Review on ACLs
Historically, the type of ACL could be identified by the number:
|
|
|
|---|---|
|
IP |
1-99, 1300-1999 |
|
Extended IP |
100-199, 2000-2699 |
|
Ethernet type code |
200-299 |
|
Ethernet address |
700-799 |
|
Transparent bridging (protocol type) |
200-299 |
|
Transparent bridging (vendor code) |
700-799 |
|
Extended transparent bridging |
1100-1199 |
|
DECnet and extended DECnet |
300-399 |
|
XNS |
400-499 |
|
Extended XNS |
500-599 |
|
AppleTalk |
600-699 |
|
Source-route bridging (protocol type) |
200-299 |
|
Source-route bridging (vendor code) |
700-799 |
|
IPX |
800-899 |
|
Extended IPX |
900-999 |
|
IPX SAP |
1000-1099 |
|
Standard VINES |
1-100 |
|
Extended VINES |
101-200 |
|
Simple VINES |
201-300 |
Today, when classifying traffic, the most common types of ACLs use IPv4 and IPv6 addresses and Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) port numbers.
http://frankfu.click/networking/cisco/ccna/access-control-list/
scenario need to consider
1. Antispoofing with ACLs
IP address spoofing overrides the normal packet creation process by inserting a custom IP header with a different source IP address. Attackers can hide their identity by spoofing the source IP address.
There are many well-known classes of IP addresses that should never be seen as source IP addresses for traffic entering an organization’s network. e.g.
- All zeros addresses ( can be DHCP discovery message )
- Broadcast addresses
- Local host addresses (127.0.0.0/8)
- Reserved private addresses (RFC 1918)
- IP multicast address range (224.0.0.0/4)
2. Permit necessary traffic
An effective strategy for mitigating attacks is to explicitly permit only certain types of traffic through a firewall. For example, Domain Name System (DNS), Simple Mail Transfer Protocol (SMTP), and FTP are services that often must be allowed through a firewall.
3. Mitigating ICMP abuse
Hackers can use Internet Control Message Protocol (ICMP) echo packets (pings) to discover subnets and hosts on a protected network and to generate DoS flood attacks. Hackers can use ICMP redirect messages to alter host routing tables. Both ICMP echo and redirect messages should be blocked inbound by the router.
Several ICMP messages are recommended for proper network operation and should be allowed into the internal network:
- Echo reply – Allows users to ping external hosts.
- Source quench – Requests that the sender decrease the traffic rate of messages.
- Unreachable – Generated for packets that are administratively denied by an ACL.
Several ICMP messages are required for proper network operation and should be allowed to exit the network:
- Echo – Allows users to ping external hosts.
- Parameter problem – Informs the host of packet header problems.
- Packet too big – Enables packet maximum transmission unit (MTU) discovery.
- Source quench – Throttles down traffic when necessary.
As a rule, block all other ICMP message types outbound.
4. Mitigating SNMP exploites
These security measures are helpful, but the most effective means of exploitation prevention is to disable the SNMP server on IOS devices for which it is not required. Use the command no snmp-server to disable SNMP on a router.
ICMP quench Message
The ICMP-Source quench message is a request to decrease the traffic rate of data messages sent to an internet destination.
The IP header plus the first 8 bytes of the original datagram’s data is returned to the sender. This data is used by the host to match the message to the appropriate process. If a higher level protocol uses port numbers, they are assumed to be in the first 64 data bits of the original datagram’s data.
This message is not generated in response to a datagram destined for a multicast address.
RFC 792, pages 10 and 11:
A gateway MAY discard internet datagrams if it does not have the buffer space needed to queue the datagrams for output to the next network on the route to the destination network.
If a gateway discards a datagram, it may send a source quench message to the internet source host of the datagram.
A destination host may also send a source quench message if datagrams arrive too fast to be processed.
The source quench message is a request to the host to cut back the rate at which it is sending traffic to the internet destination. The gateway may send a source quench message for every message that it discards. On receipt of a source quench message, the source host should cut back the rate at which it is sending traffic to the specified destination until it no longer receives source quench messages from the gateway. The source host can then gradually increase the rate at which it sends traffic to the destination until it again receives source quench messages.
The gateway or host MAY send the source quench message when it approaches its capacity limit rather than waiting until the capacity is exceeded. This means that the data datagram which triggered the source quench message may be delivered.
Code 0 may be received from a gateway or a host.
Introducing IPv6 ACLs
Why IPV6 ACLs?
IPv4 was designed without several modern-day network requirements:
- Security – IP Security (IPsec)
- Device roaming – Mobile IP
- Quality of service – Resource Reservation Protocol (RSVP)
- Address scalability – DHCP, Network Address Translation (NAT), classless interdomain routing (CIDR), variable-length subnet masking (VLSM)
IPv4 will coexist with IPv6 and then gradually be replaced by IPv6. This creates potential security holes. An example of a security concern is attackers leveraging IPv4 to exploit IPv6 in dual stack. Dual stack is an integration method in which a device has implementation and connectivity to both IPv4 and IPv6 networks. Attackers can accomplish stealth attacks that result in trust exploitation by using dual stacked hosts, rogue Neighbor Discovery Protocol (NDP) messages, and tunneling techniques.
Teredo volnerability
Teredo tunneling, for example, is an IPv6 transition technology that provides automatic IPv6 address assignment when IPv4/IPv6 hosts are located behind IPv4 network address translation (NAT) devices. It accomplishes this by embedding the IPv6 packets inside IPv4 UDP packets. The attacker gains a foothold in the IPv4 network. The compromised host sends rogue router advertisements, which triggers dual stacked hosts to obtain an IPv6 address. The attacker can then use this foothold to move around or pivot inside the network. The attacker can compromise additional hosts before sending traffic back out of the network.
IPv6 ACL
All IPv6 ACLs must be configured with a name. IPv6 ACLs allow filtering based on source and destination addresses that are traveling inbound and outbound to a specific interface. They also support traffic filtering based on IPv6 option headers and optional, upper-layer protocol type information for finer granularity of control, similar to extended ACLs in IPv4. To configure an IPv6 ACL, use the ipv6 access-list command to enter into IPv6 ACL configuration mode. Next, use the syntax shown bellow to configure each access list entry to specifically permit or deny traffic. Apply an IPv6 ACL to an interface with the ipv6 traffic-filter command.
|
Step 1 |
ipv6 access-list access-list-name |
Define an IPv6 access list name, and enter IPv6 access-list configuration mode. |
|
Step 2 |
Deny | permit protocol { source-ipv6-prefix / prefix-length | any | host source-ipv6-address } [ operator [ port-number ] ] { destination-ipv6-prefix/ prefix-length | any | host destination-ipv6-address } [ operator [ port-number ]] |
|
- Enter deny or permit to specify whether to deny or permit the packet if conditions are matched. These are the conditions:
- For protocol, enter the name or number of an Internet protocol: ahp, esp, icmp, ipv6, pcp, sctp, tcp, or udp, or an integer in the range 0 to 255 representing an IPv6 protocol number. For additional specific parameters for ICMP, TCP, and UDP, see Steps 3b through 3d.
- The source-ipv6-prefix / prefix-length or destination-ipv6-prefix / prefix-length is the source or destination IPv6 network or class of networks for which to set deny or permit conditions, specified in hexadecimal and using 16-bit values between colons (see RFC 2373).
Note Although the CLI help shows a prefix-length range of /0 to /128, the switch supports IPv6 address matching only for prefixes in the range of /0 to /64 and EUI-based /128 prefixes for aggregatable global unicast and link-local host addresses.
- Enter any as an abbreviation for the IPv6 prefix ::/0.
- For host source-ipv6-address o r destination-ipv6-address, enter the source or destination IPv6 host address for which to set deny or permit conditions, specified in hexadecimal using 16-bit values between colons.
- An IPv6 ACL contains an implicit deny ipv6 any.
- Each IPv6 ACL also contains implicit permit rules to enable IPv6 neighbor discovery. The IPv6 NDP requires the use of the IPv6 network layer to send neighbor advertisements (NAs) and neighbor solicitations (NSs). If an administrator configures the deny ipv6 any command without explicitly permitting neighbor discovery, then the NDP will be disabled.
firewall
Benefits of using a firewall in a network:
- Prevent the exposure of sensitive hosts, resources, and applications to untrusted users.
- Sanitize protocol flow, which prevents the exploitation of protocol flaws.
- Block malicious data from servers and clients.
- Reduce security management complexity by off-loading most of the network access control to a few firewalls in the network.
Firewalls also present some limitations:
- A misconfigured firewall can have serious consequences for the network, such as becoming a single point of failure.
- The data from many applications cannot be passed over firewalls securely.
- Users might proactively search for ways around the firewall to receive blocked material, which exposes the network to potential attack.
- Network performance can slow down.
- Unauthorized traffic can be tunneled or hidden as legitimate traffic through the firewall.
Stateless
These early firewalls inspected packets to see if they matched sets of rules, and then chose to forward or drop the packets accordingly. This type of packet filtering, known as stateless filtering, occurs regardless of whether a packet is part of an existing flow of data. Each packet is filtered based solely on the values of certain parameters in the packet header, which is similar to how ACLs filter packets.
Stateful
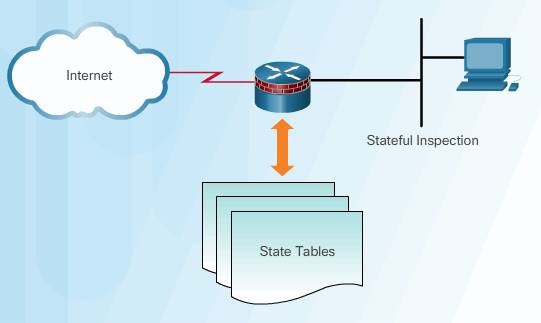
In 1989, AT&T Bell Laboratories developed the first stateful firewall. Stateful firewalls evaluate the state of connections in data flows to filter packets. The stateful firewall is able to determine if a packet belongs to an existing flow of data. Static rules, as in packet filter firewalls, are supplemented with dynamic rules created in real time to define these active flows. Stateful firewalls help to mitigate DoS attacks that exploit active connections through a networking device.
Stateful firewalls are the most versatile and the most common firewall technologies in use. Stateful firewalls provide stateful packet filtering by using connection information maintained in a state table.
Stateful filtering is a firewall architecture that is classified at the network layer. It also analyzes traffic at OSI Layer 4 and Layer 5.
Unlike a stateless firewall that uses static packet filtering, stateful filtering tracks each connection traversing all interfaces of the firewall and confirms that they are valid. Stateful firewalls use a state table to keep track of the actual communication process. The firewall examines information in the headers of Layer 3 packets and Layer 4 segments. For example, the firewall looks at the TCP header for synchronize (SYN), reset (RST), acknowledgment (ACK), finish (FIN), and other control codes to determine the state of the connection.
Each time a TCP or UDP connection is established for inbound or outbound connections, a stateful firewall logs the information in a state table for that specific flow.
Example:
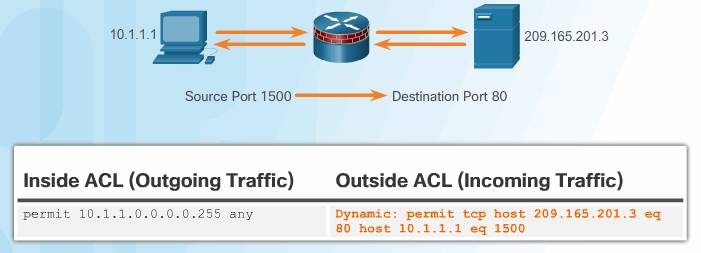
For example, in Figure host 10.1.1.1 is requesting a web page from the server at 209.165.201.3. The stateful packet filter firewall retains certain details by saving the state of the request in the state table. In this example, the router dynamically added an access control entry for return traffic sourced from server 209.165.201.3, on port 80, and destined to host 10.1.1.1 on port 1500.
Note: This is the way that previous versions of IOS firewall implemented stateful behavior. Newer Cisco IOS Firewall implementations use the zone-based approach discussed later in the chapter.
Benefits:
- Stateful firewalls are often used as a primary means of defense by filtering unwanted, unnecessary, or undesirable traffic.
- Stateful firewalls strengthen packet filtering by providing more stringent control over security.
- Stateful firewalls improve performance over packet filters or proxy servers.
- Stateful firewalls defend against spoofing and DoS attacks by determining whether packets belong to an existing connection or are from an unauthorized source.
- Stateful firewalls provide more log information than a packet filtering firewall.
Limitations:
- Stateful firewalls cannot prevent Application Layer attacks because they do not examine the actual contents of the HTTP connection.
- Not all protocols are stateful. For example, UDP and ICMP do not generate connection information for a state table, and, therefore, do not garner as much support for filtering.
- It is difficult to track connections that use dynamic port negotiation. Some applications open multiple connections. This requires a whole new range of ports that must be opened to allow this second connection.
- Stateful firewalls do not support user authentication.
Difference between stateful and stateless:
Stateful firewall – A Stateful firewall is aware of the connections that pass through it. It adds and maintains information about a user’s connections in a state table, referred to as a connection table. It then uses this connection table to implement the security policies for users connections. An example of the stateful firewall is PIX, ASA, Checkpoint.
Stateless firewalls – (Packet Filtering) Stateless firewalls, on the other hand, does not look at the state of connections but just at the packets themselves. An example of a packet filtering firewall is the Extended Access Control Lists on Cisco IOS Routers.
Types of firewall
A firewall system can be composed of many different devices and components. One component is traffic filtering, which is what most people commonly call a firewall. The following three firewalls are covered in this chapter:
Packet filtering firewall
Typically a router with the capability to filter some packet content, such as Layer 3 and sometimes Layer 4 information .Packet filtering firewalls are usually part of a router firewall, which permits or denies traffic based on Layer 3 and Layer 4 information. They are stateless firewalls that use a simple policy table look-up that filters traffic based on specific criteria.
Advantages and DisadvantagesThere are several advantages of using a packet filtering firewall:
- Packet filters implement simple permit or deny rule sets.
- Packet filters have a low impact on network performance.
- Packet filters are easy to implement, and are supported by most routers.
- Packet filters provide an initial degree of security at the network layer.
- Packet filters perform almost all the tasks of a high-end firewall at a much lower cost.
Packet filters do not represent a complete firewall solution, but they are an important element of a firewall security policy. There are several disadvantages of using a packet filtering firewall:
- Packet filters are susceptible to IP spoofing. Hackers can send arbitrary packets that meet ACL criteria and pass through the filter.
- Packet filters do not reliably filter fragmented packets. Because fragmented IP packets carry the TCP header in the first fragment and packet filters filter on TCP header information, all fragments after the first fragment are passed unconditionally. Decisions to use packet filters assume that the filter of the first fragment accurately enforces the policy.
- Packet filters use complex ACLs, which can be difficult to implement and maintain.
- Packet filters cannot dynamically filter certain services. For example, sessions that use dynamic port negotiations are difficult to filter without opening access to a whole range of ports.
- Packet filters are stateless. They examine each packet individually rather than in the context of the state of a connection.
Stateful firewall
Monitors the state of connections, whether the connection is in an initiation, data transfer, or termination state .
Application gateway firewall (proxy firewall)
Filters information at Layers 3, 4, 5, and 7 of the OSI reference model. Most of the firewall control and filtering is done in software. When a client needs to access a remote server, it connects to a proxy server. The proxy server connects to the remote server on behalf of the client. Therefore, the server only sees a connection from the proxy server.
Other methods of implementing firewalls include:
- Host-based (server and personal) firewall – A PC or server with firewall software running on it.
- Transparent firewall – Filters IP traffic between a pair of bridged interfaces.
- Hybrid firewall – A combination of the various firewall types. For example, an application inspection firewall combines a stateful firewall with an application gateway firewall.
Next generation Firewall
In August 2014, Cisco announced the integration of Sourcefire’s FirePOWER services into the Cisco Adaptive Security Appliance (ASA). Designed with advanced malware protection, the Cisco ASA with FirePOWER services is also called the Cisco ASA Next-Generation Firewall because it is an adaptive, threat-focused firewall. It is designed to provide defense across the entire attack continuum, which includes before, during, and after attacks.
A next-generation firewall goes beyond the stateful firewall in several important ways:
- Granular identification, visibility, and control of behaviors within applications
- Restricting web and web application use based on the reputation of the site
- Proactive protection against Internet threats
- Enforcement of policies based on the user, device, role, application type, and threat profile
- Performance of NAT, VPN, and stateful protocol inspection (SPI)
- Use of an integrated intrusion prevention system (IPS)
Classic Firewall
Cisco IOS Classic Firewall, formerly known as context-based access control (CBAC), is a stateful firewall feature added to the Cisco IOS prior to version 12.0.
Classic Firewall provides four main functions: traffic filtering , traffic inspection, intrusion detection, and generation of audits and alerts.
Classic Firewall can also examine supported connections for embedded NAT and Port Address Translation (PAT) information and perform the necessary address translations.
Limitation:
- Classic Firewall only provides filtering for those protocols that are specified by an administrator. If a protocol is not specified, the existing ACLs determine how that protocol is filtered and no temporary opening is created.
- Additionally, Classic Firewall only detects and protects against attacks that travel through the firewall. It does not typically protect against attacks originating from within the protected network unless that traffic travels through an internal router with the Cisco IOS Firewall enabled.
The strategic development direction for Cisco IOS Software’s stateful inspection firewall is carried by the Zone-Based Policy Firewall (ZPF).
Operation
Classic Firewall creates temporary openings in the ACL to allow returning traffic. These entries are created as inspected traffic leaves the network and are removed when the connection terminates or the idle timeout period for the connection is reached.Multistep operation that will create a temporary opening in the firewall :
1. When traffic is first generated, and it passes through the router, the inbound ACL is processed. If the ACL denies this type of connection, the packet is dropped. If the ACL permits the connection, the Classic Firewall inspection rules are examined.
2. Based on the inspection rules for Classic Firewall, the Cisco IOS software might inspect the connection. If SSH traffic is not inspected the packet is allowed through, and no other information is gathered. Otherwise, the connection goes to the next step.
3. The connection information is compared to entries in the state table. If the connection does not currently exist, the entry is added. If it does exist, the idle timer for the connection is reset.
4. If a new entry is added, a dynamic ACL entry is added to allow the returning SSH traffic that is part of the same SSH connection. This temporary opening is only active for as long as the session is open. These dynamic ACL entries are not saved to NVRAM.
5. When the session terminates, the dynamic information from the state table and the dynamic ACL entry are removed.
Classic Firewall Configuration
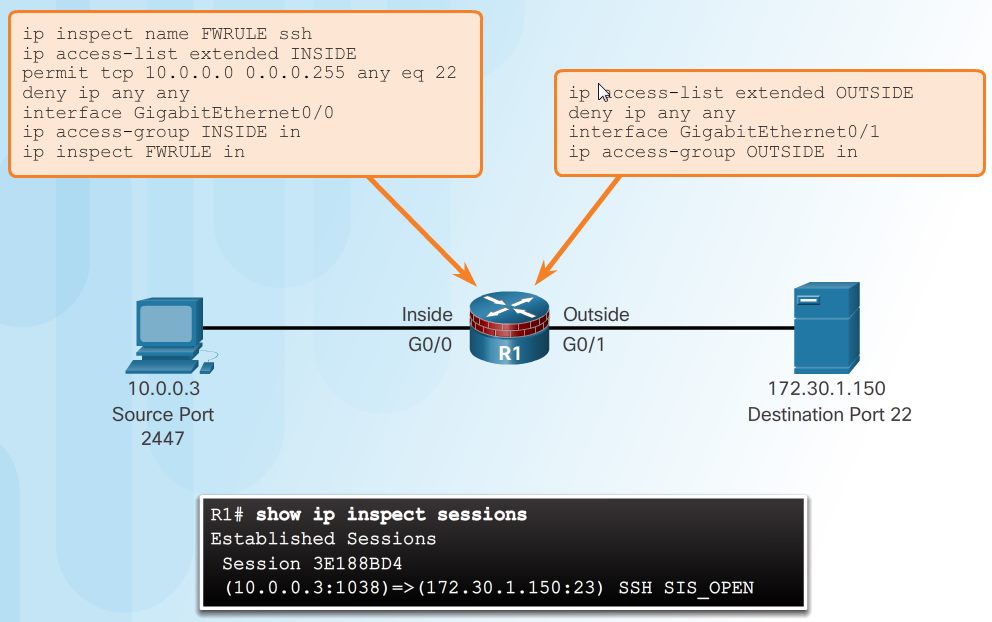
Consider the topology shown in the figure. The administrator wants to allow SSH sessions between the 10.0.0.0 and 172.30.0.0 networks. However, only hosts from the 10.0.0.0 network are allowed to initiate SSH sessions. All other access is denied. There are four steps to configure this policy using a Classic Firewall.
Step 1. Choose the internal and external interfaces.
Step 2. Configure ACLs for each interface.
Step 3. Define inspection rules.
Step 4. Apply an inspection rule to an interface.
Example
1. In this example, G0/0 is the inside interface and G0/1 is the outside interface.
2. The INSIDE ACL allows only SSH traffic from the 10.0.0.0 network. It is applied to the G0/0 interface. Until the inspection rule is configured, the OUTSIDE ACL will deny inbound traffic from the 172.30.0.0 network. It is applied to the G0/1 interface.
3. The inspection rule FWRULE specifies that traffic will be inspected for SSH connections. This inspection rule has no effect until it is applied to an interface. Although an SSH connection would be allowed in the G0/0 interface and out to host on the 172.30.0.0 network, returning SSH traffic inbound to G0/1 would still be denied.
4. When the FWRULE is applied to inbound traffic on the G0/0 interface, the Classic Firewall configuration will dynamically add an entry to allow inbound SSH traffic between the two hosts. This can be verified with the show ip inspect sessions command.
Private and public networks
Typically a firewall with two interfaces is configured as follows:
- Traffic originating from the private network is permitted and inspected as it travels toward the public network. Inspected traffic returning from the public network and associated with traffic that originated from the private network is permitted.
- Traffic originating from the public network and traveling to the private network is generally blocked.
Demilitarized zones (DMZ)
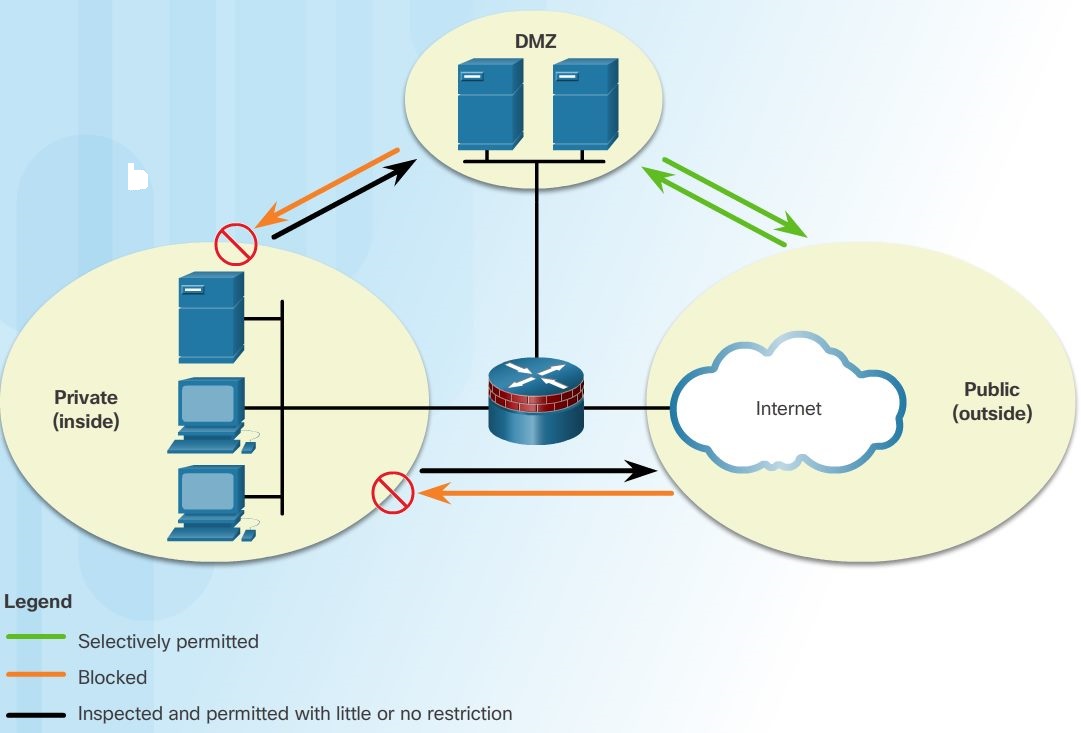
A demilitarized zone (DMZ) is a firewall design where there is typically one inside interface connected to the private network, one outside interface connected to the public network, and one DMZ interface, as shown in the figure.
- Traffic originating from the private network is inspected as it travels toward the public or DMZ network. This traffic is permitted with little or no restriction. Inspected traffic returning from the DMZ or public network to the private network is permitted.
- Traffic originating from the DMZ network and traveling to the private network is usually blocked.
- Traffic originating from the DMZ network and traveling to the public network is selectively permitted based on service requirements.
- Traffic originating from the public network and traveling toward the DMZ is selectively permitted and inspected. This type of traffic is typically email, DNS, HTTP, or HTTPS traffic. Return traffic from the DMZ to the public network is dynamically permitted.
- Traffic originating from the public network and traveling to the private network is blocked.