Cisco AutoSecure
Released in IOS version 12.3, Cisco AutoSecure is a feature that is initiated from the CLI and executes a script. AutoSecure first makes recommendations for fixing security vulnerabilities and then modifies the security configuration of the router, as shown in the figure.
AutoSecure can lock down the management plane functions and the forwarding plane services and functions of a router. There are several management plane services and functions:
- Secure BOOTP, CDP, FTP, TFTP, PAD, UDP, and TCP small servers, MOP, ICMP (redirects, mask-replies), IP source routing, Finger, password encryption, TCP keepalives, gratuitous ARP, proxy ARP, and directed broadcast
- Legal notification using a banner
- Secure password and login functions
- Secure NTP
- Secure SSH access
- TCP intercept services
There are three forwarding plane services and functions that AutoSecure enables:
- Cisco Express Forwarding (CEF)
- Traffic filtering with ACLs
- Cisco IOS firewall inspection for common protocols
AutoSecure is often used in the field to provide a baseline security policy on a new router.
Using the Cisco AutoSecure Feature
Use the auto secure command to enable the Cisco AutoSecure feature setup. This setup can be interactive or non-interactive.
Router# Auto secure [no-interact | full] [forwarding | management] [ntp | login | ssh | firewall | tcp-intercept]
•![]() no-interact—The user will not be prompted for any interactive configurations.
no-interact—The user will not be prompted for any interactive configurations.
•![]() full—The user will be prompted for all interactive questions. This is the default.
full—The user will be prompted for all interactive questions. This is the default.
• management—Only the management plane will be secured.
•![]() forwarding—Only the forwarding plane will be secured.
forwarding—Only the forwarding plane will be secured.
•![]() NTP—Without authentication or access control, Network Time Protocol (NTP) is insecure and can be used by an attacker to send NTP packets to crash or overload the switch.
NTP—Without authentication or access control, Network Time Protocol (NTP) is insecure and can be used by an attacker to send NTP packets to crash or overload the switch.
• login- specifies the configuration of the login feature in the Autosecure CLI.
When the auto secure command is initiated, a CLI wizard steps the administrator through the configuration of the device. User input is required.The auto secure command is entered. The router displays the AutoSecure configuration wizard welcome message
Secure the control plane
Routing Protocol Spoofing
Routing systems can be attacked by disrupting peer network routers, or by falsifying or spoofing the information carried within the routing protocols. Spoofing routing information may generally be used to cause systems to misinform (lie to) each other, cause a DoS attack, or cause traffic to follow a path it would not normally follow.
There are several consequences of routing information being spoofed:
- Redirecting traffic to create routing loops
- Redirecting traffic so it can be monitored on an insecure link
- Redirecting traffic to discard it.
Enable OSPF MD5 authentication globally:
ip ospf message-digest-key key md5 passwordinterface configuration command.
area area-id authentication message-digestrouter configuration command.
For more info, check http://frankfu.click/networking/cisco/single-area-ospf-configuration/2/
OSPF SHA Routing Protocol Authentication
MD5 is now considered vulnerable to attacks and should only be used when stronger authentication is not available. Cisco IOS release 15.4(1)T added support for OSPF SHA authentication, as detailed in RFC 5709. Therefore, the administrator should use SHA authentication as long as all of the router operating systems support OSPF SHA authentication.
OSPF SHA authentication includes two major steps.
Step 1. Specify an authentication key chain in global configuration mode:
- Configure a key chain name with the
key chaincommand.
- Assign the key chain a number and a password with the key and key-string commands.
- Specify SHA authentication with the cryptographic-algorithm command.
- (Optional) Specify when this key will expire with the send-lifetime command.
Syntax:
Router(config)# key chain name
Router(config-keychain)# key key-id
Router(config-keychain-key)#key-string string
Router(config-keychain-key)#cryptographic-algorithm hmac-sha-256
Router(config)# send-lifetime start-time {infinite | end-time | duration seconds}
Step 2. Assign the authentication key to the desired interfaces with the ip ospf authentication key-chain command.
Syntax:
Router(config)# interface type number
Router(config-if)# ip ospf authentication key-chain name
Network device operation
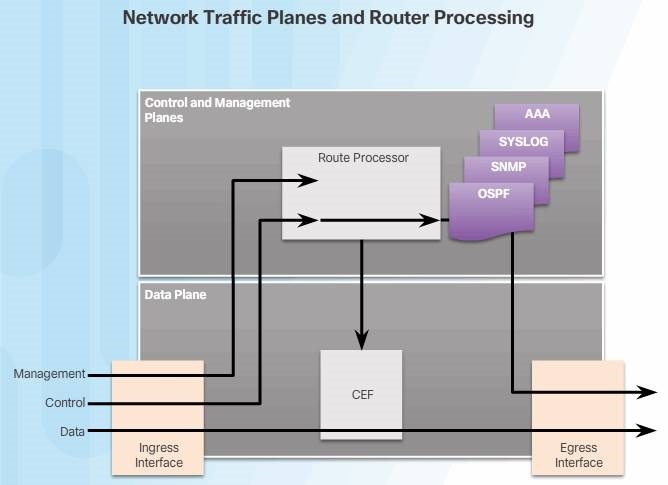
While the primary function of routers is to forward user-generated content across the data plane, routers also generate and receive traffic destined for the control and management planes. Therefore, routers must be able to distinguish between data plane, control plane, and management plane packets to treat each packet appropriately, as shown in the figure.
- Data plane packets – User-generated packets that are always forwarded by network devices to other end-station devices. From the perspective of the network device, data plane packets always have a transit destination IP address and can be handled by normal destination IP address-based forwarding processes.
- Control plane packets – Network device generated or received packets that are used for the creation and operation of the network. Examples include protocols, such as OSPF, ARP, Border Gateway Protocol (BGP), and other protocols that keep the network converged and operating properly. Control plane packets are generally packets sent to the router or network device. The destination IP address is that of the router.
- Management plane packets – Network device generated or received packets that are used to manage the network. Examples include protocols, such as Telnet, SSH, SNMP, NTP, and other protocols used to manage the device or network.
Under normal network operating conditions, the vast majority of packets handled by network devices are data plane packets. These packets are handled by Cisco Express Forwarding (CEF). CEF uses the control plane to pre-populate the CEF Forwarding Information Base (FIB) table in the data plane with the appropriate egress interface for a given packet flow. Subsequent packets that flow between that same source and destination are forwarded by the data plane based on the information contained in the FIB.
Control and Management Plane Vulnerabilities
The router processor (the CPU in the control plane) is significantly less capable of handling the kinds of packet rates experienced by CEF, and therefore, it is never directly involved in the forwarding of data plane packets.
In contrast, when high packet rates overload the control or management plane, route processor resources can be overwhelmed. This reduces the availability of these resources for tasks critical to the operation and maintenance of the network. Malicious and non-malicious events can overwhelm route processor resources. Malicious events include crafted packet attacks or simply high rates of packets directed at the control plane. Non-malicious events may result from router or network misconfigurations, software bugs, or network failure re-convergence events. It is important to take appropriate steps to protect the route processor from being overwhelmed, whether by malicious or non-malicious events.
An interface ACL is the traditional and most generally available approach for managing all packets entering or exiting a network device. ACLs are well understood and are generally applicable to data, services, control, and management plane packets. As shown in the figure, ACLs are applied at the interface level to each packet ingressing (or egressing) the interface, not just control plane packets. In addition, ACLs must be applied to every interface to which the policy is to be applied.
CoPP operation
Control Plane Policing (CoPP) is a Cisco IOS feature designed to allow administrators to manage the flow of traffic that is “punted” to the route processor. The term “punt” is defined by Cisco to describe the action an interface takes when sending a packet to the route processor.
CoPP is designed to prevent unnecessary traffic from overwhelming the route processor that, if left unabated, could affect system performance.
CoPP protects the route processor on network devices by treating route processor resources as a separate entity with its own interface. Consequently, a CoPP policy can be developed and applied to only those packets within the control plane.