and what is downloaded?
- Who is generating the most traffic?
- Is there enough bandwidth to support mission-critical activity?
- Who is monopolizing the bandwidth?
The amount of information that can be analyzed by a NetFlow collector varies based on the NetFlow version used, because different NetFlow export formats consist of distinct NetFlow record types. A NetFlow record contains the specific information about the actual traffic that makes up a NetFlow flow.
A NetFlow collector provides real-time visualization and analysis of recorded and aggregated flow data. The routers and supported switches can be specified, as well as the aggregation scheme and the time interval to store data prior to the next periodic analysis. One can sort and visualize the data in a manner which makes sense for the users: bar charts, pie charts, or histograms of the sorted reports. The data can then be exported to spreadsheets, such as Microsoft Excel, for more detailed analysis, trending, and reporting.
Netflow Collector
Scrutinizer is one of many options for capturing and analyzing NetFlow data on a NetFlow collector. Others include PRTG (Free for less than 100 sensors)
Flow monitor
Flow monitors are the Flexible NetFlow component that is applied to interfaces to perform network traffic monitoring. Flow monitors consist of a record and a cache. You add the record to the flow monitor after you create the flow monitor. The flow monitor cache is automatically created at the time the flow monitor is applied to the first interface.
Flow data is collected from the network traffic during the monitoring process based on the key and nonkey fields in the record, which is configured for the flow monitor and stored in the flow monitor cache.
For example, the following example creates a flow monitor named FLOW-MONITOR-1 and enters Flexible NetFlow flow monitor configuration mode:
Router(config)# flow monitor FLOW-MONITOR-1
Router(config-flow-monitor)#