Components of Snort
A Snort-based IDS consists of the following major components:
• Packet Decoder
• Preprocessors
• Detection Engine
• Logging and Alerting System
• Output Modules
You can see the components work with each other in below way:
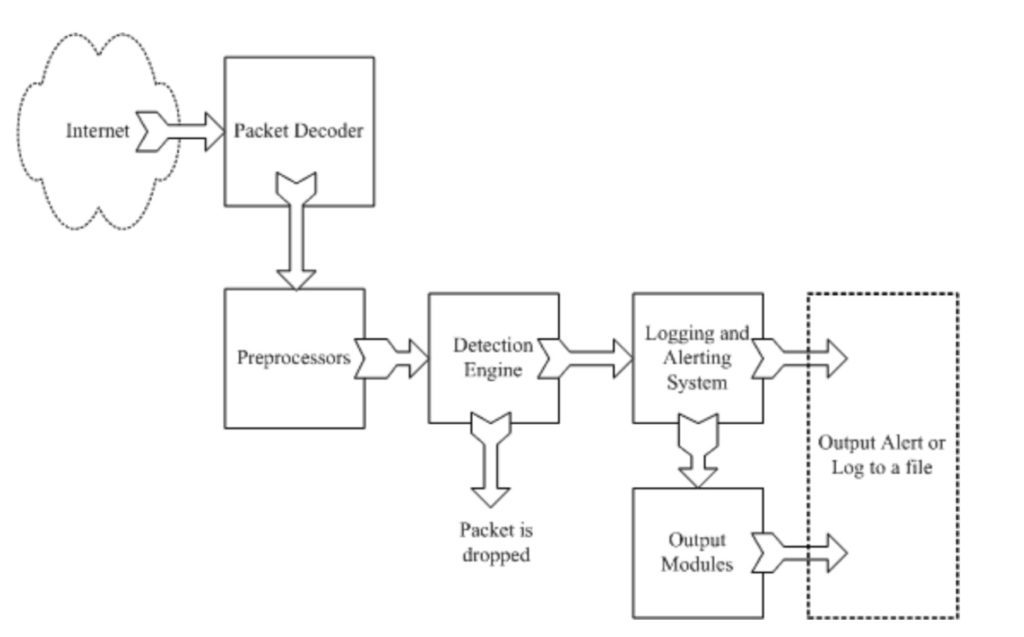
Packet Decoder
The packet decoder takes packets from different types of network interfaces and prepares the packets to be preprocessed or to be sent to the detection engine. The inter- faces may be Ethernet, SLIP, PPP and so on.
Preprocessor
Preprocessor is used to arrange or modify data packets before the detection engine does some operation to find out if the packet is being used or modified by an intruder. They can work in following ways:
- Prepare data for detection engine.
- Detect anomalies in packet headers:
- packet defragmentation: The receiving systems are capable of reassembling these smaller units again to form the original data packet.
- Decode HTTP URI. hackers can also insert in the web Uniform Resource Identifier (URI) hexadecimal characters or Unicode characters which are perfectly legal as far as the web server is concerned
Detection Engine
Detection engine is the core part of snort, its responsibility is to detect if any intrusion activity exists in a packet. The detection engine employs Snort rules for this purpose. The rules are read into internal data structures or chains where they are matched against all packets. If a packet matches any rule, appropriate action is taken; otherwise the packet is dropped.
The load on the detection engine depends upon the following factors:
• Number of rules
• Power of the machine on which Snort is running
• Speed of internal bus used in the Snort machine
• Load on the network
Note that the detection system can dissect a packet and apply rules on different parts of the packet. These parts may be:
• The IP header of the packet.
• The Transport layer header. This header includes TCP, UDP or other transport layer headers. It may also work on the ICMP header.
• The application layer level header. Application layer headers include, but are not limited to, DNS header, FTP header, SNMP header, and SMTP header. You may have to use some indirect methods for application layer headers, like offset of data to be looked for.
• Packet payload. This means that you can create a rule that is used by the detection engine to find a string inside the data that is present inside the packet.
The detection engine works in different ways for different versions of Snort.
- In all 1.x versions of Snort, the detection engine stops further processing of a packet when a rule is matched.This means that if a packet matches criteria defined in multiple rules, only the first rule is applied to the packet without looking for other matches. This is fine except for one problem. A low priority rule generates a low priority alert, even if a high priority rule meriting a high priority alert is located later in the rule chain.
- in Snort version 2 where all rules are matched against a packet before generating an alert. After matching all rules, the highest priority rule is selected to generate the alert.
Logging and Alerting system
Logs are kept in simple text files, tcp- dump-style files or some other form. All of the log files are stored under /var/log/ snort folder by default. Y ou can use –l command line options to modify the location of generating logs and alerts.
Output modules
Output modules or plug-ins can do different operations depending on how you want to save output generated by the logging and alerting system of Snort. Basically these modules control the type of output generated by the logging and alerting system.
Depending on the configuration, output modules can do things like the following:
- Simply logging to /var/log/snort/alerts file or some other file
- Sending SNMP traps
- Sending messages to syslog facility
- Logging to a database like MySQL or Oracle. You will learn more about using MySQL later in this book
- Generating eXtensible Markup Language (XML) output
- Modifying configuration on routers and firewalls.
- Sending Server Message Block (SMB) messages to Microsoft Windows-based machines
- Other tools can also be used to send alerts in other formats such as e-mail mes- sages or viewing alerts using a web interface.
Location for snort
External traffic monitoring, The best place to install Snort is right behind the firewall or router so that all of the Internet traffic is visible to Snort before it enters any switch or hub.If you have multiple paths to the Internet, you may want to place one IDS box at every entry point.
Internal traffic monitoring: However if you want to detect internal threats as well, you may want to place a box in every network segment.
Technical solution: To monitor the traffic one method is using the switch port mirroring function, you can also connect the IDS to a small HUB or a Network TAP right behind the firewall, i.e., between firewall and the switch. In this case all incoming and outgoing traffic is visible to the IDS.
How to protect snort itself
The first thing a hacker would do is turn off the IDS/IPS, so how to protect the snort itself is critical. Some recommendations are as below:
• The first thing that you can do is not to run any service on your IDS sensor itself. Network servers are the most common method of exploiting a system.
• New threats are discovered and patches are released by vendors. This is almost a continuous and non-stop process. The platform on which you are running IDS should be patched with the latest releases from your vendor.
• Configure the IDS machine so that it does not respond to ping (ICMP Echo- type) packets. such as command sysctl -w net.ipv4.icmp_echo_ignore_all=1
• If you are running Snort on a Linux machine, use netfilter/iptable to block any unwanted data. Snort will still be able to see all of the data.
• You should use IDS only for the purpose of intrusion detection. It should not be used for other activities and user accounts should not be created except those that are absolutely necessary.
Apart from these, two technic can be used to protect snort as well:
- Stealth interface(one way network cable): You can run Snort on a stealth interface which only listens to the incoming traffic but does not send any data packets out. A special cable(one way network cable) is used on the stealth interface. see this page: http://frankfu.click/security/security-labs/make-a-one-way-data-rj45-cable.html
- You can also use Snort on an interface where no IP address is assigned. Because the snort is configured to listen on a specific interface, and no IP address is required, you can use a interface with no IP address to do this job. Then use another interface with IP address from where a host can connect to the snort. On Microsoft Windows systems, you can use an interface without binding TCP/IP to the interface, in which case no IP address will be assigned to the interface. Don’t forget to disable other protocols and services on the interface as well
command
Command line options must be specified separately. “snort -de” won’t work. You can still concatenate options and their arguments, however, so “snort -Ldump” will work.
Most commonly used and useful command line options are listed below:
Options Description
-A This options sets alert mode. Alert modes are used to set different levels of detail with the alert data. Options available are fast, full, console or none.You have already seen that the console mode is used to display alert data on the console screen instead of log- ging to files. The fast mode is useful for high-speed operations of Snort.
-b This option is used to log packets intcpdumpformat. Logging is very fast and you can use the tcpdump program later on to display the data.
-c This is the most commonly used option. You specify the location of snort.conf file with this option. When specified, Snort does not look into default locations of the con- figuration file snort.conf. As an example, if the snort.conf file is present in /etc directory, you will use “-c /etc/snort.conf” on the command line while start- ing Snort.
-D This option enables Snort to run in the background. In almost all implementations of Snort, this option is used. You don’t use this option when you are testing Snort after installation.
-i This option is used to start Snort so that it listens to a particular network interface. This option is very useful when you have multiple network adapters and want to listen to only one of them. It is also useful when you want to run multiple Snort sessions on mul- tiple network interfaces. For example, if you want Snort to listen to network interface eth1 only, you will use “-i eth1” on the command line while starting Snort.
-l This option is used to set the directory where Snort logs messages. The default location is /var/log/snort. For example, if you want all log files to be generated under / snort directory, you will use “-l /snort” command line option.
-M You have to specify a text file as argument to this option. The text file contains a list of Microsoft Windows hosts to which you want to send SMB pop-up windows. Each line should contain only one IP address. Note that you can achieve the same goal through snort.conf file as well, which will be explained later.
-T This option is very useful for testing and reporting on the Snort configuration. You can use this option to find any errors in the configuration files.
Operation mode
Snort operates in two basic modes: packet sniffer mode and network intrusion detection (NIDS) mode. In sniffer mode it works similar like TCPdump or wireshark, which is not often used. In NIDS mode, it uses its rules to find out if there is any network intrusion detection activity, which will be primary purpose of using Snort.