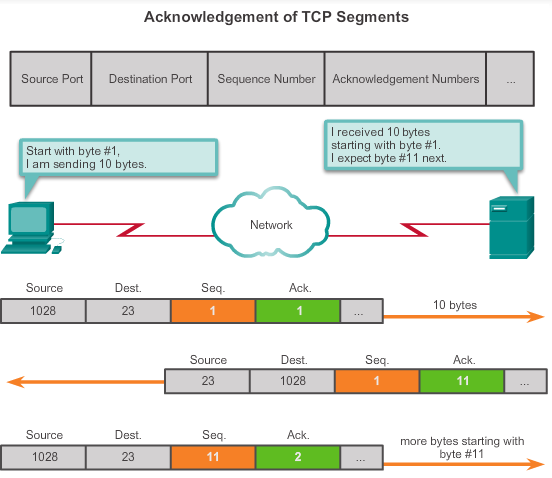
TCP
Flags:
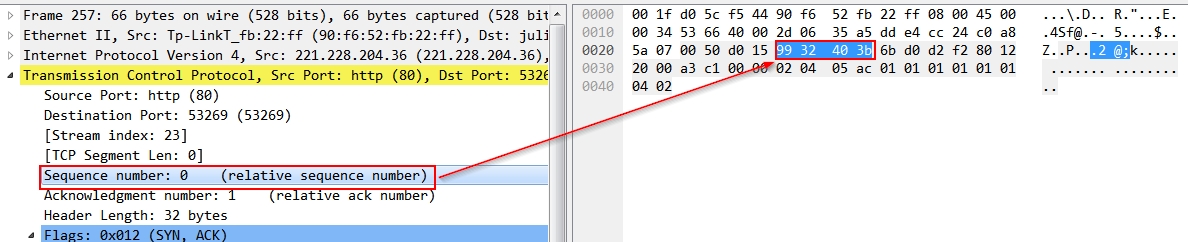
-----------------------------------------------------------------------------------------------------------------------------------------------------------
DHCP
| Value | Message type |
| 1 | DHCPDISCOVER |
| 2 | DHCPOFFER |
| 3 | DHCPREQUEST |
| 4 | DHCPDECLINE |
| 5 | DHCPACK |
| 6 | DHCPNAK |
| 7 | DHCPRELEASE |
| 8 | DHCPINFORM |
Example:
We will issue ipconfig /release and then ipconfig /renew on a windows client machine.
The wireshark captured all the DHCP related traffic:
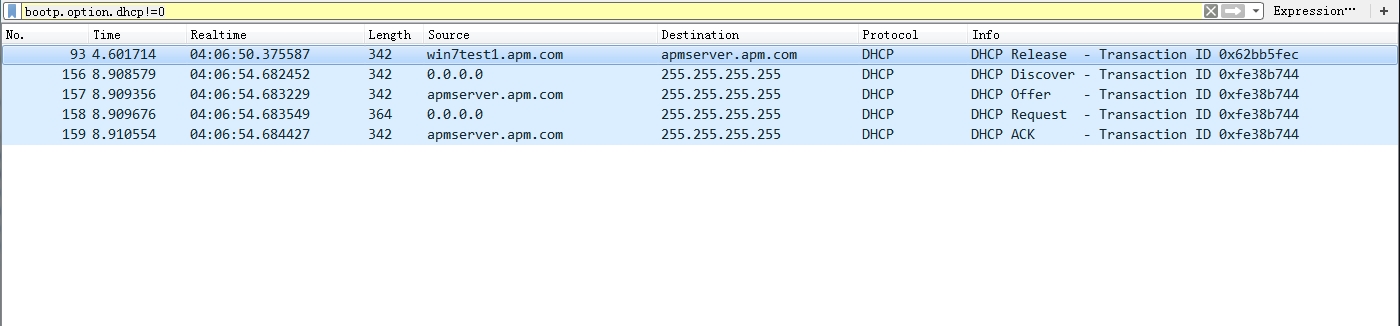
To analyze all these traffic
Request:
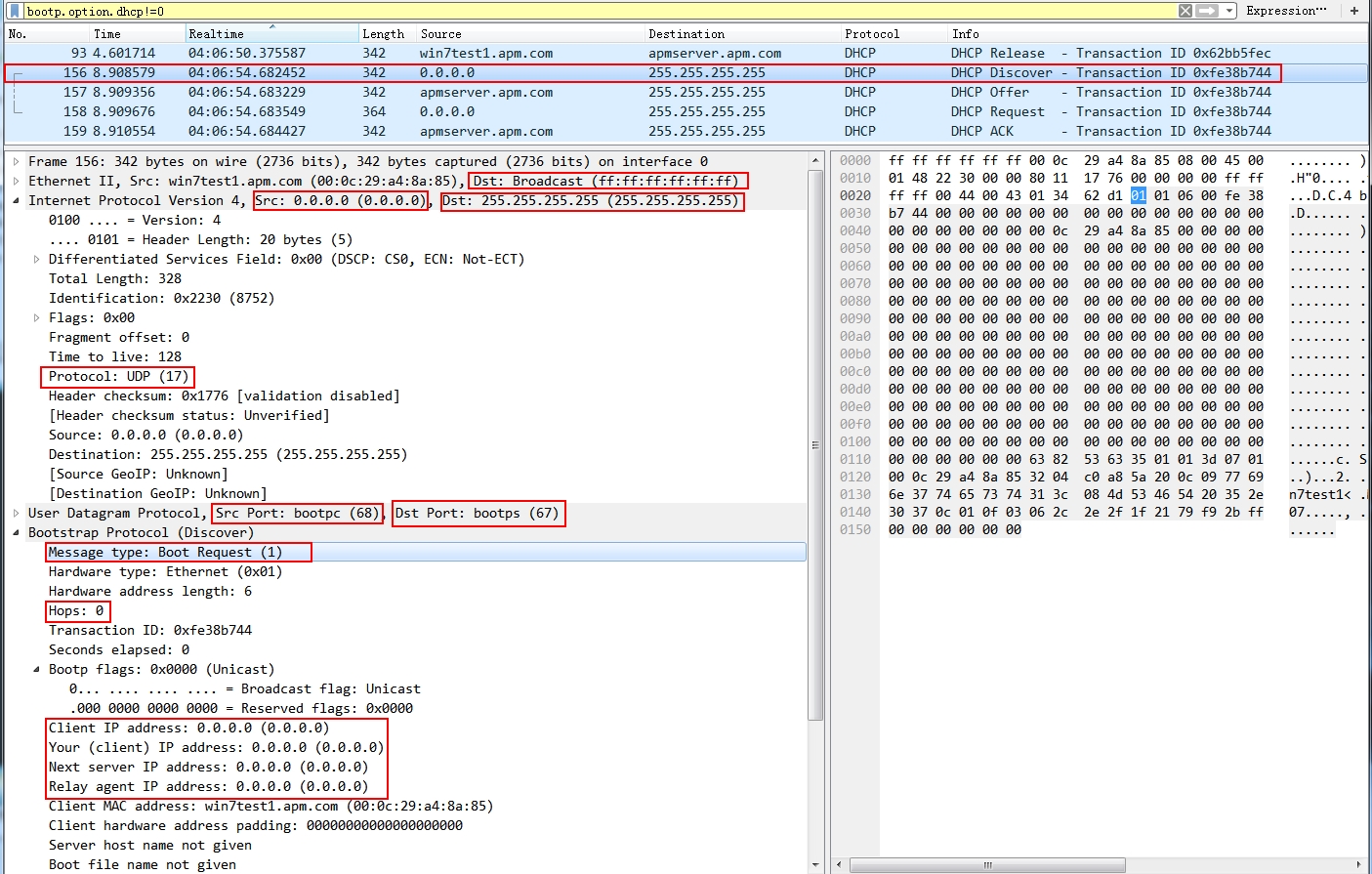
- the Destination MAC address is ff:ff:ff:ff:ff:ff
- The destination IP address is 255.255.255.255 and source IP address is 0.0.0.0
- Source Port 68, Destination port 67
- Protocol is UDP
- Message type: boot request
- Hops: 0, so the DHCP message can not go beyond default gateway.
- Also note the next server IP address and Relay agent IP address are all 0.0.0.0
Offer
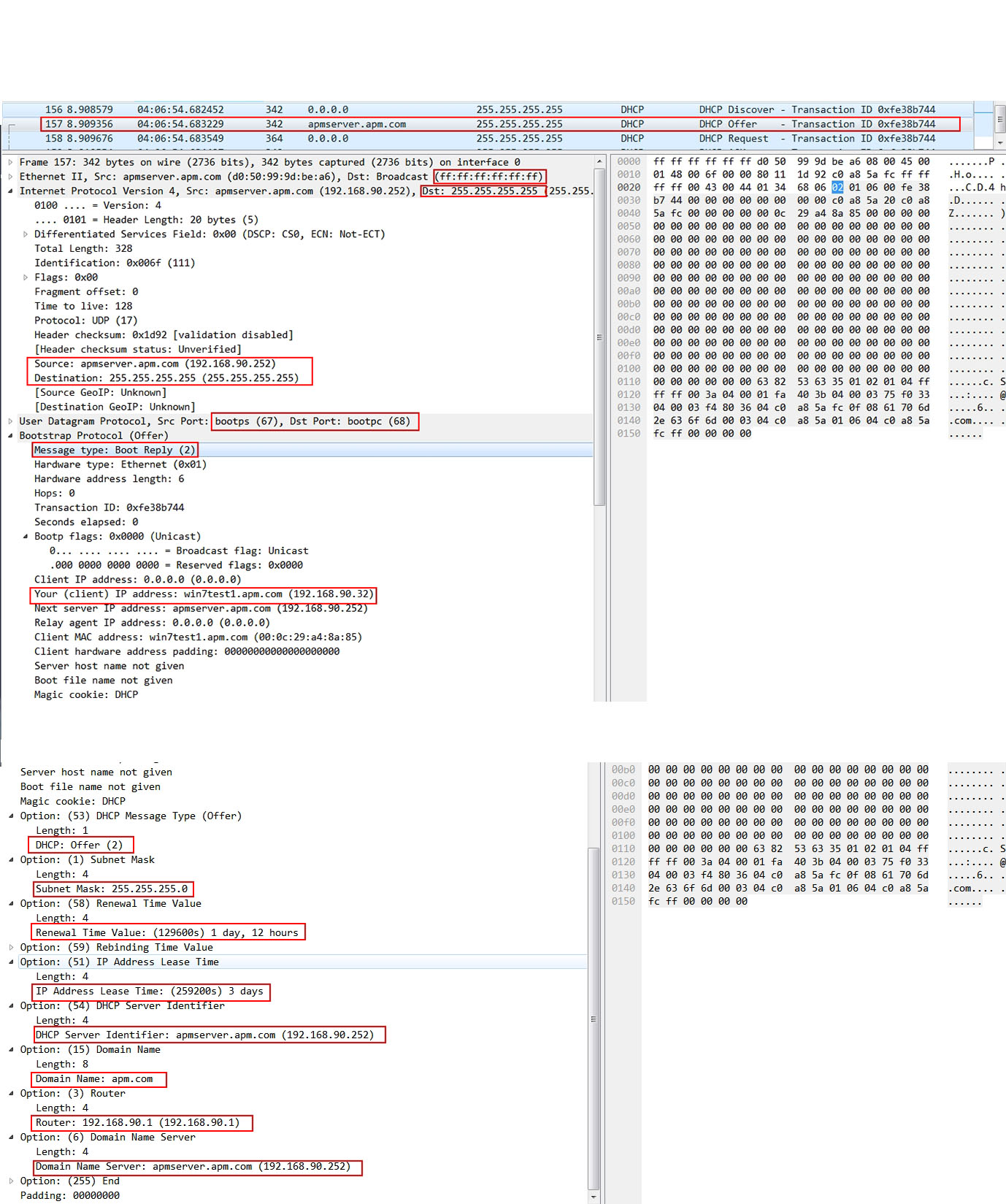
- The info tells us that the DHCP offer message is a multicast as well, no matter from the MAC address ff:ff:ff:ff:ff:ff or from the IP address 255.255.255.255.
- source port is 67 and destination port is 68.
- Message type: Boot reply, value 2.
- The offered IP address 192.168.90.32
- subnet mask: 255.255.255.0
- Lease time: 3 days, and renewal time is 1.5 days, which is when 50% lease time expired.
- DHCP server: 192.168.90.252
- Domain name: apm.com
- Router ( default gateway): 192.168.90.1
- Domain name server: 192.168.90.252
Reference
http://packetlife.net/blog/2010/jun/7/understanding-tcp-sequence-acknowledgment-numbers/
http://www.iana.org/assignments/bootp-dhcp-parameters/bootp-dhcp-parameters.xhtml