Analyse stream
There are some way to find the right stream from millions of packets.
Method 1 : Pay attention to the length:
Take telnet password sniffing as example, the length 60 usually means negotiation data
If some packet bigger than that, like 93, 156 or something else.
Method 2: Search the keyword in the data section of frame, this keyword may be the text displayed in the password entering window. enter this in the display filter: frame contains “Password” or similar frame contains “User” might be the useful frames we are looking for.
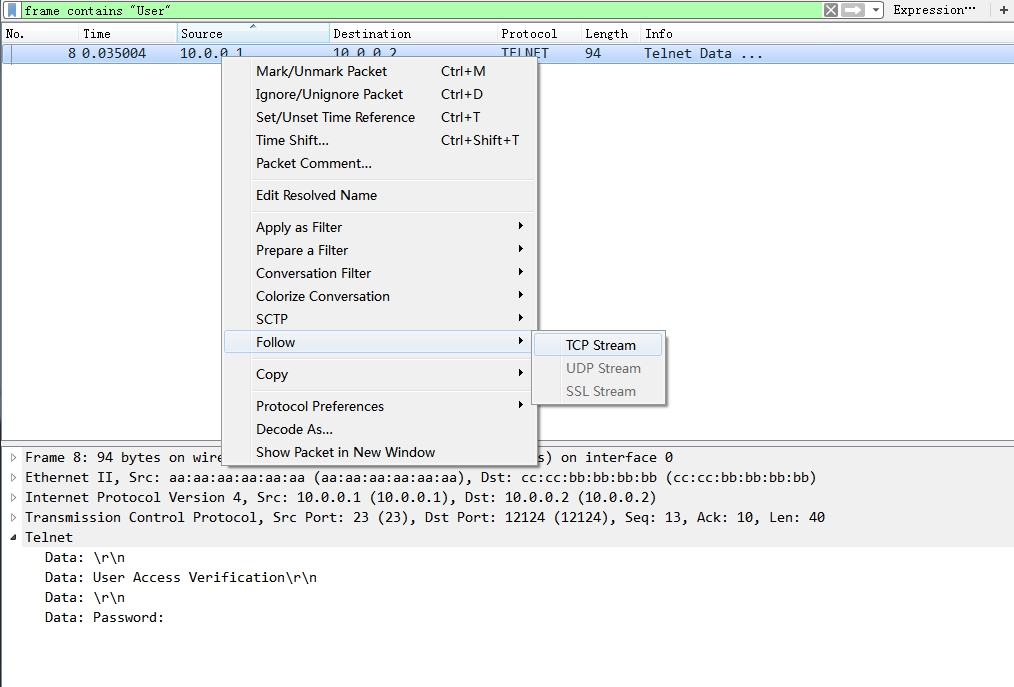
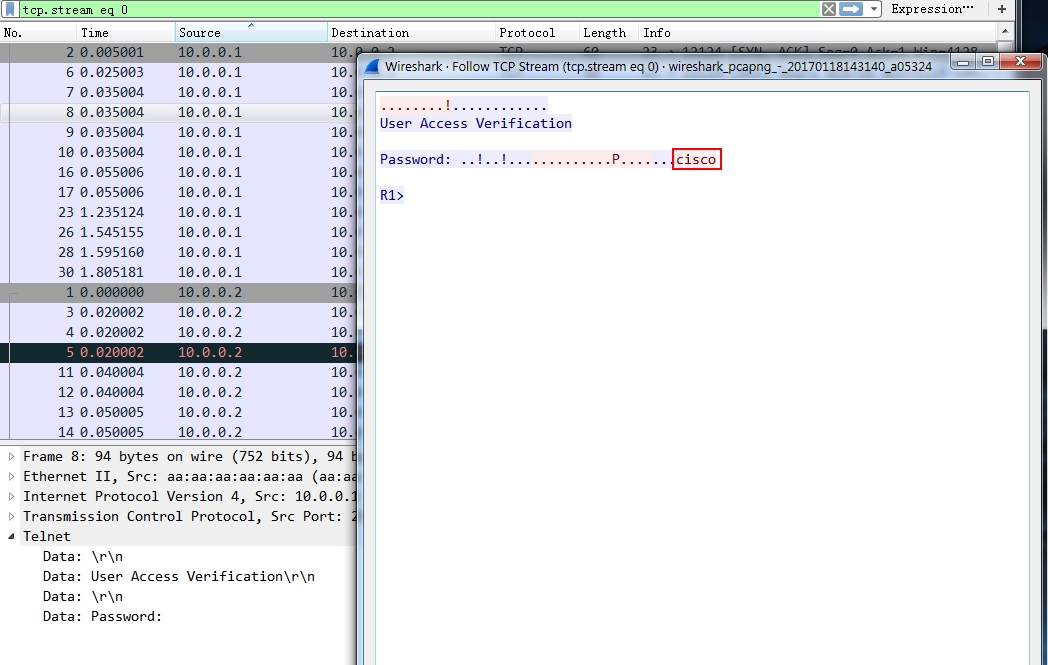
Actually, you may be interested in the frames right after that , to do this, right click the search result packet, Follow > TCP Stream. Then a new window will show the password related section.
Trace the history files
if you want to check the files, such as pdf, pictures the host has viewed on a specific website. E.g. you want to view which files has been viewed on yahoo.com. You can type frame contains "yahoo" in the display filter, hit enter, then select a packet of the stream, then click “File” in menu bar > “Export Objects > HTTP”.
Then it’s better to save all of the files to a local folder, and browse the files locally.
Stream Index
Stream index is shown only for TCP flows, but it is incremented with each conversation, even if it is a UDP conversation. If you take a closer look you’ll see that the gaps between each TCP stream number have UDP conversations that “use” the hidden numbers (usually DNS request/answer pairs).
To show all the packets with same stream index: click a TCP packet, in the Packet details pane, click “Transmission Control Protocol,…” >right click [Stream index:189] > Apply as filter > Selected