ASA firewall models
The choice of ASA model depends on an organization’s requirements, such as maximum throughput, maximum connections per second, and budget.
Models for small office and SOHO:
- ASA 5505/security plus, 150Mbps throughput
- ASA 5506-x/Security Plus, 750 Mbps throughput
- ASA 5512-X /security Plus , 1Gbps
- ASA 5515-X 1.2Gbps.
Internet Edge of medium to large businesses
- ASA 5525-x, 2Gbps
- ASA5545-X, 3Gbps
- ASA 5555-X 4Gbps
Large enterprises and data centers
- ASA5585-X SSP10, 4Gbps
- ASA5585-X SSP20, 10Gbps
- ASA5585-X SSP40,20Gbps
- ASA5585-X SSP60,40Gbps
- ASA service module: 20Gbps
Advanced ASA feature:
- ASA virtualization – A single ASA can be partitioned into multiple virtual devices.
Each virtual device is called a security context. Each context is an independent device, with its own security policy, interfaces, and administrators. Multiple contexts are similar to having multiple standalone devices. Many features are supported in multiple context modes, including routing tables, firewall features, IPS, and management. Some features are not supported, including VPN and dynamic routing protocols.
- High availability with failover – two identical ASAs can be paired into an active / standby failover configuration to provide device redundancy. Both platforms must be identical in software, licensing, memory, and interfaces, including the Security Services Module (SSM).
- Identity firewall – The ASA provides optional, granular access control based on an association of IP addresses to Windows Active Directory login information. These services enhance the existing access control and security policy mechanisms by allowing users, or groups, to be specified in place of source IP addresses. Identity-based security policies can be interleaved without restriction between traditional IP address-based rules.
- Threat control and containment services – All ASA models support basic IPS features. However, advanced IPS features can only be provided by integrating special hardware modules with the ASA architecture. IPS capability is available using the Advanced Inspection and Prevention (AIP) modules. Antimalware capabilities can be deployed by integrating the Content Security and Control (CSC) module. The Cisco Advanced Inspection and Prevention Security Services Module (AIP-SSM) and Cisco Advanced Inspection and Prevention Security Services Card (AIP-SSC), deliver protection against tens of thousands of known exploits.
Review firewall:
When discussing networks connected to a firewall, there are some general terms to consider:
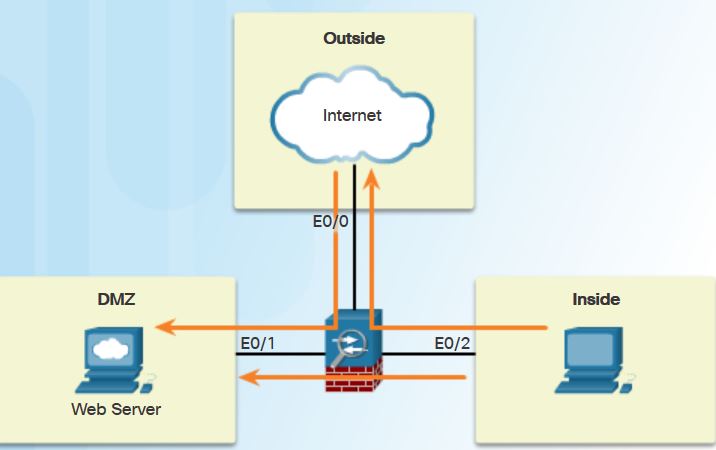
- Outside network – Network/zone that is outside the protection of the firewall
- Inside network – Network/zone that is protected and behind the firewall
- DMZ – Demilitarized zone that allows both inside and outside users access to protected network resources.
Firewalls protect inside networks from unauthorized access by users who are on an outside network. They also protect inside network users from each other.
Rules for traffic between zones:
- Traffic originating from the inside network going to the outside network is permitted.
- Traffic originating from the inside network going to the DMZ network is permitted.
- Traffic originating from the outside network going to the DMZ network is selectively permitted.
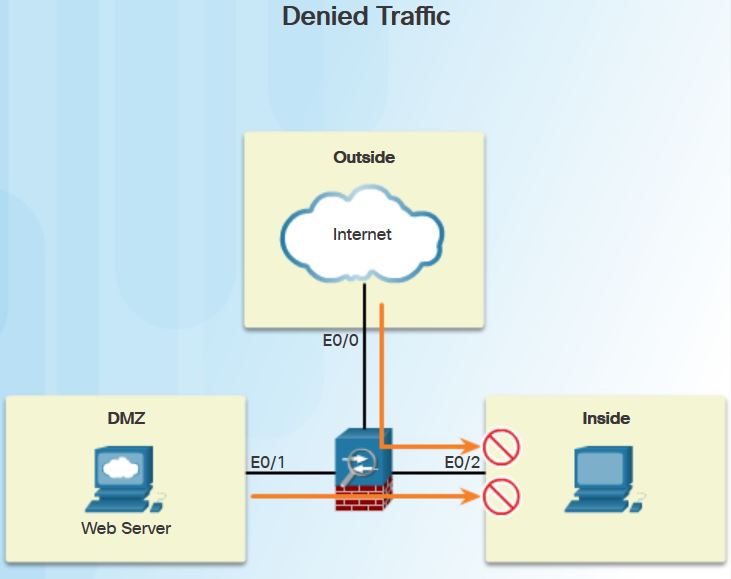
- Traffic originating from the outside network going to the inside network is denied.
- Traffic originating from the DMZ network going to the inside network is denied.
An ASA use either the Zone-Based Policy Firewall (ZPF) or by using the older context-based access control (CBAC) feature. but the configuration differs markedly from the IOS router configuration of the ZPF.
The ASA is a dedicated firewall appliance. By default, it treats a defined inside interface as the trusted network and any defined outside interfaces as untrusted networks.
Each interface has an associated security level. These security levels enable the ASA to implement security policies.
ASA Firewall Modes of Operation
There are two firewall modes of operation available on ASA devices:
- Routed Firewall Mode (default mode)- Two or more interfaces separate Layer 3 networks, i.e. domains. The ASA is considered to be a router hop in the network and can perform NAT between connected networks. Routed mode supports multiple interfaces. Each interface is on a different subnet and requires an IP address on that subnet. The ASA applies policy to flows as they transit the firewall.
- Transparent Firewall Mode – Often referred to as a “bump in the wire,” or a “stealth firewall” because the ASA functions like a Layer 2 device and is not considered a router hop.The ASA is only assigned an IP address on the local network for management purposes. This mode is useful to simplify a network configuration, or when the existing IP addressing cannot be altered. However, the drawbacks include no support for dynamic routing protocols, VPNs, QoS, or DHCP Relay.
Setting the Firewall Mode
Note We recommend that you set the firewall mode before you perform any other configuration because changing the firewall mode clears the running configuration. You are not prompted to confirm the firewall mode change; the change occurs immediately.
Prerequisites
When you change modes, the ASA clears the running configuration (see the “Guidelines and Limitations” section for more information).
•If you already have a populated configuration, be sure to back up your configuration before changing the mode.
•Use the CLI at the console port to change the mode. If you use any other type of session, including the ASDM Command Line Interface tool or SSH, you will be disconnected when the configuration is cleared, and you will have to reconnect to the ASA using the console port in any case.
Set the ASA to transparent mode:
hostname(config)# firewall transparent
To change the mode to routed, enter the command:
hostname(config)#no firewall transparent
ASA Licensing Requirements
A license specifies the options that are enabled on a given ASA. Most ASA appliances come pre-installed with either a Base license or a Security Plus license.
For example, the Cisco ASA 5505 model comes with a Base license and the option to upgrade to the Security Plus license. The Security Plus upgrade license enables the Cisco ASA 5505 to scale to support a higher connection capacity and up to 25 IPsec VPN users. It adds full DMZ support and integrates into switched network environments through VLAN trunking support. Furthermore, the Security Plus license enables support for redundant ISP connections and stateless active/standby high-availability services. This feature helps to ensure business continuity.
The permanent license is then activated by installing a permanent activation key using the activation-key command. The permanent activation key includes all licensed features in a single key. A product activation key can be purchased from a Cisco account representative.
Note: Only one permanent license key can be installed. After it is installed, it is referred to as the running license.
To verify the license information on an ASA device, use the show version command, or the show activation-key command.
ASA basic Configuration
First comes with the hardware :
Front panel:
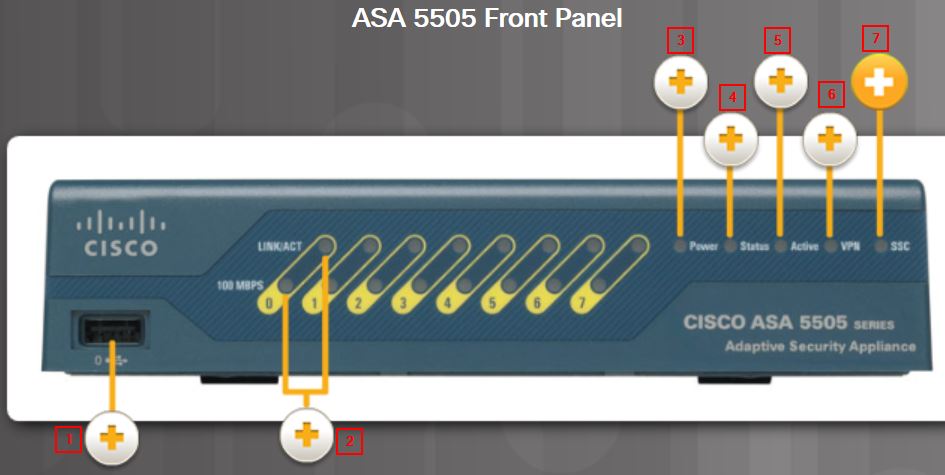
1. USB 2.0 Interface: Enables additional services and capabilities
2. Speed and Link Activity LEDs
A solid green speed indicator LED indicates 100Mb/s. If the LED is off, this indicates 10Mb/s. When the link activity indicator LED is on, it indicates that a network link is established. When it is blinking, it indicates network activity.
3. Power LED
Solid green indicates that the appliance is powered on.
4. Status LED
Flashing green indicates that the system is booting and power-up tests are running. Solid green indicates that the system tests passed and the system is operational. Solid amber indicates that the system tests have failed.
5. Active LED
Green indicates that this Cisco ASA is active.
6. VPN LED
Solid green indicate that one or more VPN tunnels are active.
7. Security Services Card (SSC) led
Solid green indicates that an SSC card is present in the SSC slot.
Back panel
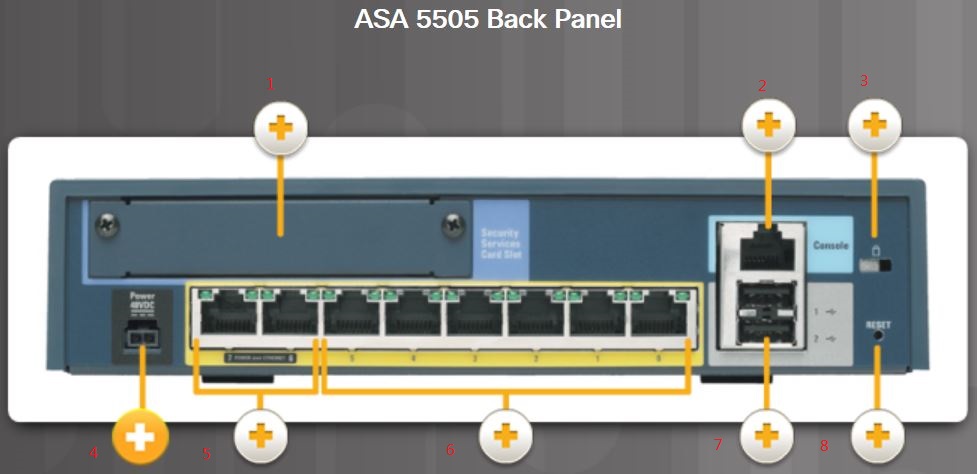
1. Security Service Card (SSC) slot
Adds the cisco advanced inspection and prevention Security Services Card (AIP-SSC). The AIP-SSC card provides intrusion prevention services to stop malicious traffic before it can affect a network.
2.Security Console Port
Initially configure the ASA
3. Lock Slot
Attach a security cable to this slot
4. Power Connector
48 VDC power.
5. Two PoE 10/100 Fast Ethernet Switch ports
These can provide Power over ethernet (PoE) ports to simplify the deployment of Cisco IP phones and external wireless access points.
6. Six 10/100 Fast Ethernet Switch Ports
These can be dynamically grouped to create up to three separate VLANs to support network segmentation and security.
7. Two USB 2.0 Ports
Enables additional services and capabilities
8. Reset button: returens to factory based configuration.
The default DRAM memory is 256 MB (upgradable to 512 MB) and the default internal flash memory is 128 MB for the Cisco ASA 5505. In a failover configuration, the two units must be identical models with the same hardware configuration, the same number and types of interfaces, and the same amount of RAM.
ASA security levels
The ASA assigns security levels to distinguish between inside and outside networks.
Security levels define the level of trustworthiness of an interface. The higher the level, the more trusted the interface. The security level numbers range from 0 (untrustworthy) to 100 (very trustworthy). Each operational interface must have a name and a security level from 0 (lowest) to 100 (highest) assigned.
- When traffic moves from an interface with a higher security level to an interface with a lower security level, it is considered outbound traffic.
- Conversely, traffic moving from an interface with a lower security level to an interface with a higher security level is considered inbound traffic.
Security Level Control:
- Network Access: By default, there is an implicit permit from a higher security interface to a lower security interface (Outbound). Hosts on the higher security interface can access hosts on a lower security interface. Multiple interfaces can be assigned the same security level. If communication is enabled for interfaces with the same security level, there is an implicit permit for traffic between the interfaces.
- Application Filtering: HTTP(S) and FTP filtering applies only for outbound connections, from a higher level to a lower level. If communication is enabled for interfaces with the same security level, traffic can be filtered in either direction.
- Inspection Engines: some application inspection engines are dependent on the security level. when interfaces have the same security level. When interfaces have the same security level, the ASA inspects traffic in either direction.
Outbound traffic is allowed and inspected by default. Returning traffic is allowed because of stateful packet inspection.
For example, internal users on the inside interface can easily access resources on the DMZ. They can also initiate connections to the Internet with no restrictions and without the need for an additional policy or additional commands. However, traffic that is coming from the outside network and going into either the DMZ or the inside network, is denied by default. Return traffic, originating on the inside network and returning via the outside interface, would be allowed.
Any exception to this default behavior requires configuration of an ACL to explicitly permit traffic from an interface with a lower security level to an interface with a higher security level, for example outside to inside.