In Linux we can use fail2ban to prevent brute attack based on the login failure attempt. Windows has a similar tool called IPBAN.
The tool can be downloaded from github.
Requirement
- Check your windows version, only windows 8.1 or newer, windows server 2012 or newer. Windows Server 2008 does a poor job of logging ip addresses and is end of life. Windows XP and Server 2003 are NOT supported
- Dowload .NET core 3.0 SDK: https://dotnet.microsoft.com/download/dotnet-core/thank-you/sdk-3.0.101-windows-x64-installer
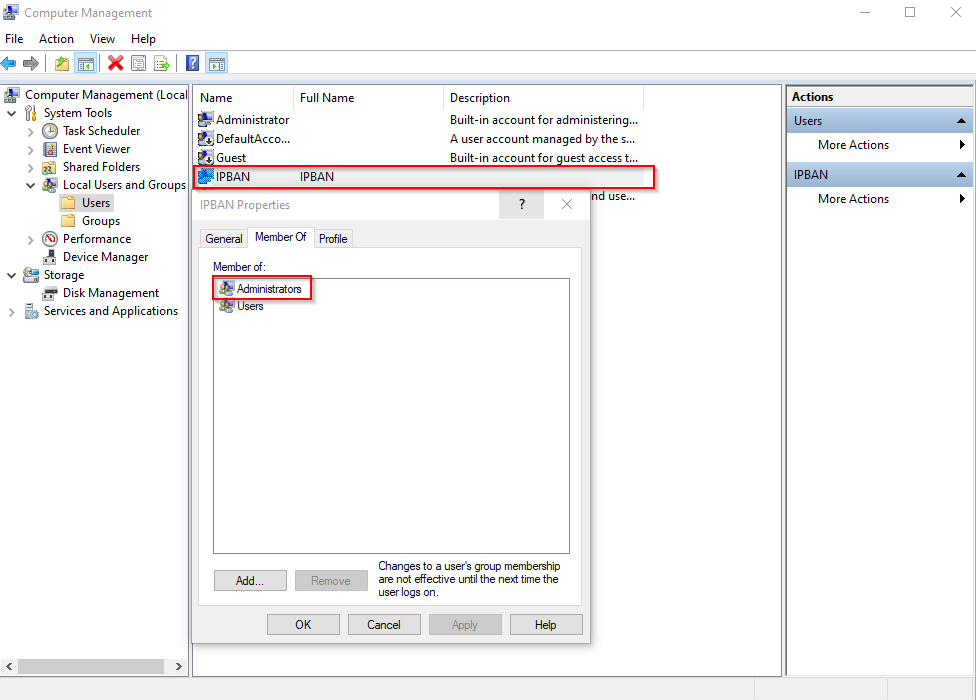
- Create a local User “IPBAN” with local Admin right.
Install
Extract the IPBan.zip (inside is IPBanWindows.zip) file to a place on your computer ( Better not under a user profile folder). Right click on all the extracted files and select properties. Make sure to select “unblock” if the option is available. You can use the [Unblock-File](https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.utility/unblock-file?view=powershell-6) utility with an **elevated** PowerShell to unblock all files in the IPBan directory:
dir C:\path\to\ipban | Unblock-File
Configure the IPBAN
Go to the folder c:\path\to\ipban, find file DigitalRuby.IPBan.dll.config and open with a text editor.
Most of the configuration is under <appSettings>
IP lockout threshold
The one I changed is the failed login attempts before banning the IP address, <add key=”FailedLoginAttemptsBeforeBan” value=”5″/>, which means if a user failed to login for 5 times, his IP will be added to the windows firewall deny list.
IP lockout duration
Duration of time <add key=”BanTime” value=”01:00:00:00″/>
The duration of time to ban an ip address (DD:HH:MM:SS) – 00:00:00:00 for max duration.
This can contain multiple time spans, separated by commas. For multiple time spans, When the previous ban time expires, the next failed login that causes a ban for the ip address will cause it to move to the next ban time. Once the last ban time has been passed, the ip address will be removed from the database and start back at the first ban time.
Reset account lockout counter
<add key=”ExpireTime” value=”00:00:05:00″/>
The duration of time to reset the failed login attempt (DD:HH:MM:SS).
Firewall rule name prefix, the rule name will be IPBan_Block_0 for the first block list:
<add key=”FirewallRulePrefix” value=”IPBan_”/>
White list
Comma separated list of ip addresses, cidr masks or dns names that are never banned. Whitelist takes precedence over blacklist. –>
<add key=”Whitelist” value=””/>
Regular expression for more advanced whitelisting. Shortcut: use * to allow any piece of an ip (i.e. 128.128.128.*).
Sample regex that whitelists a few ips: ^(128\.128\.128\.*)|(99\.99\.99\.[0-9])$
More info about regex: http://www.regular-expressions.info/
<add key=”WhitelistRegex” value=””/>
Black list
Comma separated list of ip addresses, cidr masks, dns names or user names to always ban and never unban
<add key=”Blacklist” value=””/>
Regular expression for more advanced blacklisting. Shortcut: use * to allow any piece of an ip, dns name or user name (i.e. 128.128.128.*).
Sample regex that blacklists a few ips: ^(128\.128\.128\.*)|(99\.99\.99\.[0-9])$
More info about regex: http://www.regular-expressions.info/
<add key=”BlacklistRegex” value=””/>
Configure environment
IPBAN read the logon failure record and add that IP address to the windows firewall. So you need to configure this policy:
You *MUST* make this change to the local security policy / Domain policy to ensure IP addresses show up in event viewer:
type gpedit.msc, Go to Computer configuration > Windows Settings > Security Policy -> Local Policies -> Audit Policy, and turn failure logging on for “audit account logon events” and “audit logon events”.
Or do it from an admin command prompt:
``` auditpol /set /category:"Logon/Logoff" /success:enable /failure:enable auditpol /set /category:"Account Logon" /success:enable /failure:enable ```
Disable NTLM logins
(optional) It is highly recommended to disable NTLM logins and only allow NTLM2 logins. Use secpol -> local policies -> security options -> network security restrict ntlm incoming ntlm traffic -> deny all accounts.
Create a service
First I will create a Service user account for it on the local computer, and add it to local administrators group. Give it a very complex password.
To install as a Windows service use the [sc command](https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/sc-create) and run the following in an elevated command window:
sc.exe create IPBAN type= own start= delayed-auto binPath= c:\path\to\service\DigitalRuby.IPBan.exe DisplayName= IPBAN sc.exe description IPBAN "Automatically builds firewall rules for abusive login attempts: https://github.com/DigitalRuby/IPBan"
Go to services, find the IPBAN service, go to Log On tab, tick the This Account and type .\IPBAN, then the password.
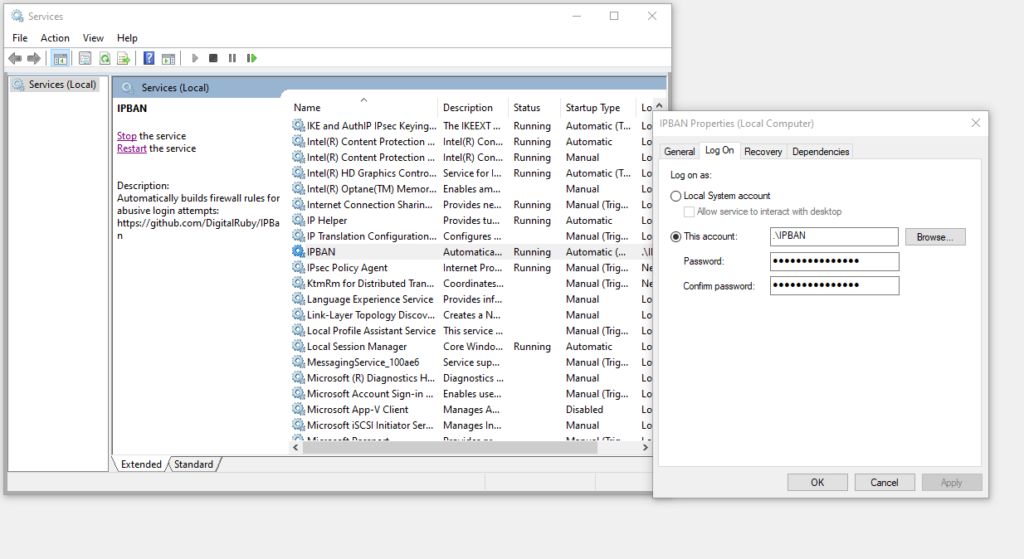
Now let’s start the service.
sc.exe start IPBAN
Do it from powershell:
or with Powershell use the command [New-Service](https://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.management/new-service) and run the following in an elevated powershell window:
Type below powershell command:
New-Service -Name "IPBAN" -BinaryPathName "c:\path\to\service\DigitalRuby.IPBan.exe" -StartupType automatic -DisplayName "IPBAN" -Description "Automatically builds firewall rules for abusive login attempts: https://github.com/DigitalRuby/IPBan" Get-WmiObject win32_service -Filter "name='IPBAN'" Start-Service IPBAN sc.exe config IPBAN start= delayed-auto
– On Windows, the service MUST be set to start as delayed automatic, otherwise the service will crash upon machine reboot.
– The service needs file system, event viewer and firewall access, so running as a privileged account is required.
– To run as a console app, simply run DigitalRuby.IPBan.exe and watch console output.
– On some Windows versions, NLA will default to on. This may lock you out of remote desktop, so turn this option off if needed.
– NLA is not supported with IPBan on Windows Server 2012 or older. You must use Windows Server 2016 or newer if you want NLA. Failed logins do not log properly with NLA on the older Windows editions, regardless of any settings, registry or group policy changes.
– On Windows Small Business Server 2011 (and probably earlier) and Windows Server running Exchange, with installed PowerShell v.2 that does not know Unblock-File command, and newer version can’t be installed (as some scripts for managing OWA stop working correctly). Easier way is to manually unblock downloaded ZIP file and then unzip content.
– On Windows Server running Exchange, it is impossible to disable NTLM (deny all clients in Security restrict ntlm incoming ntlm traffic) as then Outlook on client computers permanently asks users for entering username and password. To workaround this, set LAN Manager authenticating level in Security Optins of Local Policies to “Send NTLMv2 response only. Refuse LM & NTLM”. There is one small issue – when somebody tries to login with an undefined username, the log does not contain an IP address. Not sure why Microsoft can’t log an ip address properly.
– If using Exchange, disabling app pool ‘MSExchangeServicesAppPool’ can eliminate quite a lot of problems in the event viewer with ip addresses not being logged.
Reference
https://github.com/DigitalRuby/IPBan
Download: https://github.com/DigitalRuby/IPBan/releases