IPv4
Ping packet
In windows, it’s abcdefghijklmnopqrstuvw 20 letters.
ping large packet :
e.g. ping 2000 bytes packet : ping -l 2000 8.8.8.8
You may get request time out, then you can reduce the size to 1700, or 1000. at some point you can ping through.
ping -l 2000 -f 8.8.8.8
-f means don’t fragment.
Analyzing IP header
Check here for the IPv4 header basic knowledge: http://frankfu.click/networking/networking-fundamental/ipv4-vs-ipv6.html
Fragmentation
Fragmentation is normal because packet area often too large to transmit in one shot.
Three header fields are essential to fragmentation:
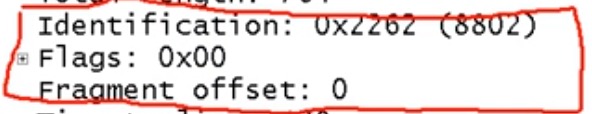
1. Identification : what’s my id?
If a packet is fragmented , ID field will be the same, so you can track the segments by the ID field.
ip.id=xxxx
2. flags : can I split the packet? are there more?
Reserved bit
Don’t fragment
More fragment : ip.flags.mf==0 , you can right click this flag, apply a filter > selected.
3. Fragment offset: how many bytes has been transferred before this packet?
Show the packets with offset, it’s multiple of 8. e.g. If the offset is 1480, it will show b9(185) here, because 1480/8=185.
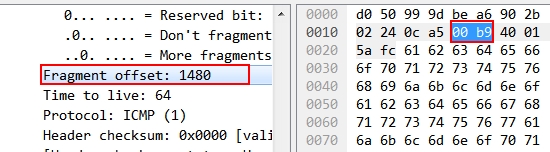
Filter to show the packet with offset:
ip.frag_offset >0
Fragmentation Example:
It’s hard to capture a normal traffic with packet defragmentation, I will ping a internal server with large packet 2000 bytes which is bigger than the MTU 1500, so the packet will be fragmented into smaller packets. And we can analysis on the procedure.
1. start to capture in Wireshark, then ping the target server ping -l 2000 -n 8 192.168.90.252
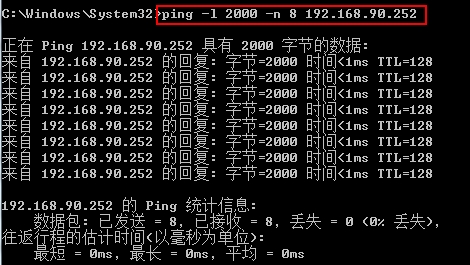
2. Then filter the icmp traffic between two host
We take a look at the first packet from my host to the server:
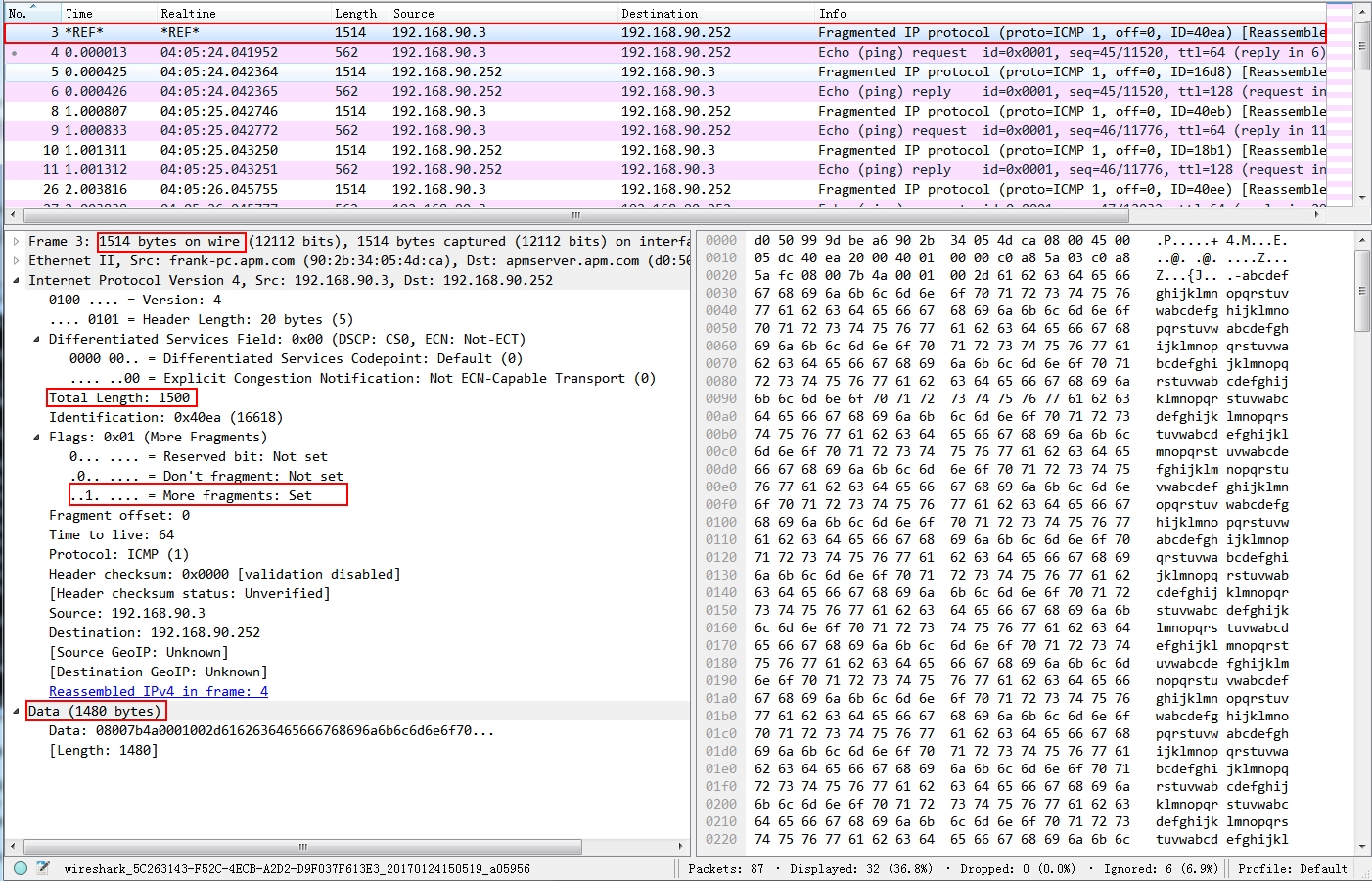
Note the marked area:
- Right click the first packet and click “set/unset Time reference”
- 1514 means the frame size, which is from 1500 (mtu size) + 14 (802.3 frame header length), for more check here: http://frankfu.click/networking/networking-fundamental/ethernet.html
- more fragments is set, means there are more packet on the way.
- The actual payload ( data ) is 1480 bytes, which means there are more 520 bytes to be transferred.
Then the second packet:
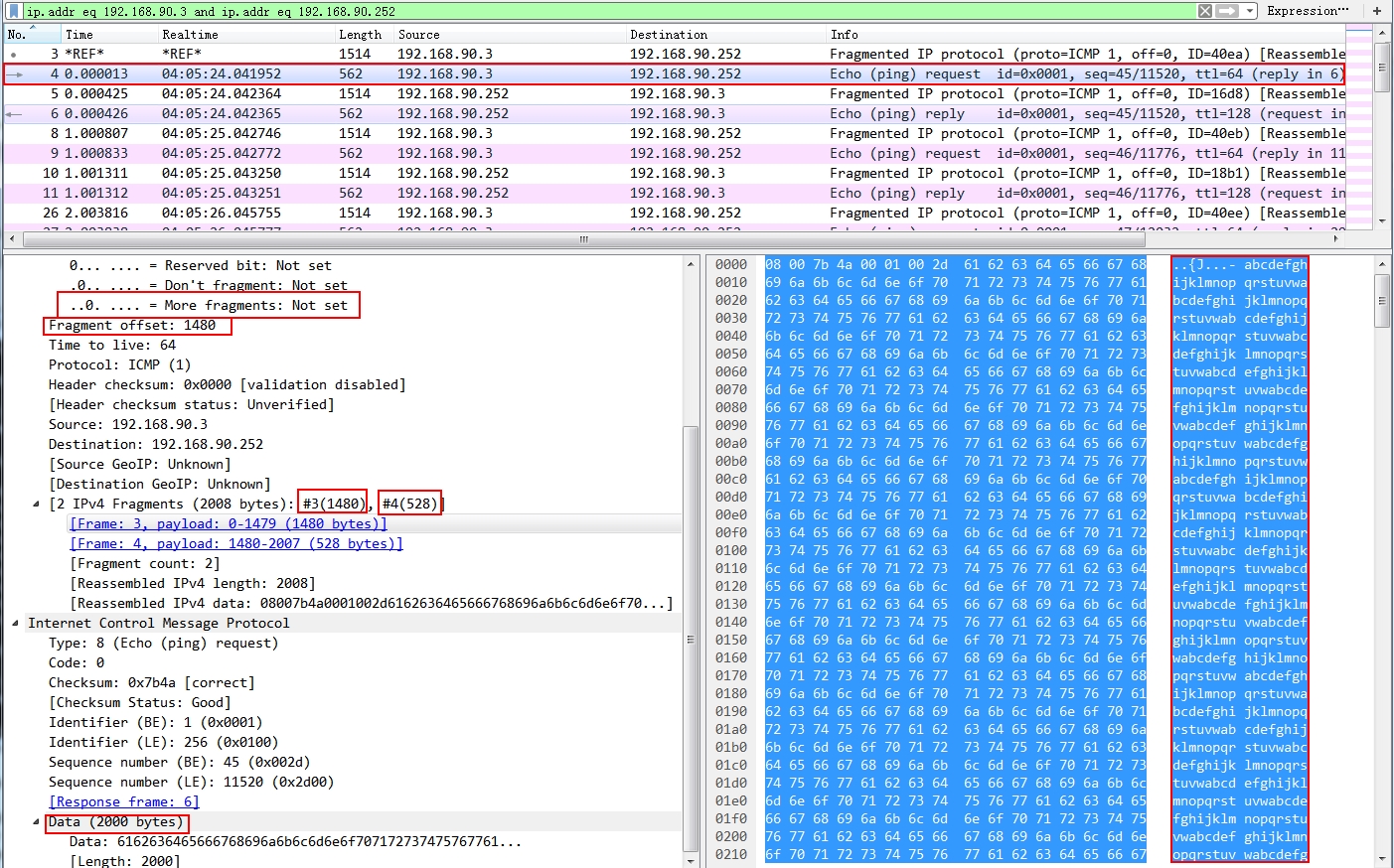
- The more fragments is set to 0 means this is the last packet.
- Fragment offset means there are 1480 bytes before this packet, which is in the packet above. If you click this line, the related hex decimal byte will be highlighted on the right:

- #3 and #4 are the number of the packet in the packets list
- Data size means the total size of the big packet.
ipv6
Basic info: http://frankfu.click/networking/networking-fundamental/ipv4-vs-ipv6.html/2/
ICMP
icmp.type==3
There are 33 types : http://www.iana.org/assignments/icmp-parameters/icmp-parameters.xhtml
E. g
| 0 | Echo Reply |
| 8 | Echo |
icmp.code==3
There are 15 types of code, you can check the link above. E.g.
| 0 | Net Unreachable |
| 1 | Host Unreachable |
| 2 | Protocol Unreachable |
| 3 | Port Unreachable |
| 4 | Fragmentation Needed and Don’t Fragment was Set |
| 5 | Source Route Failed |
source quench (SQ): If one computer sends data too fast, the other end will send source quench ICMP, ask the other to slow down.
Deprecated as of 2012 RFC 6633: A host must not send ICMP source quench.
Redirect: if you know another router which can send the data to the destination.
Path mtu: if data is sent through a serial of router, and different MTUs are set between those routers.
https://en.wikipedia.org/wiki/Path_MTU_Discovery
UDP
Common UDP protocols:
- DNS: can also be tcp
- tftp
- snmp
- rip
- early nfs
Common filters:
udp.srcport==161
udp.dstport==xxx
udp.length > xxx