First you need to get a copy of the configuration file, how ? Use your sniffing skills, which I will not show here.
Open the file, find something like below:
mgmtuser add encrypt testadmin 1 a9836e23b845fef2d73ac99f01dfae20 xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx 16 79f0be7ced838052b0cdfc062764c2de0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 read-write or radius auth add encrypt 1 192.168.11.21 1645 password 1 a9836e23b845fef2d73ac99f01dfae20 xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx 16 79f0be7ced838052b0cdfc062764c2de0000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
Having a closer look at those strings we see that no matter which kind of details (SNMP, MGMT-User, …), it’s using the same format:
- The encryption type after username: If encryption type is “1” (what means AES-128 CBC PKCS#7) it’s followed by a bunch of hex encoded strings, which is Init vector
- The Hex number after 16: The encrypted password in Hex.
The data we need here is :
a9836e23b845fef2d73ac99f01dfae20 < Init vector
79f0be7ced838052b0cdfc062764c2de <encrypted password, tailed with “0”, which can be just striped.
We also know there is a constant encryption key ( which is always same for AES-128 CBC PKCS#7): 834156F9940F09C0A8D00F019F850005 , Which can be googled.
Use an online tool http://aes.online-domain-tools.com to crack the password.
Put the values into the online tool, it will do the rest for you!
The password for this user is testP@ssw0rd .
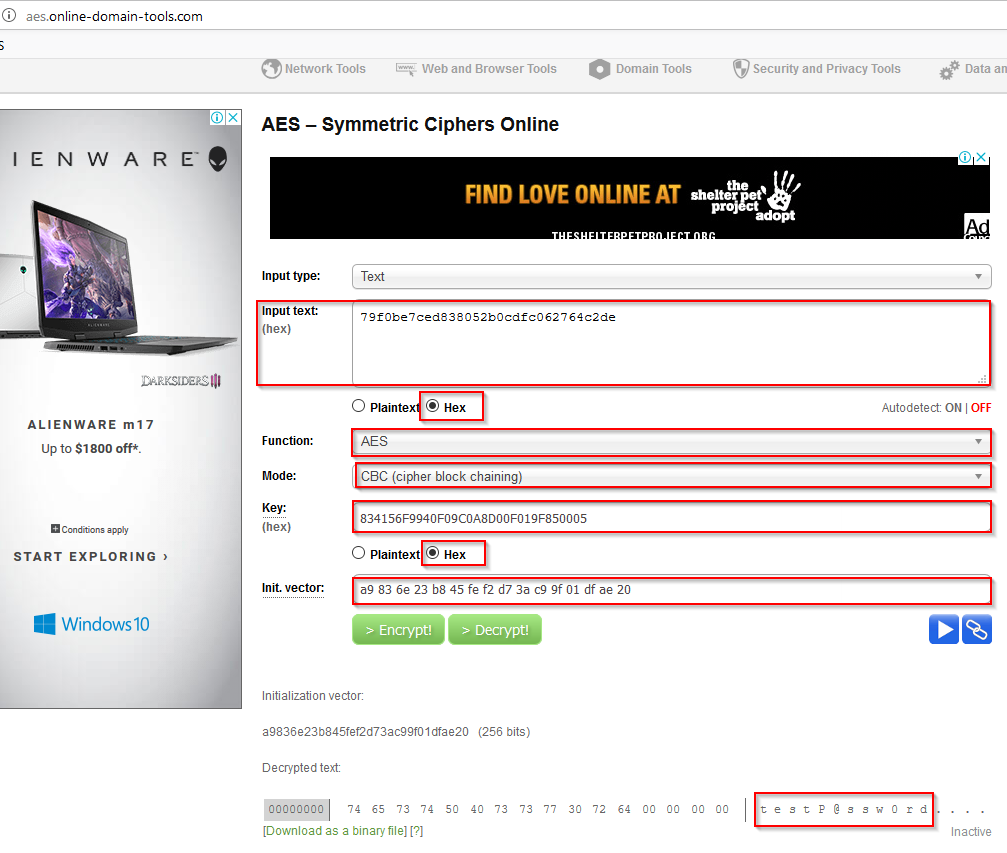
If you tick the plaintext, type testP@ssw0rd into the Input text, keep the init vector as a9836e23b845fef2d73ac99f01dfae20 , thenclick Encrypt!, it will work out the encrypted password 79f0be7ced838052b0cdfc062764c2de