securing edge router
Edge Router Security Approaches
The edge router implementation varies depending on the size of the organization and the complexity of the required network design. Router implementations can include a single router protecting an entire inside network or a router functioning as the first line of defense in a defense-in-depth approach.
Single Router Approach
A single router connects the protected network or internal local area network (LAN), to the Internet. All security policies are configured on this device. This is more commonly deployed in smaller site implementations, such as branch and small office, home office (SOHO) sites. In smaller networks, the required security features can be supported by Integrated Services Routers (ISRs) without impeding the router’s performance capabilities.
Defense-in-Depth Approach
A defense-in-depth approach is more secure than the single router approach. It uses multiple layers of security prior to traffic entering the protected LAN. There are three primary layers of defense: the edge router, the firewall, and an internal router that connects to the protected LAN. The edge router acts as the first line of defense and is known as a screening router. After performing initial traffic filtering, the edge router passes all connections that are intended for the internal LAN to the second line of defense, which is the firewall.
The firewall typically picks up where the edge router leaves off and performs additional filtering. It provides additional access control by tracking the state of the connections and acts as a checkpoint device. By default, the firewall denies the initiation of connections from the outside (untrusted) networks to the inside (trusted) network. However, it allows the internal users to establish connections to the untrusted networks and permits the responses to come back through the firewall. It can also perform user authentication (authentication proxy) in which users must be authenticated to gain access to network resources.
Routers are not the only devices that can be used in a defense-in-depth approach. Other security tools, such as intrusion prevention systems (IPSs), web security appliances (proxy servers), and email security appliances (spam filtering) can also be implemented.
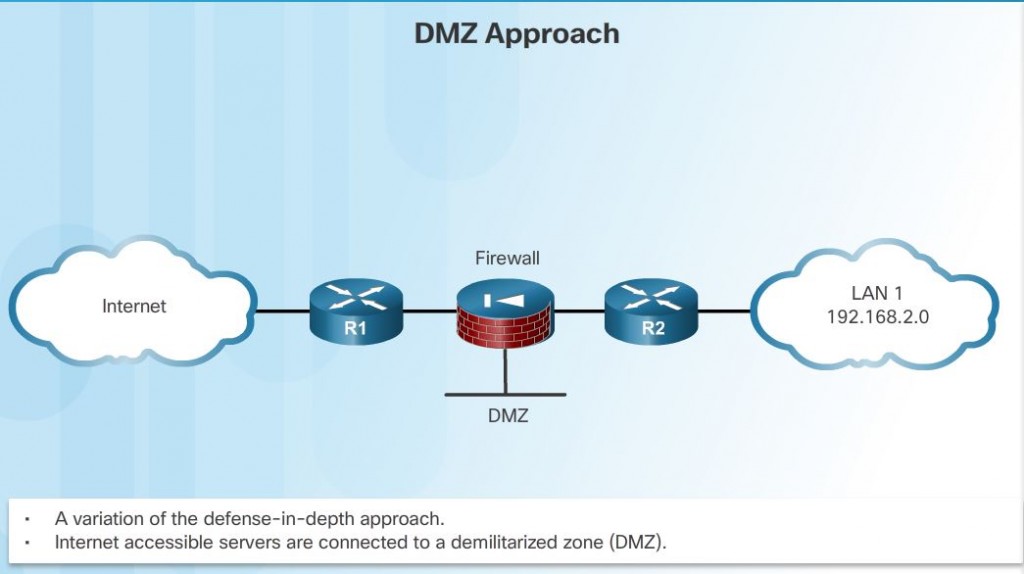
DMZ Approach
This approach includes an intermediate area, often called the demilitarized zone (DMZ). The DMZ can be used for servers that must be accessible from the Internet or some other external network. The DMZ can be set up between two routers, with an internal router connecting to the protected network and an external router connecting to the unprotected network. Alternatively, the DMZ can simply be an additional port off of a single router.
The firewall is located between the protected and unprotected networks. The firewall is set up to permit the required connections, such as HTTP, from the outside (untrusted) networks to the public servers in the DMZ. The firewall serves as the primary protection for all devices in the DMZ.
Three Areas of Router Security
Securing the edge router is a critical first step in securing the network. If there are other internal routers, they also must be securely configured. Three areas of router security must be maintained:
Physical Security
Provide physical security for the routers:
- Place the router and physical devices that connect to it in a secure locked room that is accessible only to authorized personnel, is free of electrostatic or magnetic interference, has fire suppression, and has temperature and humidity controls.
- Install an uninterruptible power supply (UPS) or diesel backup power generator, and keep spare components available. This reduces the possibility of a network outage from power loss.
Operating System Security
There are a few procedures involved in securing the features and performance of router operating systems:
- Configure the router with the maximum amount of memory possible. The availability of memory can help mitigate risks to the network from some denial of service (DoS) attacks while supporting the widest range of security services.
- Use the latest, stable version of the operating system that meets the feature specifications of the router or network device. Security and encryption features in an operating system are improved and updated over time, which makes it critical to have the most up-to-date version.
- Keep a secure copy of router operating system images and router configuration files as backups.
Router Hardening
Eliminate potential abuse of unused ports and services:
- Secure administrative control. Ensure that only authorized personnel have access and that their level of access is controlled.
- Disable unusedports and interfaces. Reduce the number of ways a device can be accessed.
- Disable unnecessary services. Similar to many computers, a router has services that are enabled by default. Some of these services are unnecessary and can be used by an attacker to gather information about the router and the network, which is then leveraged later in an exploitation attack.
Securing administrative access to:
- Restrict device accessibility – Limit the accessible ports, restrict the permitted communicators, and restrict the permitted methods of access.
- Log and account for all access – Record anyone who accesses a device, what happened during the access, and when the access occurred for auditing purposes.
- Authenticate access – Ensure that access is granted only to authenticated users, groups, and services. Limit the number of failed login attempts and the time allowed between logins.
- Authorize actions – Restrict the actions and views permitted by any particular user, group, or service.
- Present legal notification – Display a legal notice, developed in conjunction with company legal counsel, for interactive sessions.
- Ensure the confidentiality of data – Protect locally stored and sensitive data from being viewed and copied. Consider the vulnerability of data in transit over a communication channel to sniffing, session hijacking, and man-in-the-middle (MITM) attacks.
Precautions should be taken for Remote Access:
- Encrypt all traffic between the administrator computer and the router. For example, instead of using Telnet, use SSH version 2; or instead of using HTTP, use HTTPS.
- Establish a dedicated management network. The management network should include only identified administration hosts and connections to a dedicated interface on the router.
- Configure a packet filter to allow only the identified administration hosts and preferred protocols to access the router. For example, permit only SSH requests from the IP address of an administration host to initiate a connection to the routers in the network.
- Configure and establish a VPN connection to the local network before connecting to a router management interface.
Strong password
Attackers can also use a password cracker, such as L0phtCrack or Cain & Abel to discover passwords.
Password-leading spaces are ignored but spaces after the first character are not ignored. One method to create a strong password is to use a blank space in the password or create a phrase made of many words. This is called a passphrase. A passphrase is often easier to remember than a complex password. A passphrase is longer and more difficult to guess than a password.
Increase the access security
- By default, the password length minimum is six characters. To increase the minimum length, use the
security passwords min-lengthlengthglobal configuration mode command.
- By default, with the exception of the password generated by the enable secret command, all Cisco router passwords are stored in plaintext in the router startup and running configuration files. To encrypt all plaintext passwords, use the
service password-encryptioncommand in global configuration mode. - By default, an administrative interface stays active and logged in for 10 minutes after the last session activity. To disable unattended connections, use the
exec-timeout minutes [seconds]command in line configuration mode.
Security password algorithm
MD5 hashes are no longer considered secure because attackers can reconstruct valid certificates. This can allow attackers to spoof any website. The enable secret password, uses an MD5 hash by default. Therefore, it is now recommended that you configure all secret passwords using either type 8 or type 9 passwords. use enable secret level password . Type 8 and type 9 were introduced in Cisco IOS 15.3(3)M. Type 8 and type 9 use SHA encryption. Because type 9 is slightly stronger than type 8, it will be used throughout this course whenever it is allowed by the Cisco IOS.
You cannot simply enter enable secret 9 and the unencrypted password. To use this form of the command, you must paste in the encrypted password, which can be copied from another router configuration. To enter an unencrypted password, use the enable algorithm-type command syntax.
enable algorithm-type {md5| scrypt | sha256 } secret unencrypted-password
- md5: type5, selects the message digest algorithm 5 (MD5) as the hashing algorithm
- scrypt: type9 selects scrypt as the hashing algorithm.
- sha256: type8 seletcts password-base key derivation function2 (PBKDF2) with secure has algorithm, 256-bits(SHA-256) as the hashing algorithm.
If you simply enter a user with the username secret command, the default encryption will be MD5. Use the username name algorithm-type command to specify type 9 encryption.
To specify a type of the encryption:
router(ocnfig)# username name algorithm-type (md5| scrypt | sha256} secret unencrypted-password
For backwards compatibility reasons, the enable password, username password, and line password commands are available in the Cisco IOS. These commands use no encryption by default. At best, they can only use type 7 encryption.
Enhancing login process
This only slowing down attacks:
- Implement delays between successive login attempts.
- Enable login shutdown if DoS attacks are suspected.
- Generate system-logging messages for login detection.
Access control lists (ACLs) can be used to permit legitimate connection from addresses of known system administrators.
To increase the security of virtual login connections.
- The
login block-for seconds attempts tries within secondscommand can defend against DoS attacks by disabling logins after a specified number of failed login attempts. - The
login quiet-mode access-class {acl-name|acl-number}command maps to an ACL that identifies the permitted hosts. This ensures that only authorized hosts can attempt to login to the router. - The
login delay secondscommand specifies a number of seconds the user must wait between unsuccessful login attempts. - The
login on-success log [every login]andlogin on-failure log [every login]commands log successful and unsuccessful login attempts.
Note: These login enhancements do not apply to console connections. When dealing with console connections, it is assumed that only authorized personnel have physical access to the devices.
These login enhancements can only be enabled if the local database is used for authentication for local and remote access. If the lines are configured for password authentication only, then the enhanced login features are not enabled.
Login Enhancements
login block-for seconds attempts tries within seconds
- This command must be issued before any other login command can be used.
- This command can hep provide DoS detection and prevention
The login block-for command monitors login device activity and operates in two modes:
- Normal mode – This is also known as watch mode. The router keeps count of the number of failed login attempts within an identified amount of time.
- Quiet mode – If the number of failed logins exceeds the configured threshold, all login attempts using Telnet, SSH, and HTTP are denied for the time specified in the login block-for command.
When quiet mode is enabled, all login attempts, including valid administrative access, are not permitted.
However, to provide critical hosts, such as specific administrative hosts access at all times, this behavior can be overridden using an ACL. The ACL is created and identified using the login quiet-mode access-class command:
R1(config)#ip access-list standard Permit-admin
R1(config-std-nacl)# remark permit only administrative hosts
R1(config-std-nacl)# permit 192.168.10.10
R1(config-std-nacl)# exit
R1(config)# login quiet-mode access-class Permit-admin
So only the host 192.168.10.10, which match the Permit-admin statement are exempt from the quiet mode.
To make it more difficult for an attacker, the delay time between login attempts can be increased using the login delay command, the default delay is 1 second.
R1(config)# login delay 3
This example configure a delay of 3 seconds in between successive login attempts.
- Helps mitigate dictionary attacks
- This is an optional command.
Steps for Configuring SSH
There are four requirements the router must meet before configuring SSH:
- Runs a Cisco IOS release that supports SSH
- Uses a unique hostname
- Contains the correct domain name of the network
- Configured for local authentication or AAA services
Five steps needed to configure a Cisco router to support SSH with local authentication:
Step 1. Configure the IP domain name of the network using the ip domain-name domain-name command in global configuration mode.
Step 2. One-way secret keys must be generated so a router can encrypt the SSH traffic. These keys are referred to as asymmetric keys. Cisco IOS software uses the Rivest, Shamir, and Adleman (RSA) algorithm to generate keys. To create the RSA key, use the crypto key generate rsa general-keys modulus modulus-size command in global configuration mode. The modulus determines the size of the RSA key and can be configured from 360 bits to 4,096 bits. The larger the modulus, the more secure the RSA key. However, keys with large modulus values take slightly longer to generate, encrypt, and decrypt. The minimum recommended modulus key length is 1,024 bits.
Note: SSH is automatically enabled after the RSA keys are generated.
Step 3. Although not technically required, because Cisco routers default to SSH version 2, you can manually configure version 2 with the ip ssh version 2 global configuration command. The original version has known vulnerabilities.
Step 4. Ensure that there is a valid local database username entry. If not, create one using the username name algorithm-type scrypt secret secret command.
Step 5. Enable vty inbound SSH sessions using the line vty commands, login local and transport input ssh.
Modify SSH configuration
To verify SSH and display the generated keys, use the show crypto key mypubkey rsa command in privileged EXEC mode.
If there are existing key pairs, it is recommended that they are overwritten using the crypto key zeroize rsa command.
To verify the optional SSH command settings, use the show ip ssh command.
Use the ip ssh time-out seconds global configuration mode command to modify the default 120-second timeout interval.
By default, a user logging in has three attempts to enter the correct password before being disconnected. To configure a different number of consecutive SSH retries, use the ip ssh authentication-retries integer global configuration mode command.
Connect to SSH server: ssh -l username url/IP_address
16 privileged mode
Level 0: Predefined for user-level access privileges. Seldom used, but includes five commands: disable, enable, exit, help, and logout.
Level 1: The default level for login with the router prompt Router>. A user cannot make any changes or view the running configuration file.
Levels 2 –14: May be customized for user-level privileges. Commands from lower levels may be moved up to another higher level, or commands from higher levels may be moved down to a lower level.
Level 15: Reserved for the enable mode privileges (enable command). Users can change configurations and view configuration files.
To assign commands to a custom privilege level, use the privilege global configuration mode command:
privilege exec {level level | reset} command
- mode: specifies the configuration mode. Use the privilege ? to see a complete list of router configuration modes available on your router.
- level(optional): enables setting a privilege level with a specified command.
- reset(optional): resets the privilege level of a command.
- command: argument to use when you want to reset the privilege level
By default, the Cisco IOS software CLI has two levels of access to commands:
- User EXEC mode (privilege level 1) – Provides the lowest EXEC mode user privileges and allows only user-level commands available at the router> prompt.
- Privileged EXEC mode (privilege level 15) – Includes all enable-level commands at the router# prompt.
Configure and assign privilege levels
To configure a privilege level with specific commands, use the privilege exec level level [command].
R1(config)# privilege exec level 5 ping
R1(config)#enable algorithm-type scrypt secret level 5 cisco5
R1(config)#username SUPPORT privilege 5 algorithm-type scrypt secret cisco5
The command above have the effects: Privilege level 5 has access to all the commands available for the predefined level 1 and the ping command.
There are two methods for assigning passwords to the different privilege levels:
- To a user that is granted a specific privilege level, use the
username name privilege level secret passwordglobal configuration mode command
- To the privilege level, use the enable secret level level password global configuration mode command
Note: Both the username secret and the enable secret commands are configured for type 9 encryption.
The use of privilege levels has its limitations:
- No access control to specific interfaces, ports, logical interfaces, and slots on a router.
- Commands available at lower privilege levels are always executable at higher levels.
- Commands specifically set at a higher privilege level are not available for lower privileged users.
- Assigning a command with multiple keywords allows access to all commands that use those keywords. For example, allowing access to show ip route allows the user access to all show and show ip commands.
Note: If an administrator must create a user account that has access to most but not all commands, privilege exec statements need to be configured for every command that must be executed at a privilege level lower than 15.