Enumeration can best be defined as the process of counting.The purpose of this type of effort is to map the network and systems to find ways to further exploit it or set up a plan of attack. The overall goal is to reduce the amount of information available to attackers who attempt enumeration for malicious purpose.
There are multiple kinds of enumeration:
- Router and firewall enumeration
- Microsoft Windows enumeration
- Linux enumeration
- Application enumeration
- Advanced enumeration
Router And Firewall Enumeration
Many routing protocols are proprietary. As an example, Cisco routers and switches use the Cisco Discovery Protocol (CDP). CDP is an OSI Layer 2 protocol that helps a network professional to manage a network. CDP sends updates every 60 seconds to a multicast address. It runs on all media that supports Subnetwork Access Protocol (SNAP), including LAN and WAN technologies, such as Frame Relay and ATM.
Routing protocols
RIP: three versions of RIP: 1, 2, and RIPng for IPv6.
From a security perspective, RIP can be very problematic as it is not a sophisticated or high-security routing protocol. RIP updates; they are sent as User Datagram Protocol (UDP) datagrams to and from port 520.
So, you can emulate an attacker’s inquiry by performing a port scan to detect its presence:
nmap -v -sU -p 520
OSPF: The most common OSPF traffi c you will find is the OSPF HELLO packets. These are normally sent out about once every 30 seconds.
TFTP
Routers can use a relatively insecure protocol known as Trivial File Transfer Protocol (TFTP). TFTP can be used to hold router configurations. The TFTP server gives the router a place to put backup configurations or a place from which to pull a configuration if it needs to be rebuilt. The risk is that others may also be able to access the router configuration files.
Firewall Enumeration
There are a few ways to identify and enumerate firewalls:
■ Port scanning
■ Banner grabbing
■ Firewalking
Port scanning is a simple way to attempt to enumerate the type of firewall an organization is using. Many fi rewalls have specifi c ports; knowledge of this can help you identify the firewall type. Here are several examples:
■ Microsoft Proxy Server—Ports 1080 and 1745
■ Check Point Firewall-1—Ports 256, 257, and 258
■ Check Point NG— Ports 18210, 18211, 18186, 18190, and 18191
■ WatchGuard Firewall —Port 4100
The second type, banner grabbing, is the most well-known method of enumeration.
This method can generate a wealth of information. The three main services that may provide banners include FTP, Telnet, and web services.
Windows Enumeration
To understand why, you need to know a little history. Network Basic Input/Output System (NetBIOS) is a creation of IBM. It allows applications on different systems to communicate through a LAN and has become a de facto industry standard. On LANs using NetBIOS, systems identify themselves by using a 15-character unique name. Because NetBIOS is nonroutable by default, Microsoft adapted it to run over TCP/IP. NetBIOS was used in conjunction with Server Message Block (SMB) protocol. SMB/SMB2 allows for the remote access of shared directories and files. This key feature of Windows makes file and print sharing and the Network Neighborhood possible
| PORT | PROTOCOL | SERVICE |
| 135 | TCP | MS-RPC endpoint mapper |
| 137 | UDP | NetBIOS name service |
| 138 | UDP | NetBIOS datagram service |
| 139 | TCP | NetBIOS session service |
| 445 | TCP | SMB over TCP |
Two items that Windows uses to help
If you find NetBIOS running, one of the easiest ways to exploit it is to use the built-in nbtstat command. Nbtstat connects to individual systems and serves up the NetBIOS name table from a remote system. An example is shown here:
C:\>nbtstat -a 10.0.0.108
NetBIOS Remote Machine Name
A name table is returned that provides specific hex codes and tags of unique or group . These codes identify the services running on this specific system. For example, the code of 20 unique signifies the File Service Name. Some of the more common NetBIOS name codes are shown below:
00 U Workstation Service
Computer name 00 G Domain Name
Computer name 01 U Messenger Service
Computer name 20 U File Server Service
Computer name 03 U Messenger Service
| NAME | HEX NUMBER | TYPE | USAGE |
| Computer name | 00 | U | Workstation Service |
| Computer name | 00 | G | Domain Name |
| Computer name | 01 | U | Messenger service |
| Computer name | 20 | U | File server service |
| Computer name | 03 | U | Messenger service |
Unfortunately, NetBIOS is not supported on Windows Server 2008, Windows 8, or subsequent versions of Microsoft operating systems. On older operating systems, such as XP, it can be removed by disabling the Alerter and Messenger services on individual systems.
IPC
Server Message Block (SMB) makes it possible for users to share fi les and folders; Interprocess Communication (IPC) offers a default share on Windows systems. The IPC share is used to support named pipes that programs use for interprocess (or process-to-process) communication. Because named pipes can be redirected over a network to connect local and remote systems, they also enable remote administration.
The most basic connection possible with IPC is the NULL, or anonymous, connection. You achieve this connection by executing a net command. There is an entire host of net commands. You will look at a few here, but for a more complete list, you can just type net from the command line. Then, enter the /? syntax after any of the commands that you would like more information about. Suppose, for example, that you have identified open ports 135, 139, and 445 on some targeted systems. You may want to start with the net view /domain command:
Enumeration and the IPC$ Share
Now that you have completed some basic groundwork, you can move on to enumerating user details, account information, weak passwords, and so forth. You will be exploiting IPC$ for these activities. Specifically, you need to set up a null session manually with the net command:
By default, newer operating systems such as Windows 8, Windows 10, Server 2008, and Server 2012 are not vulnerable to a null session attack.
C:\>net use \\192.168.0.100\ipc$ "" /u:""
DumpSec is a Windows-based GUI enumeration tool from SomarSoft, and is available from www.systemtools.com/somarsoft/?somarsoft.com. DumpSec enables you to connect remotely to older Windows machines and dump account details, share permissions, and user information.
Linux/Unix Enumeration
Network Time Protocol (NTP) is the first one you will look at. NTP is a protocol designed to synchronize clocks of networked computers. Networks using Kerberos or other time-based services need a time server to synchronize systems. NTP uses UDP port 123. Some basic commands that can be used to enumerate the NTP service include the following:
■ Ntpdate —Used to collect time samples
■ Ntptrace —Follows time servers back up the chain to the primary time server
■ Ntpdc —Used to query about the state of the time server
■ Ntpq —Used to monitor performance
Here are some other Linux enumeration commands:
■ Rpcclient —Using rpcclient , the attacker can enumerate usernames, for example, rpcclient $> netshareenum .
■ Showmount —Displays a list of all clients that have remotely mounted a filesystem from a specified machine in the host parameter.
■ Finger —Enumerates the user and the host. This command enables an attacker to view the user’s home directory, login time, idle times, office location, and the last time they both received and read mail. It is rarely found but is still worth a try.
■ Rpcinfo —Helps to enumerate RPC protocol. This command makes an RPC call to an RPC server and reports what it finds.
■ Enum4linux —Enumerates information from Windows and Samba systems.
The application basically acts as a wrapper around the Samba tools smbclient, rpcclient , net, and nmblookup .
SNMP
Attackers are interested in SNMP for the same reason as network managers: because SNMP can be used to manage and report on workstations, servers, routers, switches, and even intelligent hubs.
- SNMPUtil— A Windows resource kit command-line enumeration tool that can be used to query computers running SNMP
- SNScan— A free GUI-based SNMP scanner from Foundstone
- SolarWinds IP Network Browser—A GUI-based network-discovery tool that enables you to perform a detailed discovery on one device or an entire subnet. This tool is not free.
The SNMP enumeration countermeasures include turn off SNMP if not needed, block port 161 at network checkpoints and upgrade to SNMP version 3. Group Policy security option, Additional Restrictions for Anonymous Connections, which restricts SNMP connections. Finally, implementing ACL filtering allows access to your Read-Write community only from approved stations or subnets.
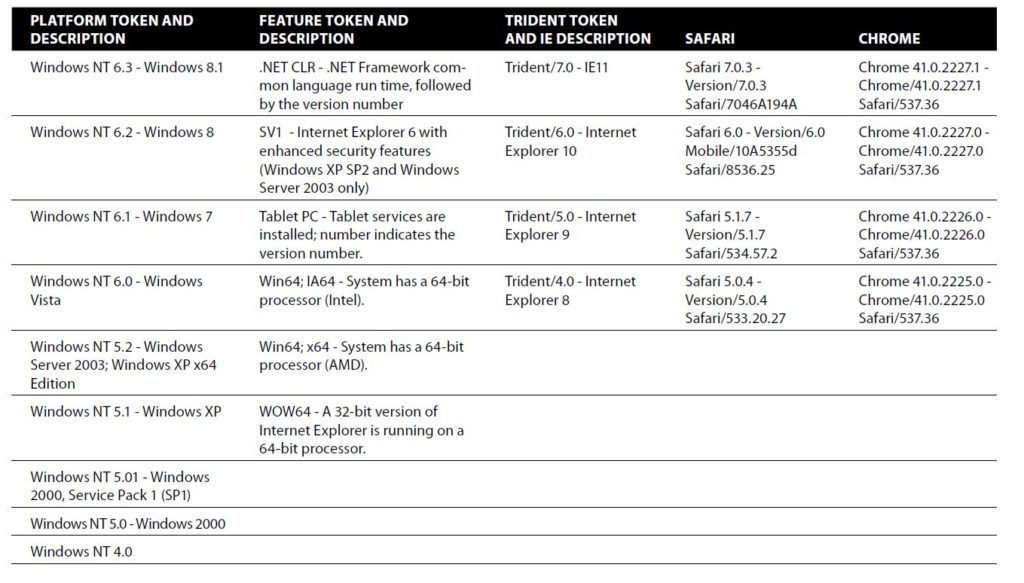
User Agent Strings
User agent strings act as another method to fingerprint a client.These characteristics range from identifying the browser to the type of OS that it is running on. The user agent string is simply a line of text that is returned whenever your browser connects to a website. The user agent string is based on the specific browser you are using and the OS that is installed on your computer.
One way to see who is tracking you is by installing Lightbeam. Lightbeam is a Firefox add-on that provides an interactive visualization that displays everyone to whom your browsing habits and data are sent.
1. Go to https://www.mozilla.org/en-US/lightbeam/ and download the Lightbeam add-on for Firefox.
2. Install Lightbeam.
3. Click the Lightbeam add-on to see a graphical representation of all the third parties your information is being forwarded to.
Fingerprinting your system
Fingerprinting looks at the characteristics of a computer to examine unique attributes such as what plug-ins and software you have installed, the size and manufacturer of the monitor, and time zone, all the way down to the serial number of your hard drive.
Fingerprinting is poised to be much more invasive than cookies ever were, as these items are not easily changed or modified.
Mapping the Attack Surface
Attack surface is The sum of the different points (the “attack vectors”) where an unauthorized user (the “attacker”) can try to enter data to or extract data from an environment.
The attacker may attempt this in the following ways:
■ Password speculation
■ Sniffi ng password hashes
■ Exploiting vulnerabilities
Password Speculation and Cracking
Windows stores usernames and passwords in the Security Accounts Manager (SAM) database. If the system is part of a domain, the domain controller stores the critical information. These hashes are stored in the local SAM database ( C:\Windows\System32\config\SAM file) or in Active Directory ( C:\Windows\NTDS\ntds.dit file on DCs).
When the systems store the passwords, Older systems use a LAN Manager hash (LM hash). This approach had several weaknesses, including a maximum length of 14 characters and the fact that the password was actually stored in two seven-character fields. NTLM is more recent, and is actually a challenge-response authentication protocol that uses three messages to authenticate a client in a connection-oriented environment. NTLM can support passwords that are up to 127 characters long.
The hash calculation remains the most common attack vector, techniques include dictionary, hybrid, and brute-force password cracking.
- Dictionary password attacks pull words from a dictionary or word list to attempt to discover a user’s password. A dictionary attack uses a predefined dictionary to look for a match between the encrypted password and the encrypted dictionary word.
- A hybrid attack also uses a dictionary or word list, but it prepends and appends characters and numbers to dictionary words in an attempt to crack the user’s password. These programs are comparatively smart because they can manipulate a word and use its variations. For example, consider the word password . A hybrid password audit would attempt variations such as 123password, abcpassword, drowssap, p@ssword, pa44w0rd, and so on.
- Brute-force attacks use random numbers and characters to crack a user’s password. A brute-force audit on an encrypted password may take hours, days, months, or years, depending on the complexity and length of the password.
Password Cracking Tools
Some better-known dictionary, hybrid, and brute-force password-cracking tools include the following:
■ John the Ripper— A well-known password-auditing tool that is available for 11 types of Unix systems as well as Windows. It can crack most common passwords, including Kerberos, AFS, and Windows NT/2000/XP/2003 LM hashes. A large number of add-on modules are available for
this tool that allow it to crack OpenVMS passwords, Windows credential caches, and MySQL passwords.
■ Cain & Abel— A multipurpose tool that can perform a variety of tasks, including Windows enumeration, sniffi ng, and password cracking. The password-cracking part of the program can perform dictionary and bruteforce analysis and can use precomputed hash tables.
■ LCP— Another program that can perform a range of password-cracking techniques
Some passwords were considered secure because of the time it would take to crack them; sure, they could be cracked, but who was going to spend three months trying? This theory no longer holds true.
Another approach is to use a rainbow table. It works by precomputing all possible passwords in advance. Upon completion of this time-consuming process, the passwords and their corresponding encrypted values are stored in a file called a rainbow table. Encrypted passwords are loaded, and a search for the password hash is performed. When a match is found, the password is revealed. Typically, this takes only a few minutes. One tool that will perform a rainbow attack is Ophcrack. This passwordcracking tool implements the rainbow table technique just discussed. It has several tables that can be downloaded, and you can search the web for others. What is most important to remember is that if a password is in the table, it will be cracked quickly. The Ophcrack website also lets you enter a hash and reveal the password in just a few seconds.
NT cracking tools
KerbCrack, a tool from www.ntsecurity.nu , can be used to attack Kerberos. It consists of two separate programs. The first program is a sniffer that listens on port 88 for Kerberos logins; the second program is used as a cracking tool to launch a dictionary or brute-force attack on the password.
Exploring a Vulnerability
Vulnerabilities are typically reported as Common Vulnerabilities and Exposures (CVEs). CVEs are weaknesses or holes in your computers and other equipment that can be exploited by hackers. When a CVE is reported, it is cataloged and named by the MITRE Corporation.
While MITRE is in the process of researching a candidate CVE, the company creates a name for the candidate. CVE can be researched at http://nvd.nist.gov/home.cfm .
Here is how the vulnerability process may be used by an attacker:
1. The attacker enumerates a system to determine which services and versions are running. For this example, suppose the attacker identifies the system as Red Hat Linux 6.1.
2. The attacker surfs the web for vulnerabilities for Red Hat Linux 6.1. Note that there are reported vulnerabilities for race conditions and the Programmable Authentication Module.
3. With several vulnerabilities discovered, the attacker now searches the web for exploit code. Packet Storm security (www.packetstormsecurity.org ) returns several matches that may work against the vulnerable site.
4. The attacker downloads the code and launches it against the vulnerable target. If it is successful, the attacker gains access. If it is unsuccessful, the attacker renews his search and tries another exploit.
Other ways that attackers gain access by means of exploit code include the following:
■ Tricking the user into executing the malicious program. E-mail is a common attack vector.
■ Copying the code to the system and scheduling it to run at a predetermined time, for example, with the AT command.
■ Exploiting interactive access to the system, for example, with Terminal Server, PC Anywhere, or the like.