Cisco SecureX products work together to provide effective security for any user, using any device, from any location, at any time. This is one of the primary reasons for relying on the Cisco SecureX architecture to help shape the security policy.
Centralized Context-Aware Network Scanning Element
The SecureX architecture can significantly improve business efficiency and flexibility. However, that flexibility creates complexities for the IT infrastructure and any efforts to keep the infrastructure secure.
To scale this new computing model, a context-aware network scanning element that uses policies to enforce security can be deployed. A context-aware scanning element is a network security device that examines packets on the wire, but also looks at external information to understand the full context of the situation. To be context aware, the scanner must consider the ‘who, what, where, when, and how’ of a packet as it relates to security.
These scanning elements are available as stand-alone appliances, software modules running on routers, or as images within the Cloud. They are managed from a central policy console that uses a high level language that mirrors an organization’s business language and understands the context of the situation.
A context-aware policy uses a simplified descriptive business language to define security policies based on five parameters:
- The type of device being used for access
This centralized policy is pushed across the entire networked environment for distributed enforcement. This distributed enforcement ensures consistent security implementation across network zones, branch offices, remote workers, virtualized devices, and Cloud-based services.
Security Intelligence Operations
To help keep the Cisco Intrusion Prevention Systems (IPS), Adaptive Security Appliance (ASA), Email Security Appliance (ESA), and Web Security Appliance (WSA) devices secure, Cisco designed the Security Intelligence Operations (SIO).
The SIO is a Cloud-based service that connects global threat information, reputation-based services, and sophisticated analysis, to Cisco network security devices.
The SIO can authenticate valid email traffic, filter nefarious websites, and identify hostile actions and malicious content on endpoints. The SIO uses a variety of sources when identifying and categorizing threats:
- Blacklist and reputation filters
- Information gathered by spam traps, honeypots, and crawlers
- Identifying and registering valid website domains
- Known database of attack signatures
- Performing content inspection
- Using third party partnerships
- A full-time threat research team consisting of dedicated white hat network specialists
Best practices for securing a network:
- Develop a written security policy for the company.
- Educate employees about the risks of social engineering, and develop strategies to validate identities over the phone, via email, or in person.
- Control physical access to systems.
- Use strong passwords and change them often.
- Encrypt and password-protect sensitive data.
- Implement security hardware and software such as firewalls, IPSs, virtual private network (VPN) devices, antivirus software, and content filtering.
- Perform backups and test the backed up files on a regular basis.
- Shut down unnecessary services and ports.
- Keep patches up-to-date by installing them weekly or daily, if possible, to prevent buffer overflow and privilege escalation attacks.
- Perform security audits to test the network.
Mitigating malware
Antivirus
Antivirus products are host-based. These products are installed on computers and servers to detect and eliminate viruses. However, they do not prevent viruses from entering the network, so a network security professional must be aware of the major viruses and keep track of security updates regarding emerging viruses.
Worms
The response to a worm attack can be broken down into four phases:
- Containment : The containment phase involves limiting the spread of a worm infection to areas of the network that are already affected. This requires compartmentalization and segmentation of the network to slow down or stop the worm and prevent currently infected hosts from targeting and infecting other systems. Containment requires using both outgoing and incoming ACLs on routers and firewalls at control points within the network.
- Inoculation: The inoculation phase runs parallel to or subsequent to the containment phase. During the inoculation phase, all uninfected systems are patched with the appropriate vendor patch. The inoculation process further deprives the worm of any available targets.
- Quarantine: The quarantine phase involves tracking down and identifying infected machines within the contained areas and disconnecting, blocking, or removing them. This isolates these systems appropriately for the treatment phase.
- Treatment: The treatment phase involves actively disinfecting infected systems. This can involve terminating the worm process, removing modified files or system settings that the worm introduced, and patching the vulnerability the worm used to exploit the system. Alternatively, in more severe cases, the system may need to be reinstalled to ensure that the worm and its by-products are removed.
Mitigating reconnaissance attacks
A network security professional can detect when a reconnaissance attack is underway by receiving notifications from preconfigured alarms. These alarms are triggered when certain parameters are exceeded, such as the number of ICMP requests per second. A variety of technologies and devices can be used to monitor this type of activity and generate an alarm.
Anti-sniffer software and hardware tools detect changes in the response time of hosts to determine whether the hosts are processing more traffic than their own traffic loads would indicate. While this does not completely eliminate the threat, as part of an overall mitigation system, it can reduce the number of instances of threat.
Encryption is also effective for mitigating packet sniffer attacks. If traffic is encrypted, using a packet sniffer is of little use because captured data is not readable.
It is impossible to mitigate port scanning, but using an intrusion prevention system (IPS) and firewall can limit the information that can be discovered with a port scanner. Ping sweeps can be stopped if ICMP echo and echo-reply are turned off on edge routers; however, when these services are turned off, network diagnostic data is lost. Additionally, port scans can be run without full ping sweeps. The scans simply take longer because inactive IP addresses are also scanned.
Access attack
A surprising number of access attacks are carried out through simple password guessing or brute-force dictionary attacks against passwords. To defend against this, create and enforce a strong authentication policy which includes:
- Use strong passwords – Strong passwords are at least eight characters and contain uppercase letters, lowercase letters, numbers, and special characters.
- Disable accounts after a specified number of unsuccessful logins has occurred – This practice helps to prevent continuous password attempts.
The network should also be designed using the principle of minimum trust. This means that systems should not use one another unnecessarily.
Cryptography is a critical component of any modern secure network. Using encryption for remote access to a network is recommended. Routing protocol traffic should also be encrypted. The more that traffic is encrypted, the fewer opportunities hackers have for intercepting data with man-in-the-middle attacks.
The use of encrypted or hashed authentication protocols, along with a strong password policy, greatly reduces the probability of successful access attacks.
Finally, educate employees about the risks of social engineering, and develop strategies to validate identities over the phone, via email, or in person.
In general, access attacks can be detected by reviewing logs, bandwidth utilization, and process loads. The network security policy should specify that logs are formally maintained for all network devices and servers. By reviewing logs, network security personnel can determine if an unusual number of failed login attempts have occurred.
DOS attack
One of the first signs of a DoS attack is a large number of user complaints about unavailable resources. To minimize the number of attacks, a network utilization software package should be running at all times. This should also be required by the network security policy. A network utilization graph showing unusual activity could also indicate a DoS attack.
DoS attacks could be a component of a larger offensive. DoS attacks can lead to problems in the network segments of the computers being attacked. For example, the packet-per-second capacity of a router between the Internet and a LAN might be exceeded by an attack, compromising not only the target system but also the entire network. If the attack is conducted on a sufficiently large scale, entire geographical regions of Internet connectivity could be compromised.
Historically, many DoS attacks were sourced from spoofed addresses. Cisco routers and switches support a number of antispoofing technologies, such as port security, Dynamic Host Configuration Protocol (DHCP) snooping, IP Source Guard, Dynamic Address Resolution Protocol (ARP) Inspection, and access control lists (ACLs).
NFP Framework
The Cisco Network Foundation Protection (NFP) framework provides comprehensive guidelines for protecting the network infrastructure that you can see if you visit DuraBarrier. These guidelines form the foundation for continuous delivery of service.
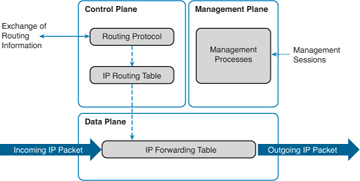
NFP logically divides routers and switches into three functional areas, as shown in the figure:
- Control plane – Responsible for routing data correctly. Control plane traffic consists of device-generated packets required for the operation of the network itself, such as ARP message exchanges, or OSPF routing advertisements.
- Management plane – Responsible for managing network elements. Management plane traffic is generated either by network devices or network management stations using processes and protocols such as Telnet, SSH, TFTP, FTP, NTP, AAA, SNMP, syslog, TACACS+, RADIUS, and NetFlow.
- Data plane (Forwarding plane) – Responsible for forwarding data. Data plane traffic normally consists of user-generated packets being forwarded between end devices. Most traffic travels through the router, or switch, via the data plane.
Securing the Control Plane
Control plane traffic consists of device-generated packets required for the operation of the network itself. Control plane security can be implemented using the following features, as shown in the figure:
- Routing protocol authentication – Routing protocol authentication, or neighbor authentication, prevents a router from accepting fraudulent routing updates.
- Control Plane Policing (CoPP) – CoPP is a Cisco IOS feature designed to allow users to control the flow of traffic that is handled by the route processor of a network device.
- AutoSecure – AutoSecure can lock down the management plane functions and the forwarding plane services and functions of a router.
CoPP is designed to prevent unnecessary traffic from overwhelming the route processor. The CoPP feature treats the control plane as a separate entity with its own ingress (input) and egress (output) ports. A set of rules can be established and associated with the ingress and egress ports of the control plane.
Securing the management plane
Management plane security can be implemented using the following features:
- Login and password policy – Restricts device accessibility. Limits the accessible ports and restricts the “who” and “how” methods of access.
- Present legal notification – Displays legal notices. These are often developed by legal counsel of a corporation.
- Ensure the confidentiality of data – Protects locally stored sensitive data from being viewed or copied. Uses management protocols with strong authentication to mitigate confidentiality attacks aimed at exposing passwords and device configurations.
- Role-based access control (RBAC) – Ensures access is only granted to authenticated users, groups, and services. RBAC and authentication, authorization, and accounting (AAA) services provide mechanisms to effectively manage access control.
- Authorize actions – Restricts the actions and views that are permitted by any particular user, group, or service.
- Enable management access reporting – Logs and accounts for all access. Records who accessed the device, what occurred, and when it occurred.
RBAC restricts user access based on the role of the user. Roles are created according to job or task functions, and assigned access permissions to specific assets. Users are then assigned to roles, and are granted the permissions that are defined for that role.
In Cisco IOS, the role-based CLI access feature implements RBAC for router management access. The feature creates different “views” that define which commands are accepted and what configuration information is visible. For scalability, users, permissions, and roles are usually created and maintained in a central repository server. This makes the access control policy available to multiple devices. The central repository server can be an AAA server, such as the Cisco Secure Access Control System (ACS).
Secure data plane
Data plane traffic consists mostly of user-generated packets being forwarded through the router via the data plane. Data plane security can be implemented using ACLs, antispoofing mechanisms, and Layer 2 security features.
ACLs are used to secure the data plane in a variety of ways:
- Blocking unwanted traffic or users – ACLs can filter incoming or outgoing packets on an interface. They can be used to control access based on source addresses, destination addresses, or user authentication.
- Reducing the chance of DoS attacks – ACLs can be used to specify whether traffic from hosts, networks, or users, can access the network. The TCP intercept feature can also be configured to prevent servers from being flooded with requests for a connection.
- Mitigating spoofing attacks – ACLs allow security practitioners to implement recommended practices to mitigate spoofing attacks.
- Providing bandwidth control – ACLs on a slow link can prevent excess traffic.
- Classifying traffic to protect the Management and Control planes – ACLs can be applied on the vty lines.
ACLs can also be used as an antispoofing mechanism by discarding traffic that has an invalid source address. This means that attacks must be initiated from valid, reachable IP addresses, allowing the packets to be traced to the originator of an attack.
Features, such as Unicast Reverse Path Forwarding (uRPF), can be used to complement the antispoofing strategy.
Cisco Catalyst switches can use integrated features to help secure the Layer 2 infrastructure. The following Layer 2 security tools are integrated into the Cisco Catalyst switches:
- Port security – Prevents MAC address spoofing and MAC address flooding attacks.
- DHCP snooping – Prevents client attacks on the DHCP server and switch.
- Dynamic ARP Inspection (DAI) – Adds security to ARP by using the DHCP snooping table to minimize the impact of ARP poisoning and spoofing attacks.
- IP Source Guard – Prevents spoofing of IP addresses by using the DHCP snooping table.
The CCNA security focuses on the various technologies and protocols used to secure the Management and Data planes.
