First of all, we want to catch the packets transferred between local computer and a specific website. We use 168.1.8.244 in this example.
Step1. Open wireshark.choose the second icon from the left, which is “capture options”.
In the “Capture” frame, choose the interface you will use to connect to Internet. In the “capture Filter: type” tcp port http”, this will just get the type of traffic we need in this example.Then, click “start”.
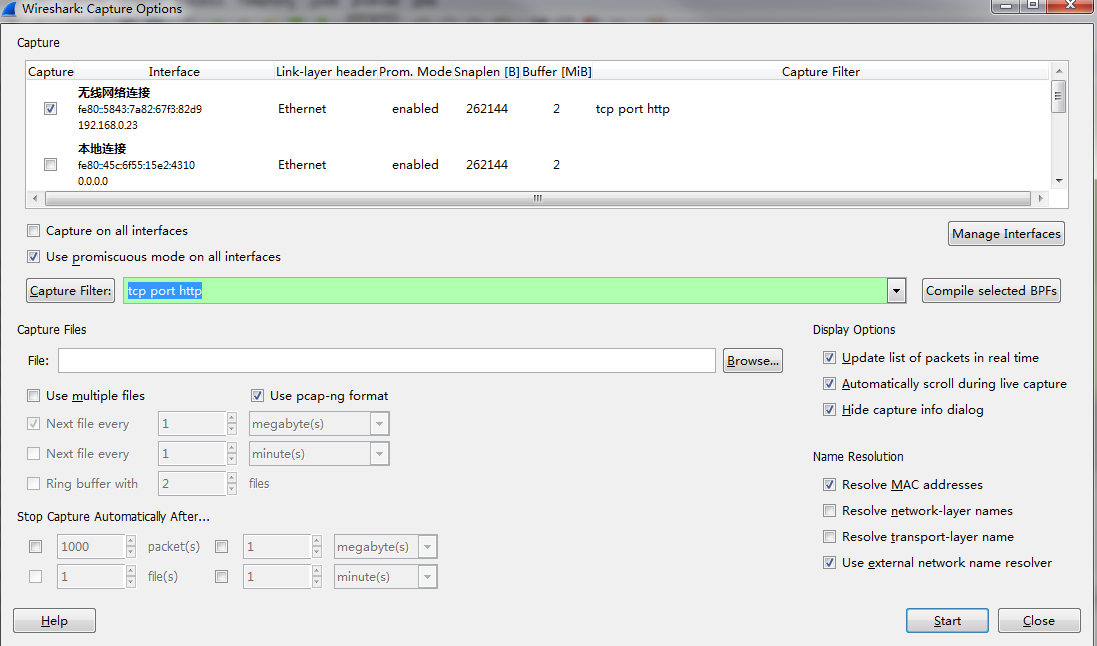
Then open a browser and visit www.abc.net.au, and you can see some records have been added in to the wireshark. If the home page show up, we can close the browser and click the stop button, which is the 4th from the left.
Step2. Open a browser, and visit www.yourdomain.com to create a record Open CMD, type:
nslookup www.yourdomain.com
The address may be one of the above address, we will see which one we will use in this connection.
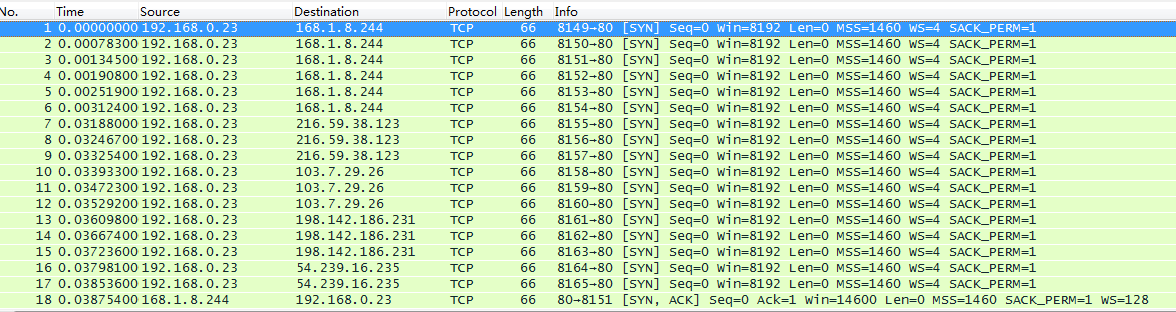
We can see that the browser used the address 168.1.8.244, so we only need to focus on the connection between local pc and this site. Click in the text field after Filter, type “ip.addr==168.1.8.244”.
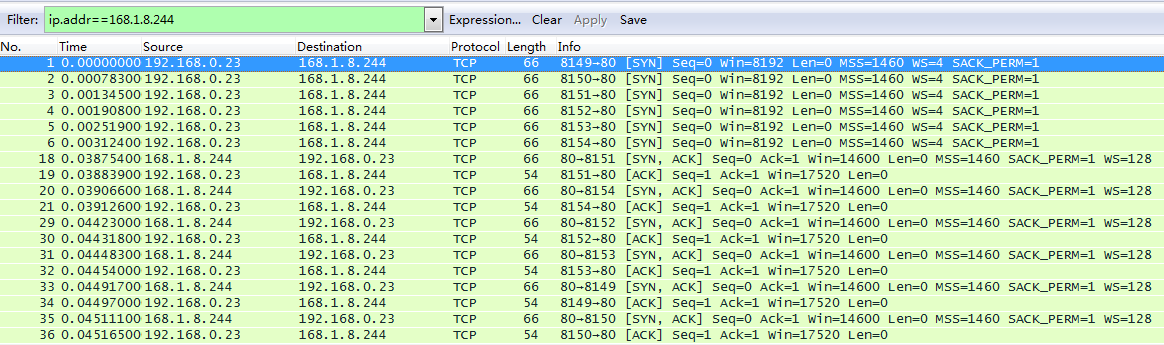
Now is the TCP three handshake in the first few lines.
We can see the connection establish request (SYN) in line 1-6. (why there are 6 times request). Then the step 2 [SYN, ACK] acknowledge 1st step, and synchronize the connection parameters. Step3, acknowledge that both sides agree to establish the connection.
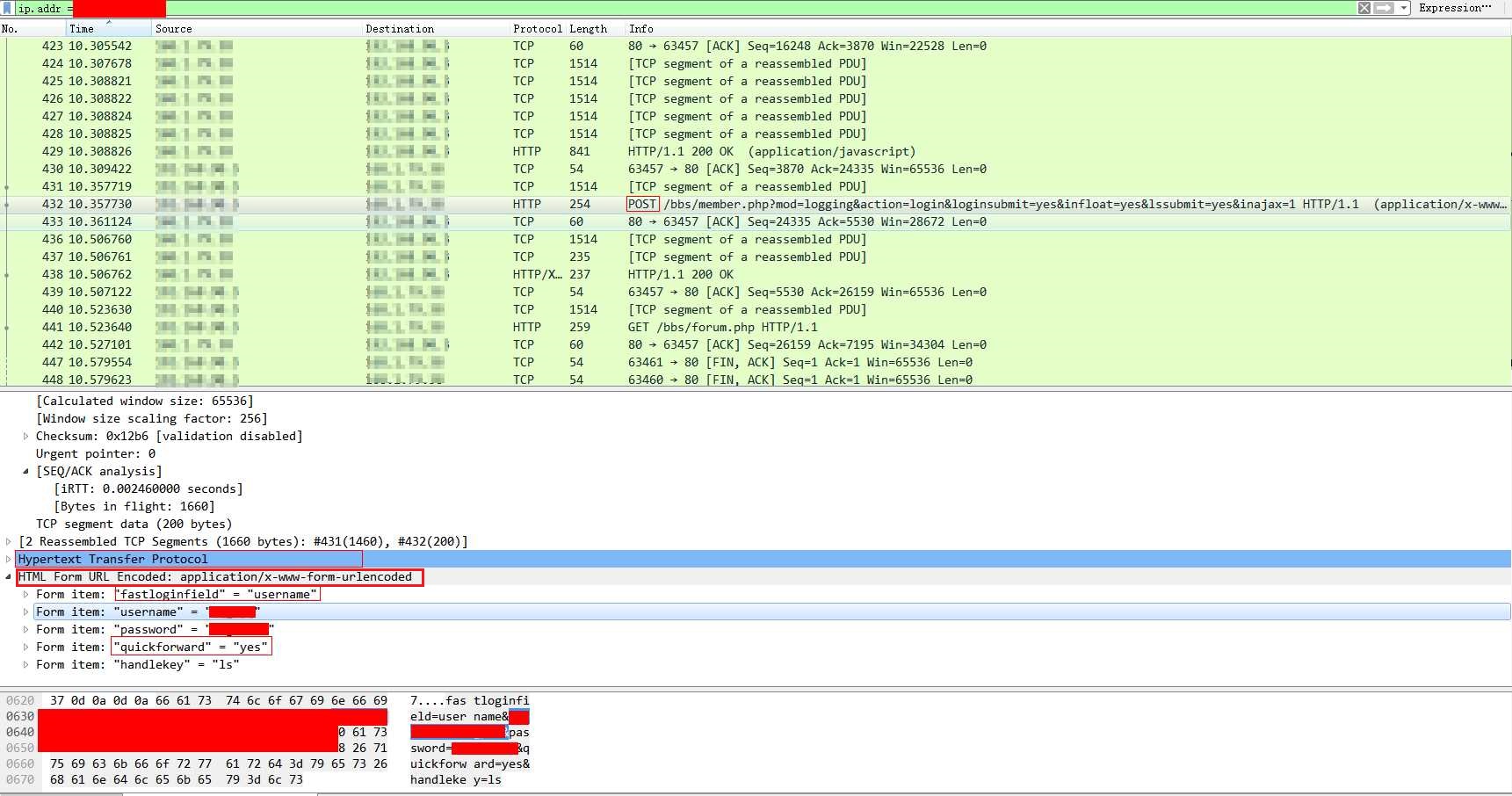
Password sniffing
for the password transferred in http, which is plain text, you can easily find the password by looking for the Post action in the Info tab. Then check the HTML Form URL Encoded: application/x-www-form-urlencoded, there are some form item. you can find the username and password there.
To capture the traffic, you would need other method, such as Man in the middle, DHCP poison, etc to redirect the traffic.